There are numerous coding practices and server setups that can result in unexpected cached pages — pages that shouldn’t be able to be served to another user.
One of the most-abused page caching features is “search index caching” — aka using a website’s search feature to inject your own content/domains/spam into a permanently cached version of that page, so that other users who stumble across that page via Google or other means, they could see content on the search result page input by another user that would appear to have been written by the owners of the website.
And how could this be done in real life, like right now?
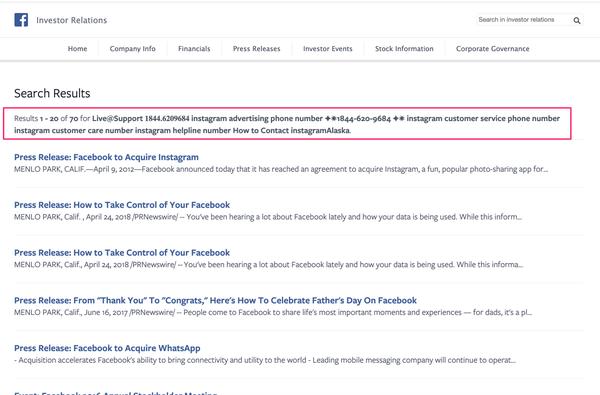
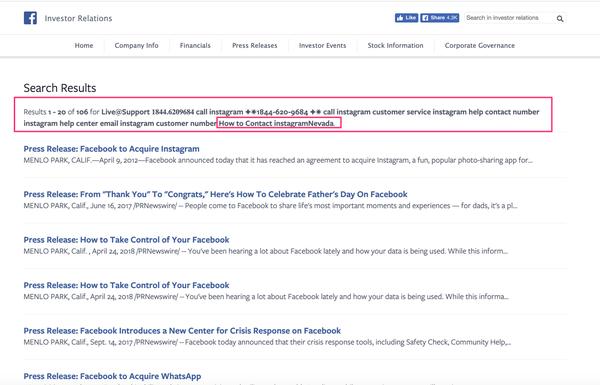
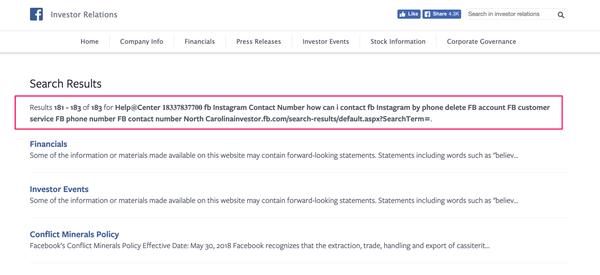
Imagine a Facebook scammer was trying to hijack Facebook and Instagram accounts and they could inject a “Facebook Customer Support phone number” they control into a search result page on a mis-configured Facebook subdomain, and then trick anyone who calls the number looking for support. That would be bad right?
Well, that’s what is happening over on Facebook’s investor portal @ https://investor.fb.com/ and even though I reported it to Facebook through the only means available (the Facebook WhiteHat program) they closed the report and seem to indicate it’s of minimal concern.
Here’s just a few screen shots of the types of messages that are being injected across the Investor.fb.Com subdomain:
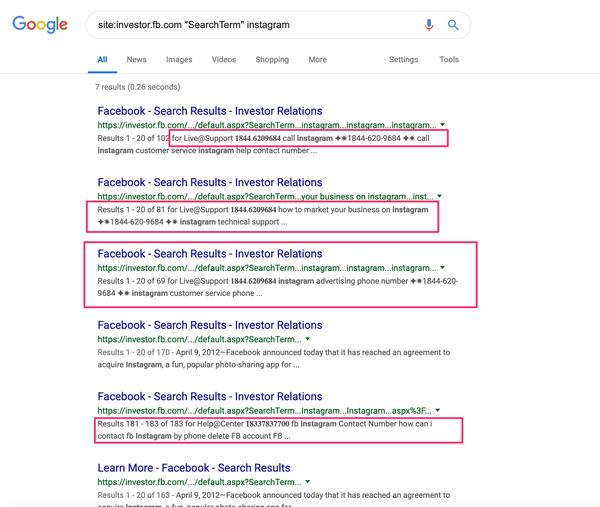
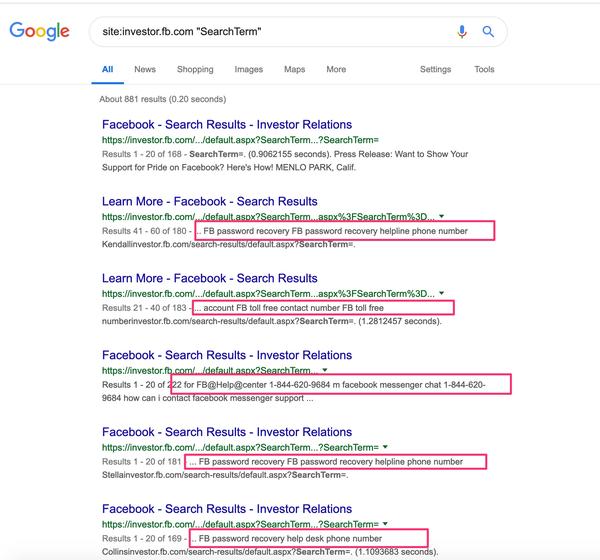
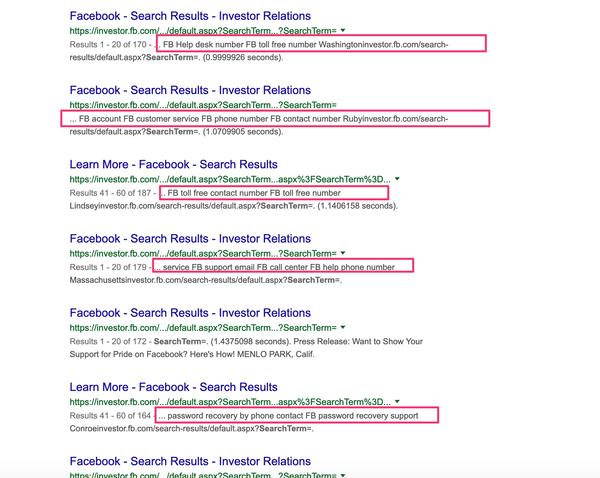
And then what does that look like for the end-user if they click any of those links?
With geographic keyword stuffing!
In my opinion, these types of user-phishing vulnerabilities created by insecure search+cache settings are not only the responsibility of the vendor who built the page (Facebook works with a niche 3rd party software vendor on this subdomain), but they are also the responsibility of the domain owner and anyone servicing clients using that subdomain.
It’s obvious that even though this is an “investor portal” the phishing phone number messages are targeting average Instagram and Facebook users — and trying to keyword stuff the cached search pages to target unique people.
I’d like to see Facebook act and remove these cached pages, change their bug bounty terms to include 3rd party software vulnerabilities that create FB user phishing vulnerabilities, and see more companies taking the security of search results pages seriously. If a user can be exploited by a feature on your website, that’s a bug.
Finally — in case you’re wondering whether I tried to call that phone number or what happens if you do — yes — I’ve tried to call that phone number a couple times a week for ~3 weeks now. The number just hangs when connecting as though the line is overwhelmed with other people calling. I never got through to get my “instagram support” …luckily…
🤖

Recent Comments