Today on Twitter, you can’t tell which YouTube embeds are actually hiding a dark secret that will share your user data to a totally random organization, which isn’t Google or Twitter, and that organization has a business model which appears to include sharing or selling user data to advertising companies.
Twitter knows about this problem, but the problem exists due to how Twitter embeds a redirected YouTube iFrame, and this problem can happen to a few vendors other than YouTube… Be warned, this is a very effective phishing tactic for a VIP user with a high threat profile.
Note: some organizations sharing the links in this research likely don’t realize this is an “exploit” — but some organization created this technical workaround and are likely profiting from their data ingestions.
Twitter has a unique process where they will allow certain technology vendors who have user-generated content that can be embedded into external websites via “iFrames” (YouTube, Vimeo, certain audio hosting companies) to serve the content directly within Twitter.
Twitter users are most familiar with this functionality for YouTube videos — on Twitter, if you see a YouTube embed, which has a consistent look across ~all YouTube embeds (*even the videos associated with malicious links, more on that in a second), you can click on the video, you’ll be able to watch the content, and engage with the video player window, changing audio levels, scrolling ahead in the video, pausing and other controls.
If you are viewing a tweet, and are watching & listening to a video that you can prove is being streamed from YouTube, with all the normal controls and functionality, could you tell if that “youtube.com” link below the video was actually hiding a separate, non-Twitter/YouTube-owned domain, that will ingest your device/network data potentially to reshare or sell that data to a separate advertising company?
The Ed Sheeran screenshot below, watching the YouTube video looks normal, and if you click the “youtube.com”/Twitter card below the video, this is also clean and safe….
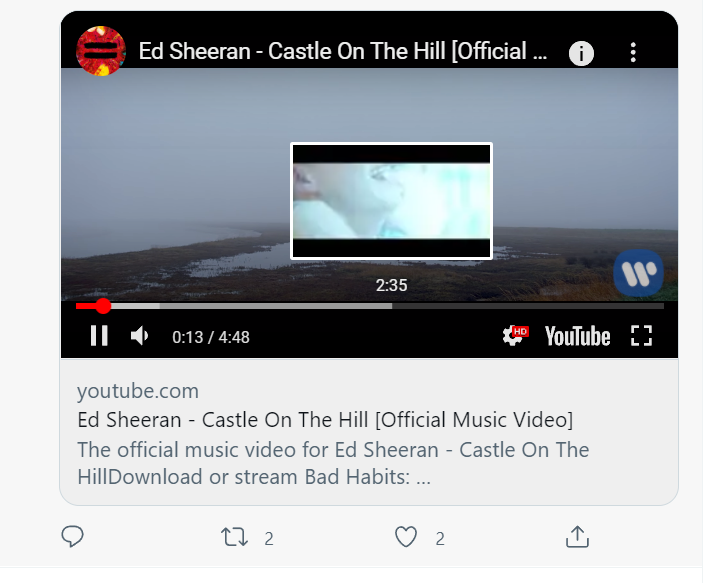
But what about this business video below? Does anything look wrong (just visually) with the screenshot below, which was taken directly from Twitter here? You will notice that this is a YouTube embed, the embedded video has all the normal YouTube functionality, and the Twitter card/link below the video says “youtube.com” – so this would appear to be a Twitter card/ link that would take the user through Twitter’s t.co URL service and then directly to Youtube.com, but that is not what happens.
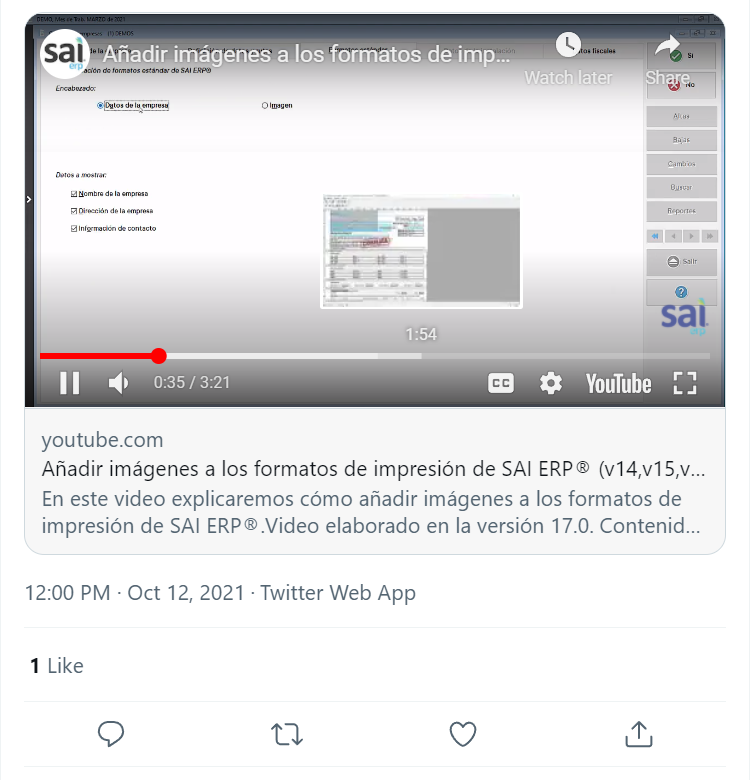
If you clicked on that link above and captured the network requests through the t.co redirect, you’ll notice that your visit goes through this path:
Twitter.com (normal Twitter domain hosting the Youtube embed) -> t.co (Twitter’s normal URL shortened / analytics / security service) -> http://y2u.be (wtf?!) -> Youtube.com
And note… this connection flow goes from secure to insecure, like this:
HTTPS (Twitter) ->HTTPS (Twitter) ->HTTP (y2u.be owner) -> HTTPS (Google)
If you view this Tweet via an embed, can you tell that if you click on the YouTube widget you’ll send data to a company that isn’t Twitter or Google?
How about this video about homeschooling?
Or this techno video?
Or this geology webinar?
Or this video linking to a “workshop replay” for a conference on European AI Policy…
Or this video about how a nuclear reactor works…
Or this Weezer video with random Weezer lyrics?
Or this Baptist Church sermon?
Fun fact: all those embeds above were malicious.
100% of the embedded tweets above are sharing data to y2u.be if you click on the YouTube links — yet the video content is hosted by Youtube and the final URL is on YouTube.com.
For some reason, there are also certain Twitter accounts targeting BTS fan videos that also scrape user data via the y2u.be redirection exploit. Many of these videos also embed domain arrays, so you can more easily see that the YouTube video embedding into the tweets is associated with the y2u.be domain.
A few examples from one account consistently sharing the y2u.be links:
Now… does Google own y2u.be?
Nope. Y2u.be does “not hide” that they have built a URL redirection service and you can see that if you go directly to their homepage @ https://y2u.be/
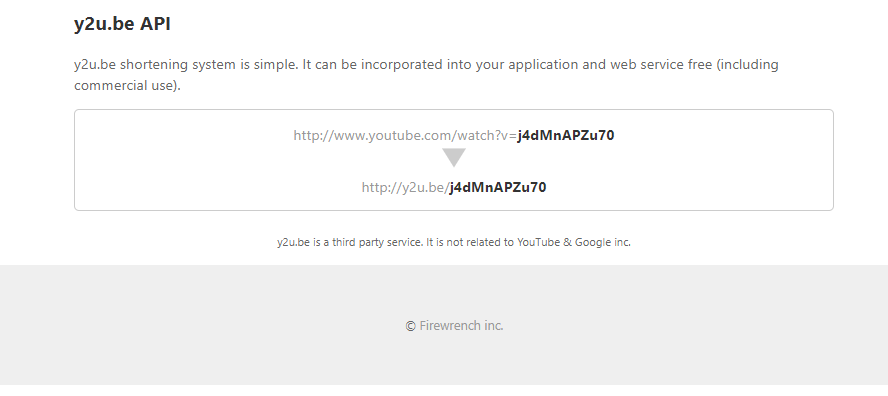
In the footer of the y2u.be domain, you will see that the ownership is “Firewrench, inc.” @ https://www.firewrench.com/
On this website, the company admits to owning a few apps, that all have ads @ https://www.firewrench.com/apps
You can see one of their iOS apps here. The developer details link for this app goes to a new website where you will see Google ads @ https://www.linemp3.com/

If you click through the 4 apps owned by Firewrench (including the one above), you’ll see Google ads across all the websites, with reputable brands buying ads on the sites.
Here are some screenshots of these sites, and the ads shown in one page view:

So a company that makes apps that feature heavy ads, also has a YouTube redirection service that users can’t see from Twitter, what’s the big deal?
You can view the Firewrench Privacy Policy @ https://www.firewrench.com/privacy
First, none of the data flows to Firewrench’s youtube shortener are secure (they flow over HTTP), yet this company literally claims the opposite, writing (translated): “FOR THE TRANSMISSION OF INFORMATION, ENCRYPTED COMMUNICATION BY SSL IS PERFORMED AND MANAGED IN THE DATA BASE IN THE FIREWALL.”
There are also at least 8 “third party advertising services” that are disclosed as working with Firewrench from within this privacy policy:
“Within our services, we use third-party advertising services (Google, Fluct, Yahoo!, nend, Ninja AdMax, imobile, A8.net, etc.). In order to display advertisements that are optimal to users, advertising distributors may use information about access to this site and other sites (name, address, email address, telephone number) by obtaining information through cookies and web beacons.”
Directly below this section, Firewrench discloses new advertising partners:
“Google
Yahoo!
MicroAd
Fluct”
This is the Microad website & privacy policy, which is a Japanese advertising company @ http://send.microad.jp/w3c/
This is the Fluct SSP website & privacy policy, which is also a Japanese advertising company @ https://corp.fluct.jp/ + https://corp.fluct.jp/privacy/
In conclusion, currently Twitter is allowing a company with numerous SSP advertising partners to conduct a HTTP data scrape of Twitter user data when they are attempting to click on YouTube links, and Twitter’s t.co URL shortener doesn’t expose the insecure miTM domain for anyone, on any Twitter platform.
Currently, a creative attacker can setup an insecure domain redirect to YouTube, and not only monetize the fingerprint data through online advertising partnerships, but also potentially conduct offensive attacks against specific VIP users who click to view specific YouTube links.
Twitter was warned about this behavior in the context of exfiltrating user data to be monetized by unethical advertising companies – a fingerprint SSP user table built off the specific interests of each youtube click – scrape the youtube video metadata and associate it to the user data/ network data / fingerprint scraped via the insecure redirect, and then sell that fingerprint + contextual-intent as targeting criteria to other brands and advertising companies.
There are other creative ways this type of “real YouTube embed on Twitter to honeypot a scraped click into an insecure connection” but I’m going to hold off on explaining anything else. I hope it’s clear that this could happen with more than just YouTube embeds, and Twitter needs to stop pretending like this isn’t a real risk for certain types of users — and at-scale, this is a risk for everyone who doesn’t want their YouTube interests sold off to advertisers along with their device/network information — it’s bad enough that YouTube is owned by Google, but we don’t need even more advertising companies scraping this information in unexpected ways…
Questions? Concerns? Edits? ping me on twitter @thezedwards

Recent Comments