A global hacking group took over Epic Games subdomains, then the problem was swept under the rug by Epic Games.
At the end of March, 2020, Epic Games posted on their Twitter account a $1 million bounty for anyone to provide information of any corporate astroturfing spreading rumors about Epic Games, particularly with regard to Epic Games’ House Party users complaining about being hacked.
We are investigating indications that the recent hacking rumors were spread by a paid commercial smear campaign to harm Houseparty. We are offering a $1,000,000 bounty for the first individual to provide proof of such a campaign to bounty@houseparty.com.
— Houseparty (@houseparty) March 31, 2020
This unusual ‘commercial smear’ bounty was covered by a variety of reporters, with a limited amount of facts available, other than random Twitter users complaining about being hacked.
After the bounty was issued, House Party started to back track, and made a claim rejected by Twitter that there were unauthentic users spreading the rumors. Twitter provided a comment to a Buzzfeed article on the story stating, “‘We haven’t seen any coordinated activity related to conversations about Houseparty, but are continuing to keep an eye on it.”
After the bounty was issued, I quickly just pulled up their web login page to get a sense for their security — I was quickly shocked with their lack of protections for users and tweeted a brief detail about a lack of “Content Security Policy” (CSP) request headers for the login form that would prevent MiiM phishing attacks — their login form could be embedded on a 3rd party website without it breaking:
Your password reset page @ https://t.co/pE2gLfgvww is on an insecure page that can be embedded for phishing attacks due to no CSP headers // that page is linked from your login page and it's just one of many problems for your users.
This $1 mil bounty = joke, right? pic.twitter.com/Erg7KrqTgn
— ℨ𝔞𝔠𝔥 𝔈𝔡𝔴𝔞𝔯𝔡𝔰 (@thezedwards) March 31, 2020
After tweeting that detail, I realized that there was potentially something much worse going on with Houseparty, and I wrote up a report and tried to submit it to their bounty@houseparty.com email that had been released to the media. Several days later, the email I sent them was responded to, and I was told that in order for House Party to triage my ticket, I would need to submit it through their preferred bug bounty program hosted by HackerOne.
I re-sent the details of my ticket, and flagged prominently one of the Epic Games House Party subdomains that had been taken over, they looked like this:
There were dozens of similar subdomains compromised by the attackers, and you can still see some of the Redirection Malware that they uploaded via Google searches — this was from May 18, 2020 (the links are broken, but cached content can be viewed):
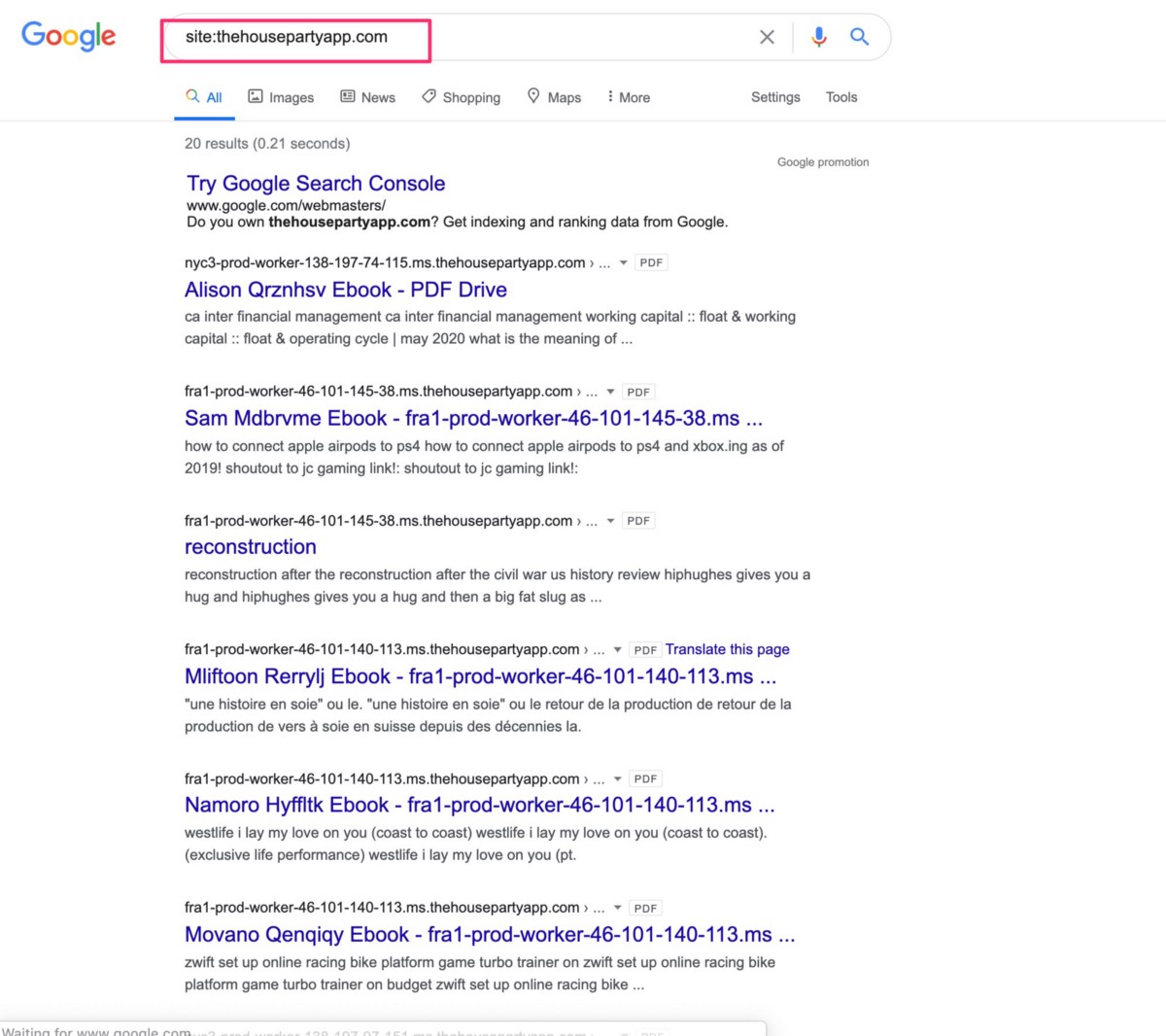

If you open any of these cached files that appear to be PDFs in the Google cache, you’ll see random text details and then deep links to tons more of the PDF files across a compromised domain — these deep links push the pages into search results and basically are an SEO-malware-optimization technique. When the pages were live, they also all triggered PHP redirects to new domains — these PDF->Page URL redirects are visible across the internet on dozens of other compromised domains, more details below.
Here’s a screen shot of one of the Epic Games compromised pages and the additional requests linking to other compromised content on the Epic Games subdomains — You’ll also see highlighted here a string referencing a unique domain — this string can help you find other compromised websites in this attacker’s network:
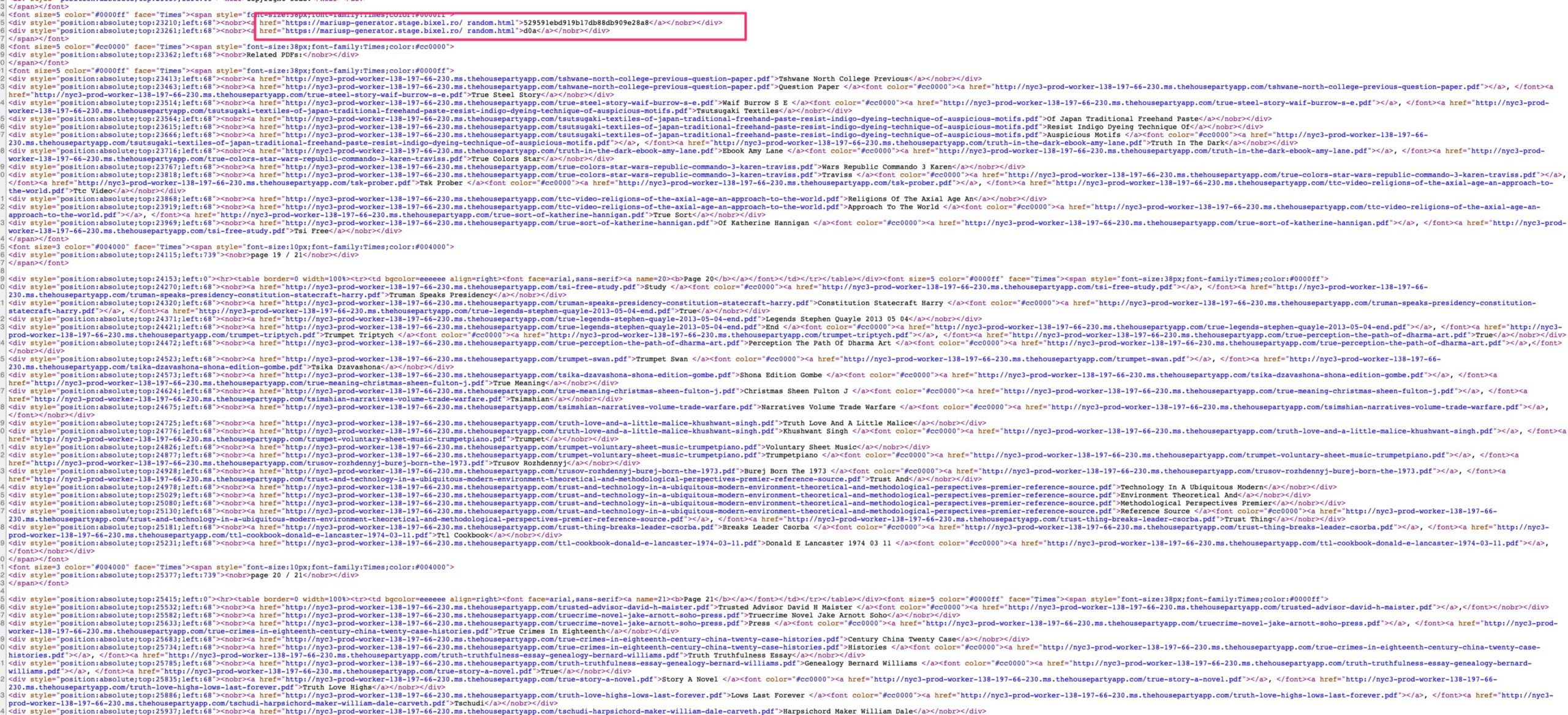
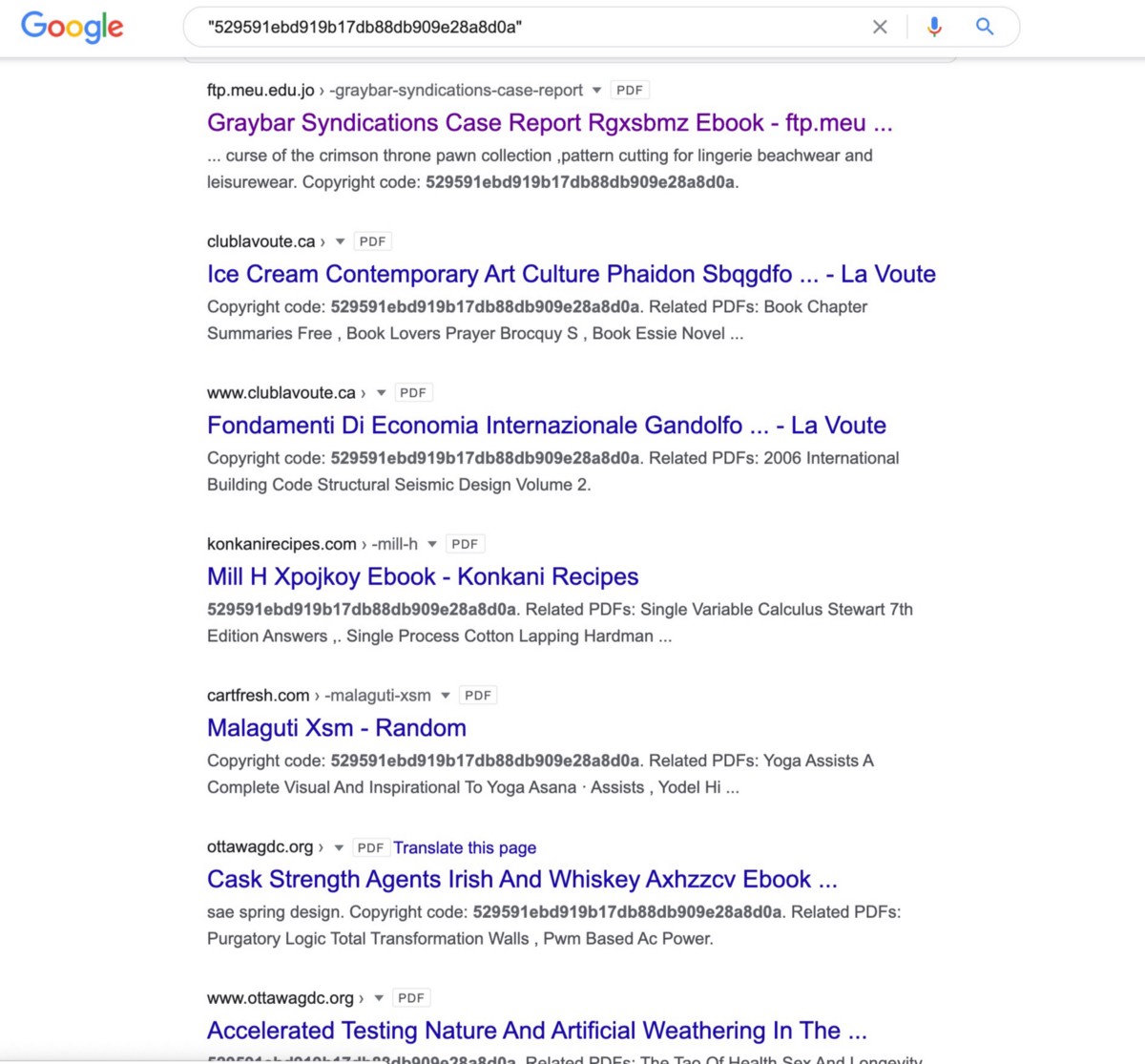
If you take the string above “529591ebd919b17db88db909e28a8” and then Google this string, you’ll find 29 other compromised domains that have this same PDF-string:
A similar process can be conducted across all of the malicious PDFs (poisonPDFs) that were uploaded into the compromised Epic Games subdomains — and the attackers even wrote messages to taunt Epic Games like this one in their Lola PDF: “Rather than enjoying a good book with a cup of tea in the afternoon, instead they juggled with some malicious virus inside their desktop computer.”
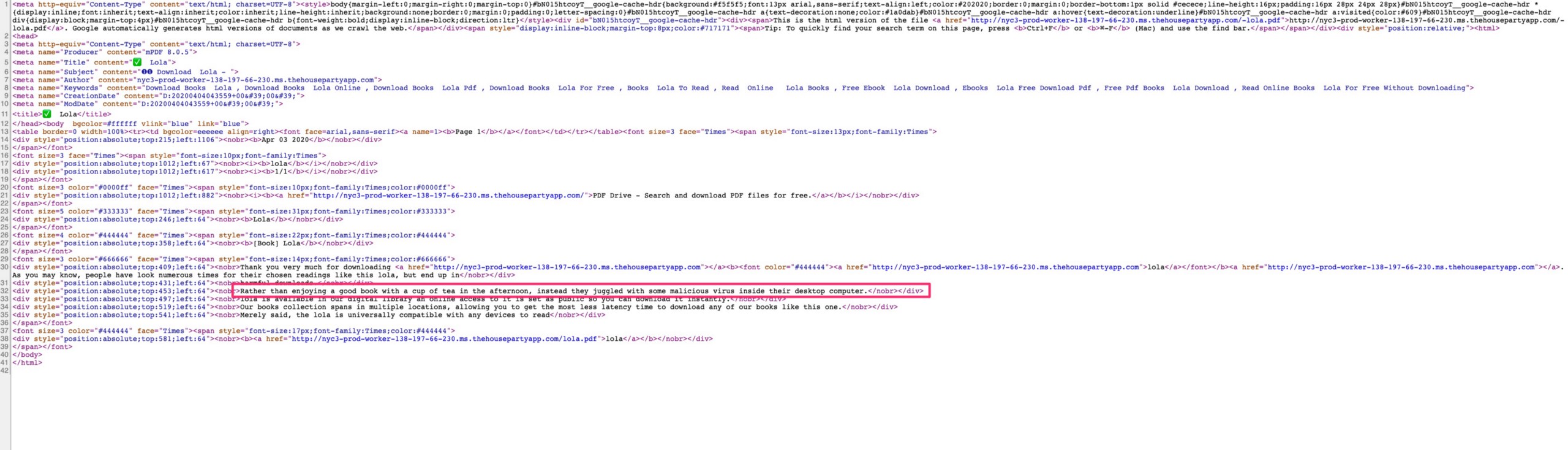
While I haven’t read the book Lola, I’m familiar enough with the content and when it was written to assume that the book didn’t include any references to a “malicious virus inside their desktop computer”
This string is also useful for finding other compromised domains — a quick search of the initial portion of that string shows that there are even multiple versions of the same sentence, translated slightly differently. You can see those results and more compromised domains:
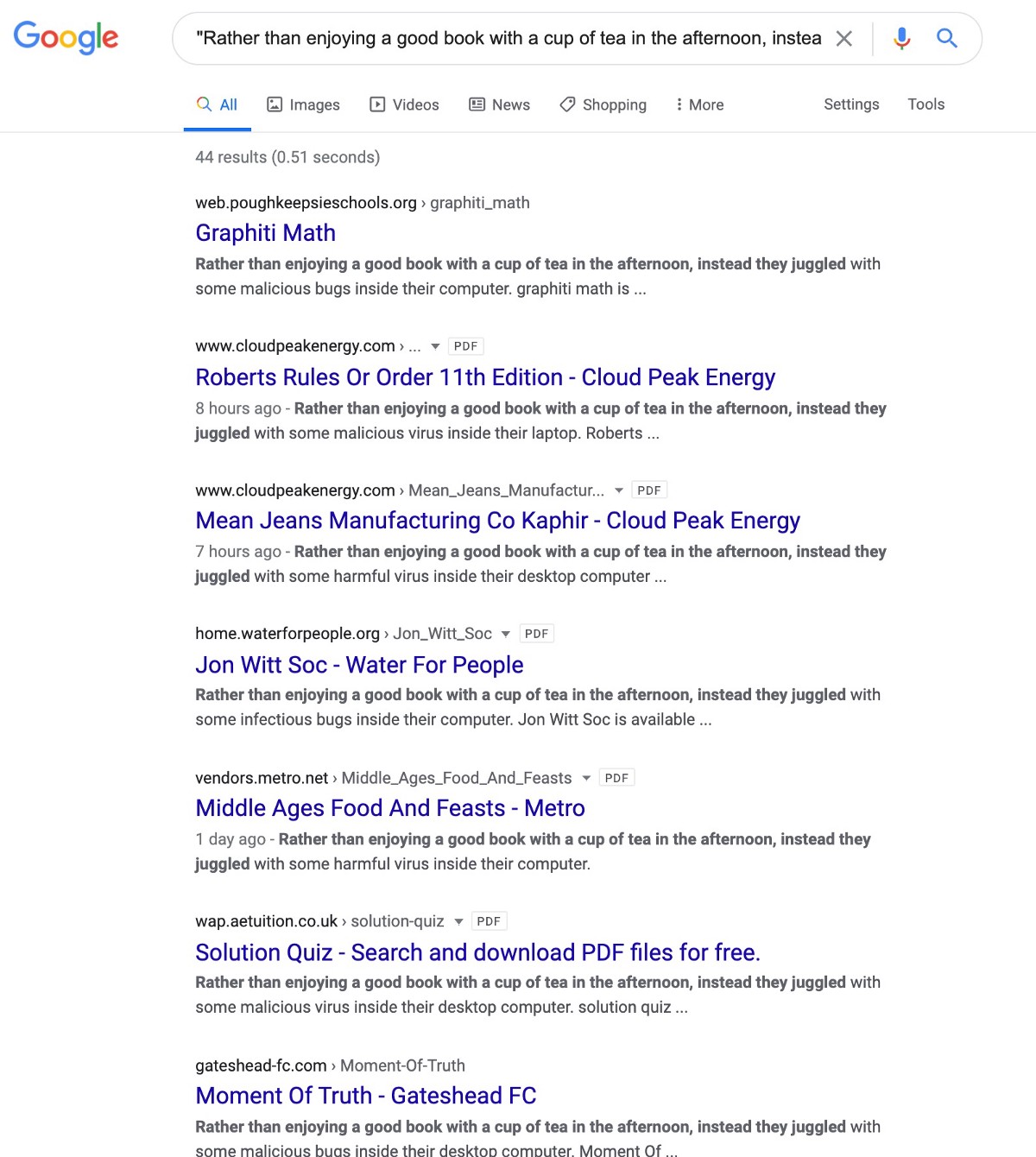
A huge portion of the 44 domains in this search result are still compromised and some of them have lists of all the compromised PDFs — if you click any of these links you will be taken into malicious redirects and I would STRONGLY urge to be extremely careful not only visiting this top level domain but clicking any links like (WARNING: http://www.cloudpeakenergy(.)com/)
It should also be noted that in the results above, one of the poisonPDFs is for “Roberts Rules of Order” — it’s important to understand that this book is used by politicians, regulators, people in charge of open meetings, and attackers would know that anyone searching for free versions of this book would likely be a VIP individual who could be connected to politicians or political decisions — so attackers like this show their political sophistication by creating entire networks of poisonPDFs for free ebook copies of “Roberts Rules of Order.”
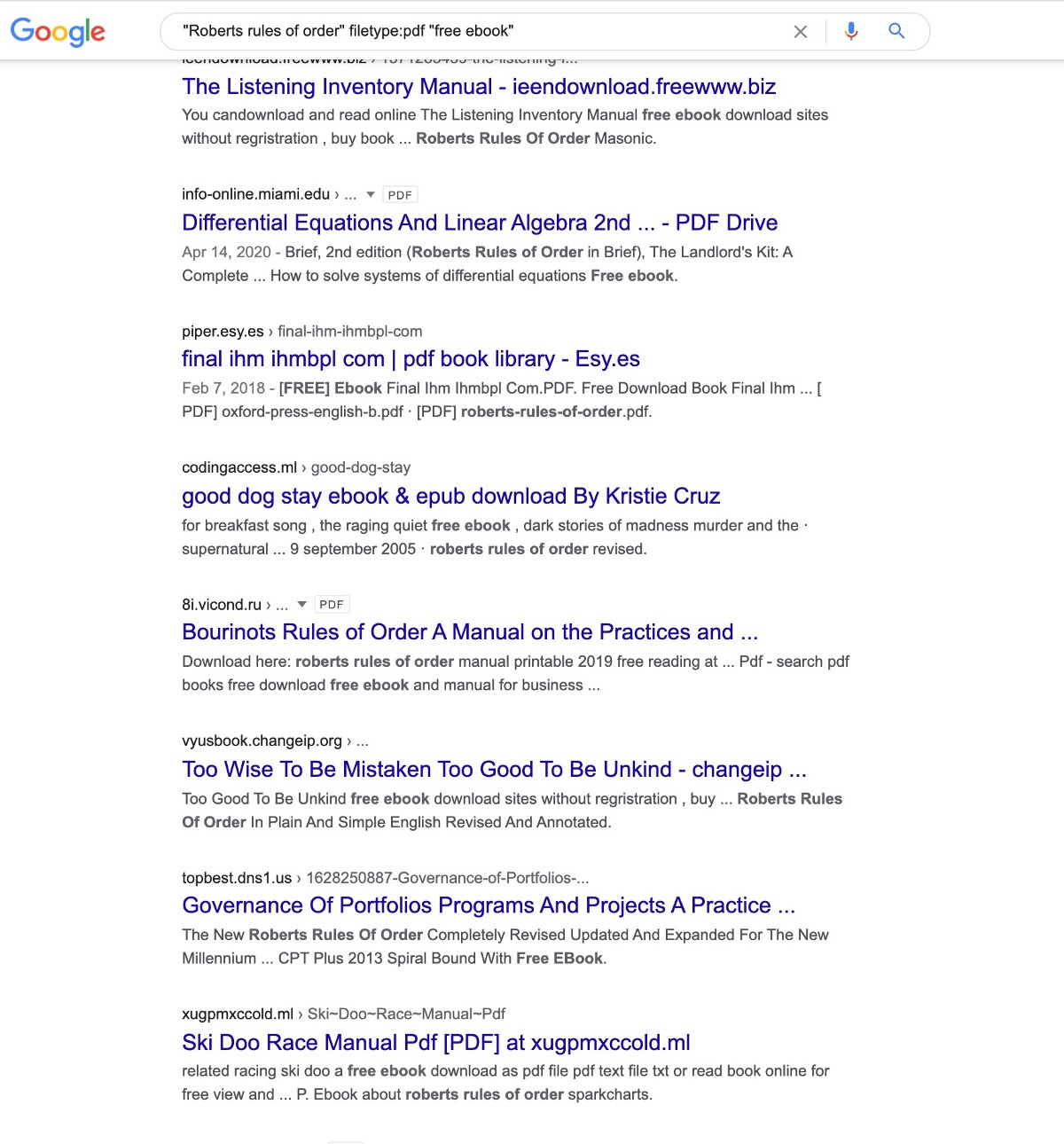
Maimi.edu was one of the domains that got hit big time, and they had over 100,000 files hosted on their compromised subdomain before it was fixed:
Whenever you visit one of the hijacked subdomains and their “files” / pages on them, you’ll be pushed into a redirect and dropped into a series of websites that are likely owned by the same criminal group. The domains look like:
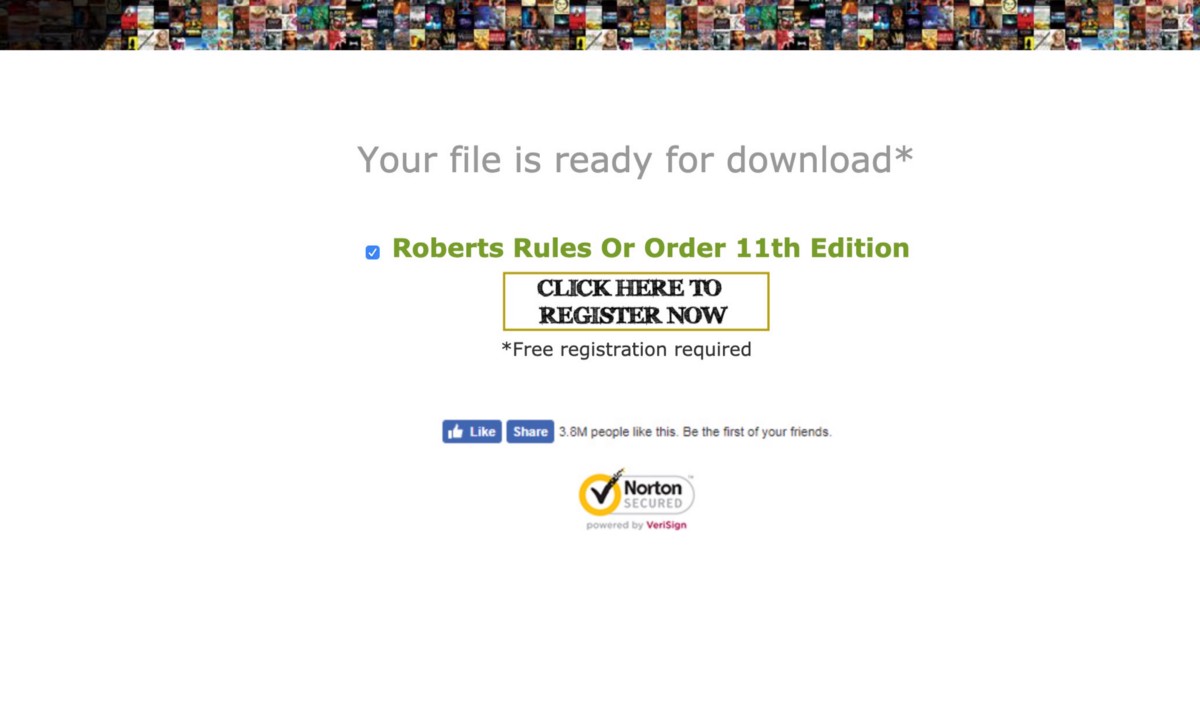
If you stay on these pages long enough or click to Register Now, you’ll be taken to a new domain requesting signups — these websites exist for Ebooks, video streaming services, and a wide variety of websites promising “Free Media / Downloads / Books / Movies etc” — here’s one of the landing pages in this specific redirect scam:
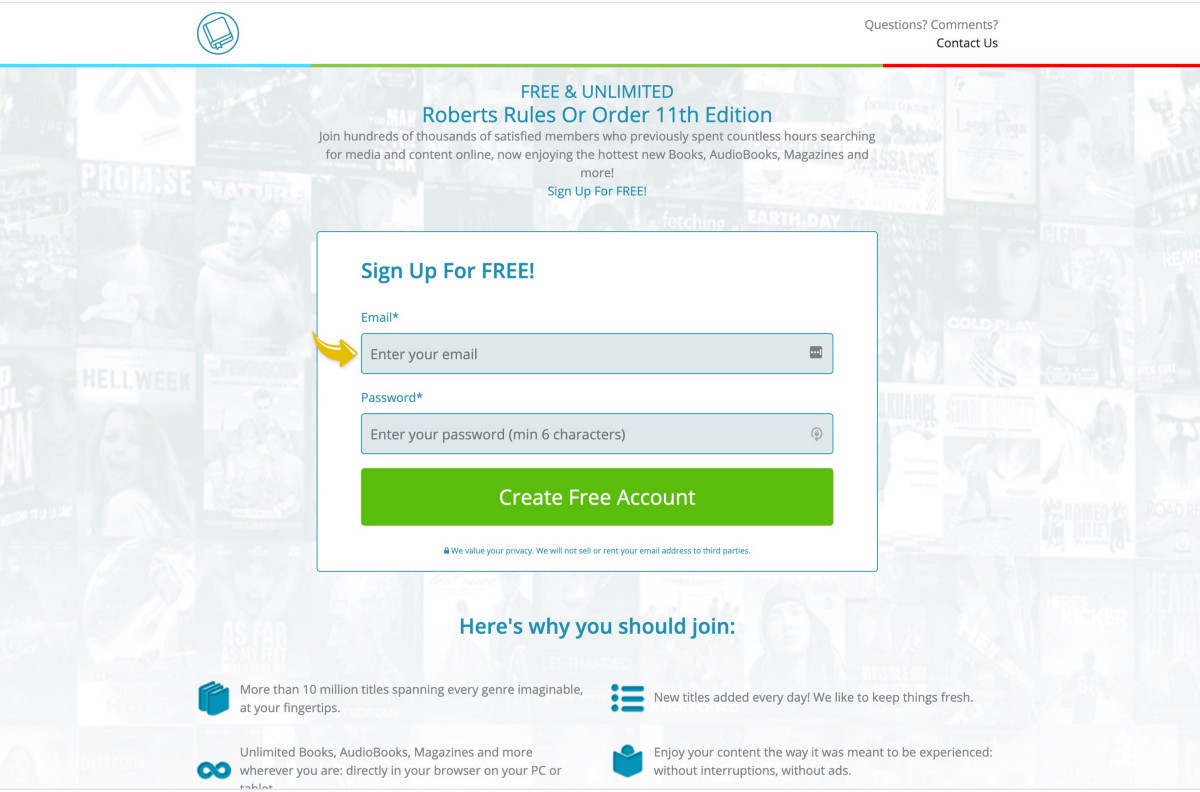
There are massive networks of these websites — they all have similar messaging, similar promises, and are likely being used for complicated forms of credit card fraud and account hijacks for reused passwords:
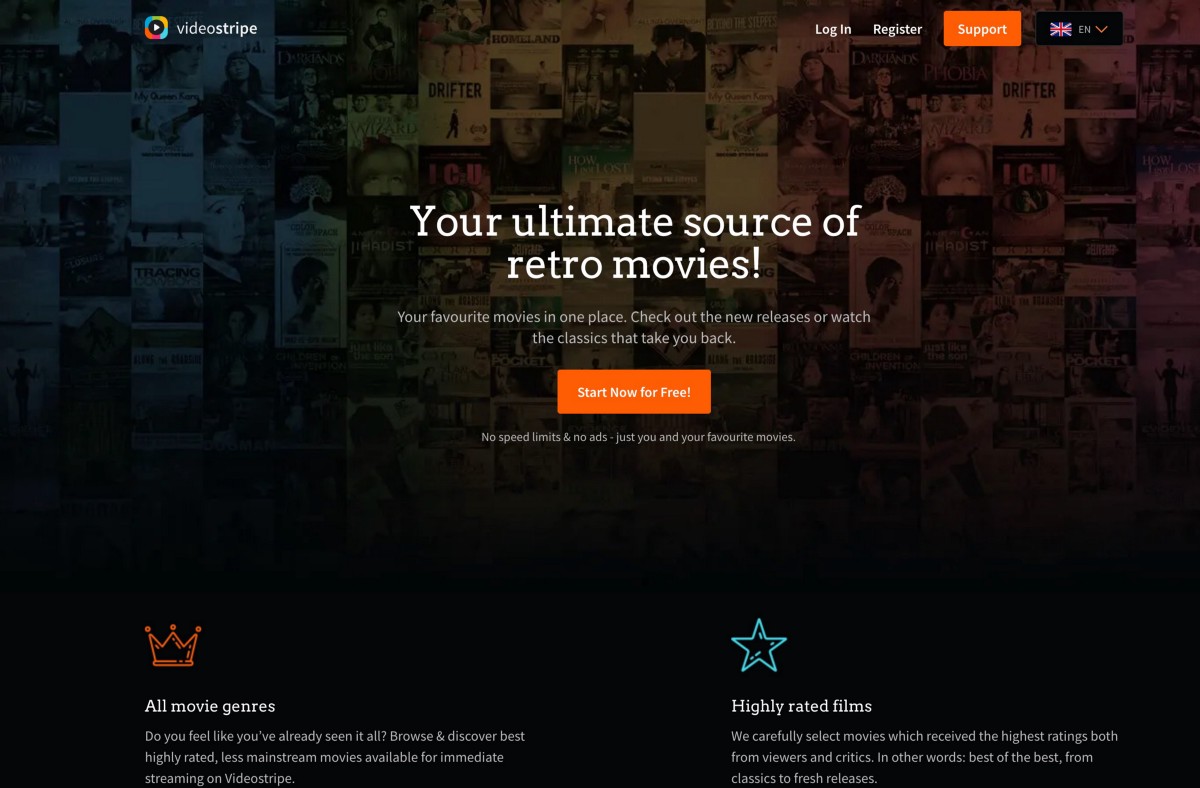
These websites even signup affiliates and appear to offer fraud services on specific affiliate pages like: https://my-ebooks.club/affiliate
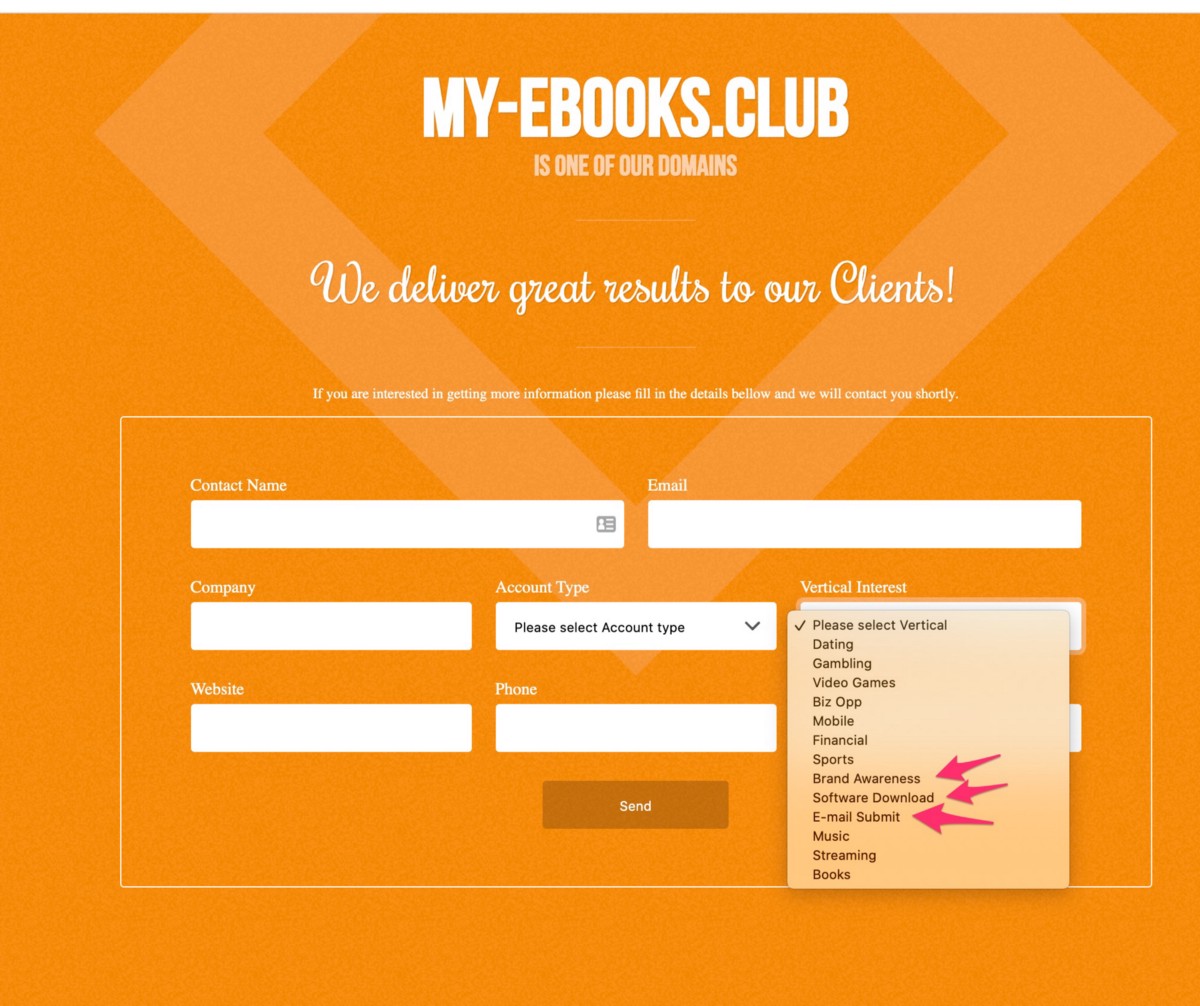
On this Affiliate signup page, it’s one of the few pages in these attacker networks that actually, factually, is probably used to signup new partners. And even spammers want to know their conversion rates, so the folks who setup this network embedded their actual, factual tracking code from Matomo Tag Manager and several other unique strings can be used to find their other assets. The Matomo Tag string that uncovers more of their work is: https://collecting(.)click/js/container_ecko3JmF.js
That string -without the (.) included above – can be searched and more of their Ebooks/redirection spam uncovered — some of it captured by antivirus companies:
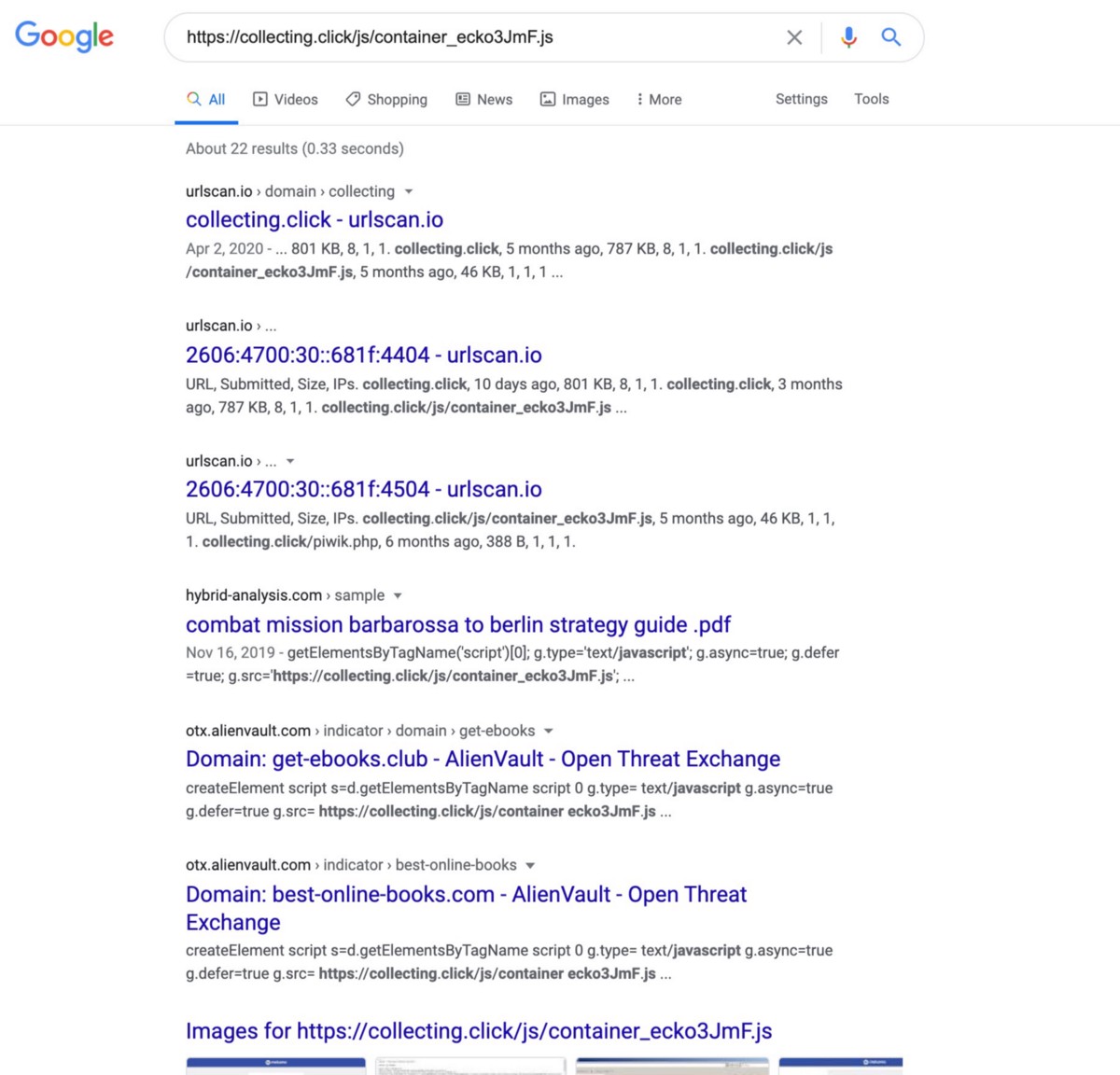
If you visit the results in this search, you’ll find more of the “free media” scams like — https://best-online-books.com/
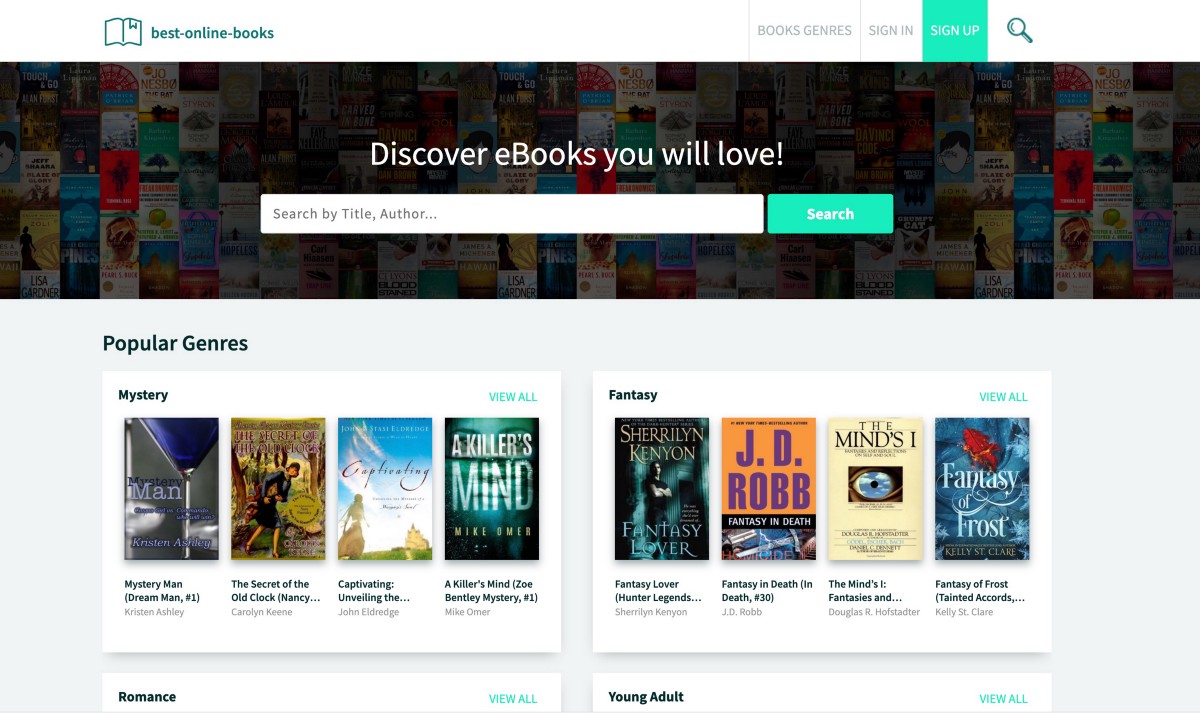
And nearly identical sites can be found using strings on these pages:
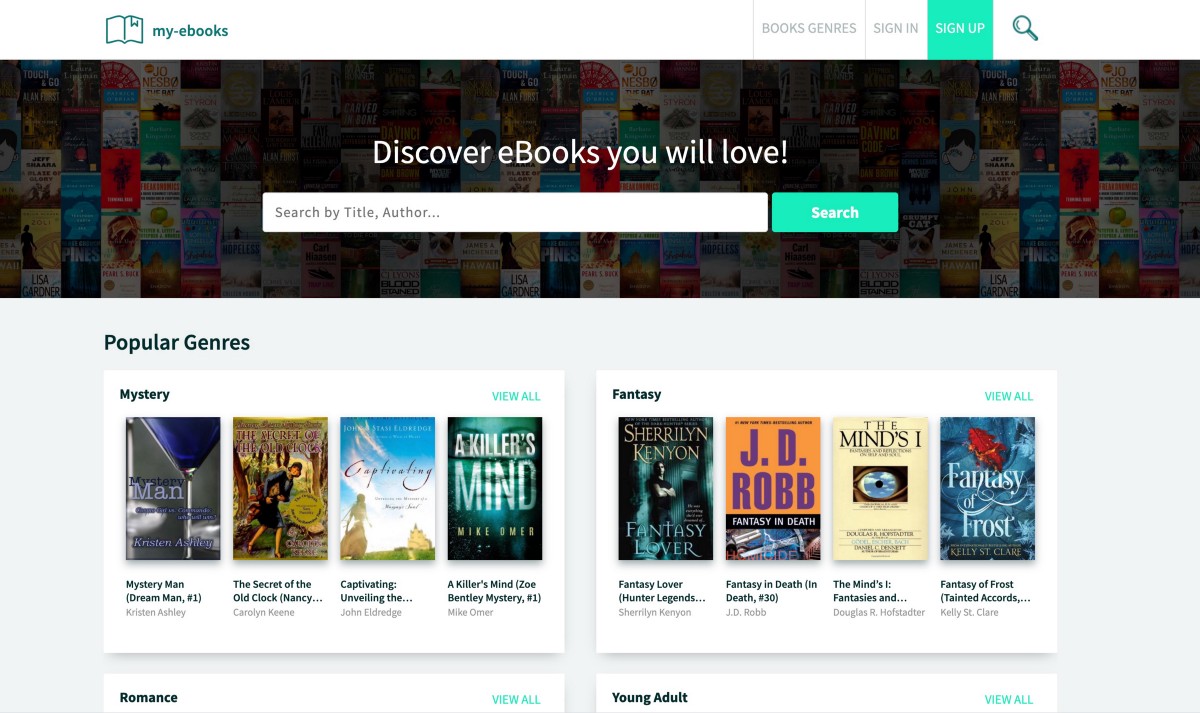
Some of these domains can be searched on SecurityTrails.com and you’ll find subdomains on them that are mapped to larger networks of these hijacked domains — the domains seem to be registered/hosted via “Serverius Holding B.V.” which makes it easy to confirm that the 134 domains registered and hosted on IP Address 37.1.223.152 on this list are the core domains in their network, which they connect to hijacked subdomains for their redirection scams:
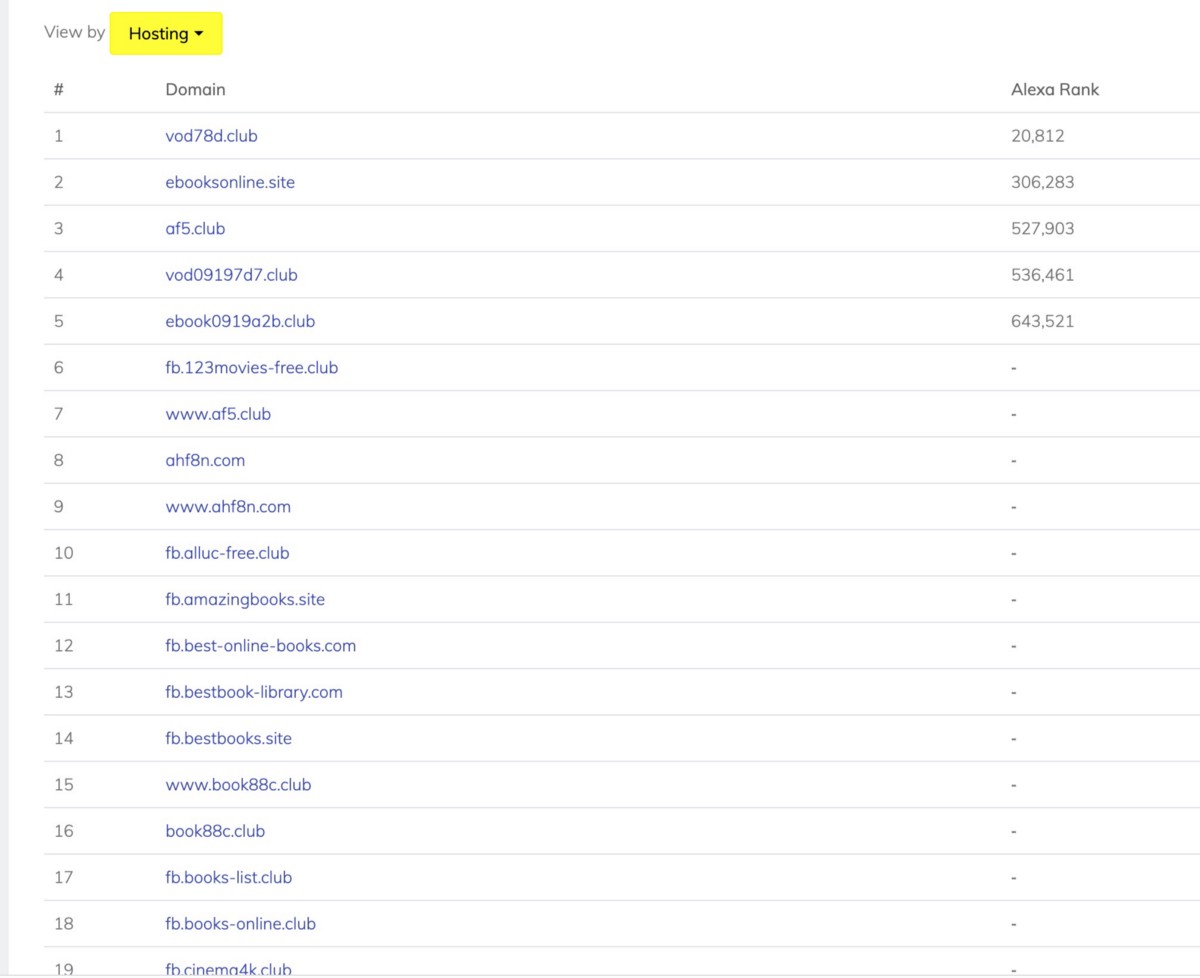

These domains all have the same affiliate signups and redirection scams that were highlighted above in the other core domains:
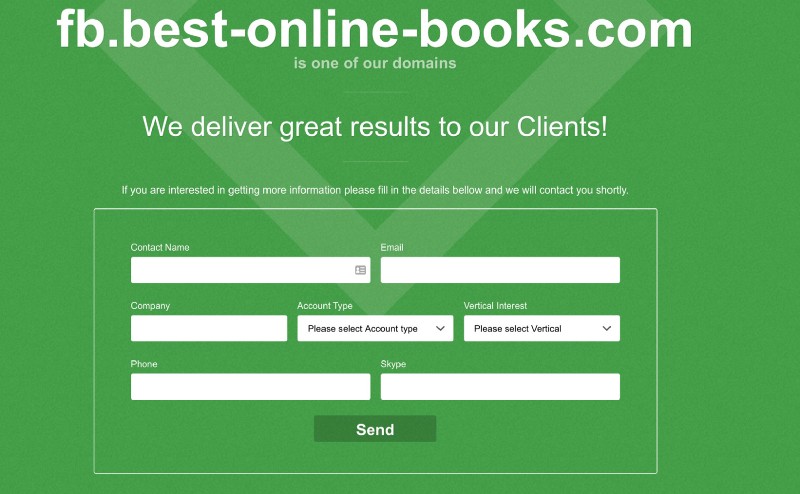
On these pages, the web fonts are being requested from “webfonts.ru” — this and other details point to a Russian-language network behind these hijacks:
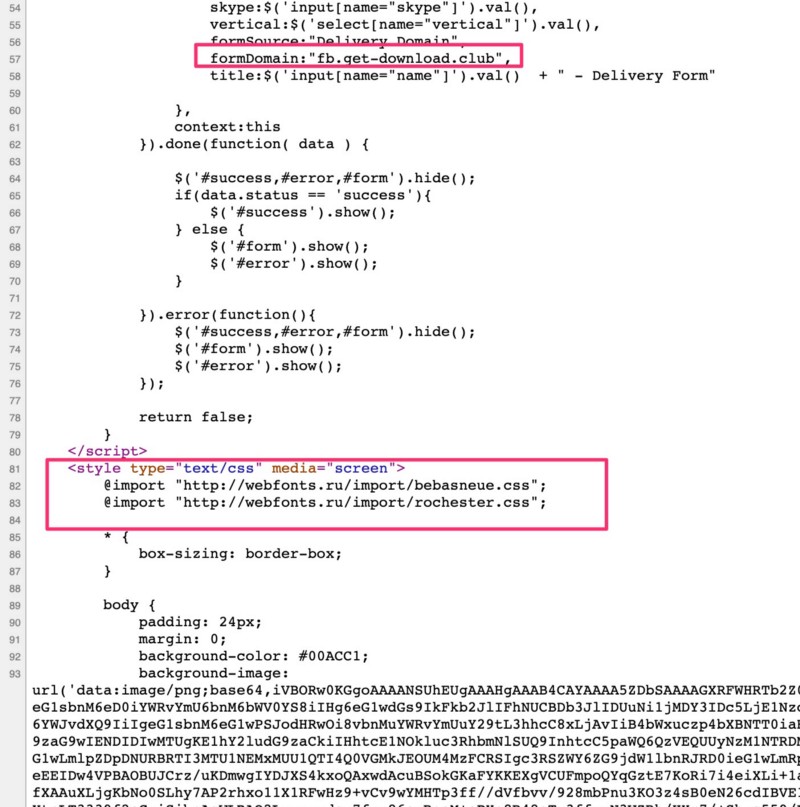
These sites are heavily focused on Ebooks, Free movie streaming and other “free media” services that would trick a user into creating accounts quickly — they also have websites like “hd-stream(.)club” which seems to target Soccer fans — if you click on that website to view any of the live streams you’ll be redirected to another site in their network with a URL like @
https://()my-sports(.)club/sports/signup-dual/-/#/z=yhuuIk3ZOQofMgGkUOfQ6Z/theme=default/q=/s1=/s2=/s3=/s4=/s5=/source_id=e7f60728-784f-dd02-117d-e3dc046d292b/project=1M5iou/mh_offer_id=/dp=gTtt4NObPRkknNLoJfIss9/m=/c_bg=/c_img1=/c_img2=/c_color=/source=Direct/software=Browser/domain=cdn.spba7(.)club/
These “Register to Start Live HD Stream” landing pages would likely trick some users into creating simple passwords they’ve used on other websites:
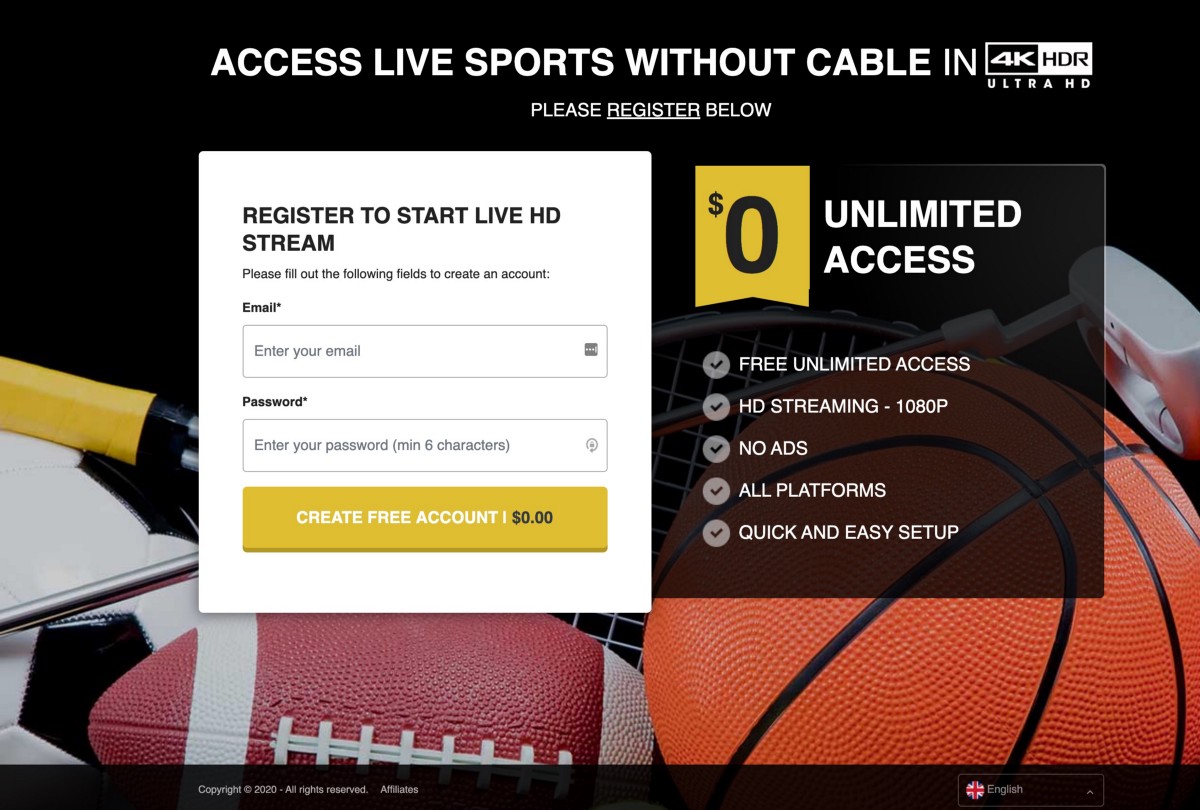
The link above in the footer for “Affiliates” — when clicked, takes users to a very familiar Affiliate signup page:
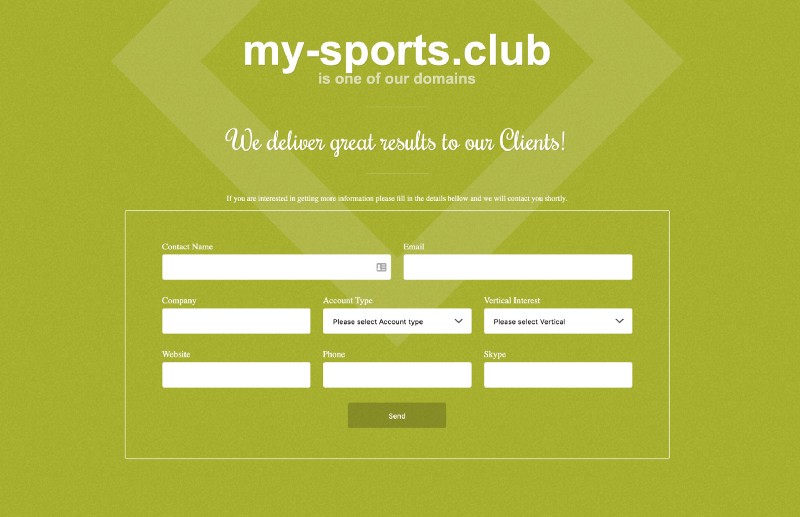
In the source code of the My-sports.club website, there is a reference to this domain “cdn.spba7.club” — across all these networks in the source code / metadata there are additional domains referenced. A huge portion of these domains, when entered into the URl bar, redirect to “webtools.media” which is a platform SPECIFICALLY built to redirect users to unique webpages/websites based on their country of origin. This is how a user in the United States would be redirected to a specific domain, and someone in the U.K. could be redirected to another domain. This type of orchestration is used by all sophisticated operators to try and hide their work from U.S. auditors or auditors they know exist in specific countries. By merely focusing malicious redirects on certain users and not others, a hijack can look “random” and like some sort of local human error or local compromise, instead of a network compromise orchestrating the delivery of people to specific malware/phishing domains.
The domains listed @ https://securitytrails.com/list/ip/37.1.223.152 have a wide variety of these phishing sites — they all promise high quality content with slick looking websites like:
You can view a Google sheet of these domains just in case they go away, here. Be very careful with this list — don’t visit these sites unless you are aware of the risks and purposefully trying to expose yourself to those risks.
Criminal Group Running Redirection Scams and Domain/Subdomain Takeovers Hit Epic Games House Party Subdomains, Epic Games Downplays User Risk with Technical Incompetence
As mentioned above, a wide range of subdomains were hijacked on “TheHousePartyApp.com” — which is owned by Epic Games.
The first thing you should notice is that the subdomains that were compromised were on the domain “TheHousePartyApp.com” — the core domain for House Party is “HouseParty.com” but you can see in this screen shot below that the “app.houseparty.com” login page had a Content Security Policy that allowed code to be fired from “wss://*.thehousepartyapp.com” and “https://*.thehousepartyapp.com” // The second entry there with “*.thehousepartyapp.com” has an asterisks “*” in the subdomain field — this is a “catch-all” entry and any subdomain on thehousepartyapp.com then had the elevated privileges to fire javascript code in the window/page of the HouseParty.com login page:
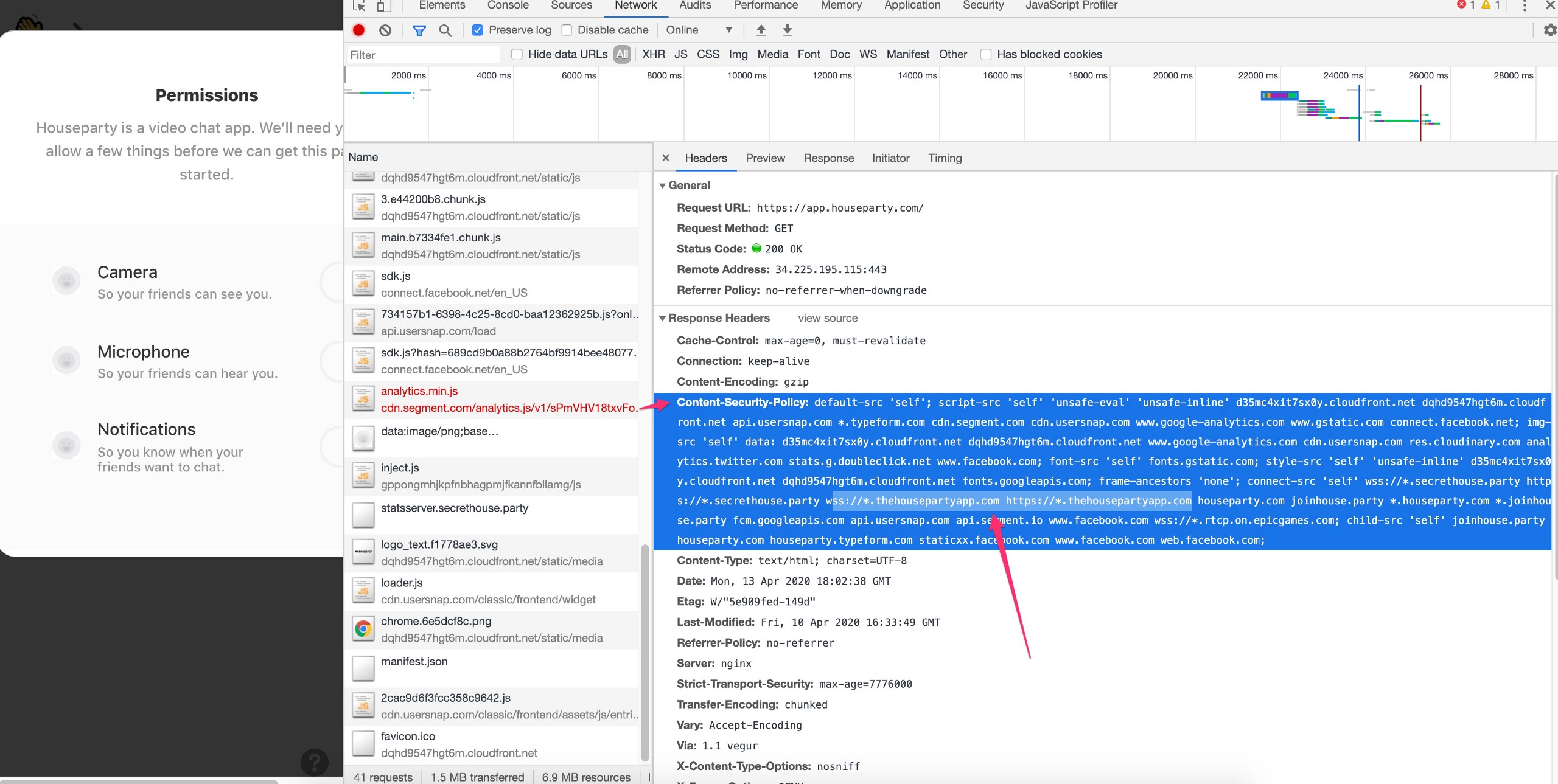
The details above, with the CSP policy + the vulnerability that exists on the login page were sent to the Epic Games team, who argued that because the hijacked subdomains didn’t have code from Epic Games on them, somehow those subdomains were safe. They wrote:
Thanks again for reaching out, all of these records should now be cleaned up and we’re putting checks in place to address future takeovers. Would you like to confirm we haven’t missed any records before we resolve this?
…
I’m also dropping this to a Medium, as this was a result of old IPs that a new user inherited, rather than a compromise of our infrastructure. If you have any other questions please let me know! Once you confirm I’ll close this out.
I asked whether they read my ticket and questioned whether they understood the risk to users, they responded:
In regards to the severity change. This report was originally submitted under the impression that our environment was compromised, and as a result a bad actor was actively taking over subdomains. We confirmed that is not the case, and that the subdomains in question were pointing to abandoned DNS records, which in turn were automatically inherited by a third-party which was hosting eBooks. We found no indication of a targeted compromise.
We are investigating your findings on api2.thehousepartyapp.com. Can you please file a separate submission so we can track that? Any additional POC you have for that would be greatly appreciated. As long as that submission follows responsible disclosure practices we can transfer it to our bounty program and award the appropriate bounty.
I further questioned the Epic Games team and their reference to a “Third-party which was hosting ebooks” — they then responded with:
The domain you listed is a subdomain of thehousepartyapp.com, which is a domain we own. That is one of the subdomains that was addressed in this submission. The content that was hosted there was not being hosted by us. A third party inherited the IP address that HouseParty formerly owned, the DNS record associated with that IP was never removed, which is why that subdomain still directed to the IP in question.
Even though a subdomain owned by us points to an endpoint, that does not mean the endpoint is hosted by us. For instance, foo.houseparty.com could be directed to Google, but we are not hosting Google’s content. HackerOne has a great writeup on subdomain takeovers available here.
I further questioned their understanding of subdomain takeovers and they replied with more caveats:
This issue has been discussed with, and investigated by, the Epic Games team and the conclusion is that other than the fact that non-legitimate content could, and was, being hosted by this third party, further exploitation was far less likely.
You mentioned second order subdomain takeover, and in order for that to happen, domain A, which I assume you are referring to the parent domain,
http://thehousepartyapp.com/, would need to import some resources from domain B, the affected subdomain. That is not the case here. The takeover of a subdomain per se does not directly mean that the parent domain would be affected. There are mitigation factors that come into place and render exploitation unlikely.
In this case specifically, due to the nature of the relationship between the parent domain and the affected subdomain, further exploitation would most likely not be possible. No cookies are set in the affected subdomain and the ability to read/write them in the parent domain would also not make exploitation possible, because session-wise, the parent domain does not rely on session cookies for authentication.
It is also important to note that when dealing with security vulnerabilities in the bug bounty realm, evidence of exploitation along with a proof of concept leveraging the issue to a practical exploitation scenario are of utmost importance. Even though you have pointed out that some subdomains pointers were left dangling and a 3rd party was hosting content on those assets, everything else is purely theoretical.
All of the above results in the reasoning behind lowering the severity of the issue, and why it did not have as severe a potential impact to Epic Games as it might have originally seemed. Hopefully that will help to explain the situation, and how the team came to their conclusion.
… and also wrote:
The first discussion is related to the technical issues that you submitted. Those being, that there were a number of subdomain pointers that had not been updated and were pointing to an IP address now controlled by another organization, and the permissive cookie structure in the CSP. This conversation is relevant to your submission to the HackerOne platform and, with the information that you have provided, the Epic Games team evaluated the impact and removed the abandoned DNS entries identified in your report. The team also identified and removed additional entries no longer in use on the HouseParty platform. Epic Games is implementing further tooling to address retired subdomains and evaluating updates to the CSP on app.houseparty.com. To be clear, these subdomains were not maliciously created by an attacker, they were created by the HouseParty team and were not deprovisioned when they were replaced. The Epic Games team has found no indication of exploitation of the DNS entries you identified, nor any additional entries identified by the team.
The standard flow of how reporting works on the HackerOne platform is that a hacker provides a proof of concept for a security issue and how it could be reproduced. Then the security team at an organization internally reviews the impact of the finding and takes any appropriate actions. In this case, any security vulnerabilities related to your finding are theoretical from your point of view, of what could be done, not what has been proven. There is a lot of discussion in this report so, if you are able, please provide a new technical write up of any proof of wrongdoing that you were able to identify, and we will be happy to take that into consideration.
As a side note, the issue that you mentioned relating to api2.thehousepartyapp.com sounds like a separate issue, and the Epic Games team would encourage you to submit that separately to the program on HackerOne. They will be glad to evaluate it separately, please keep in mind this submission must follow responsible disclosure in order to qualify for a bounty on HackerOne.
Epic Games was even told the name of the attackers, a link to a news article about the attackers, and details about these phishing / credit card attacks that have gone on for years
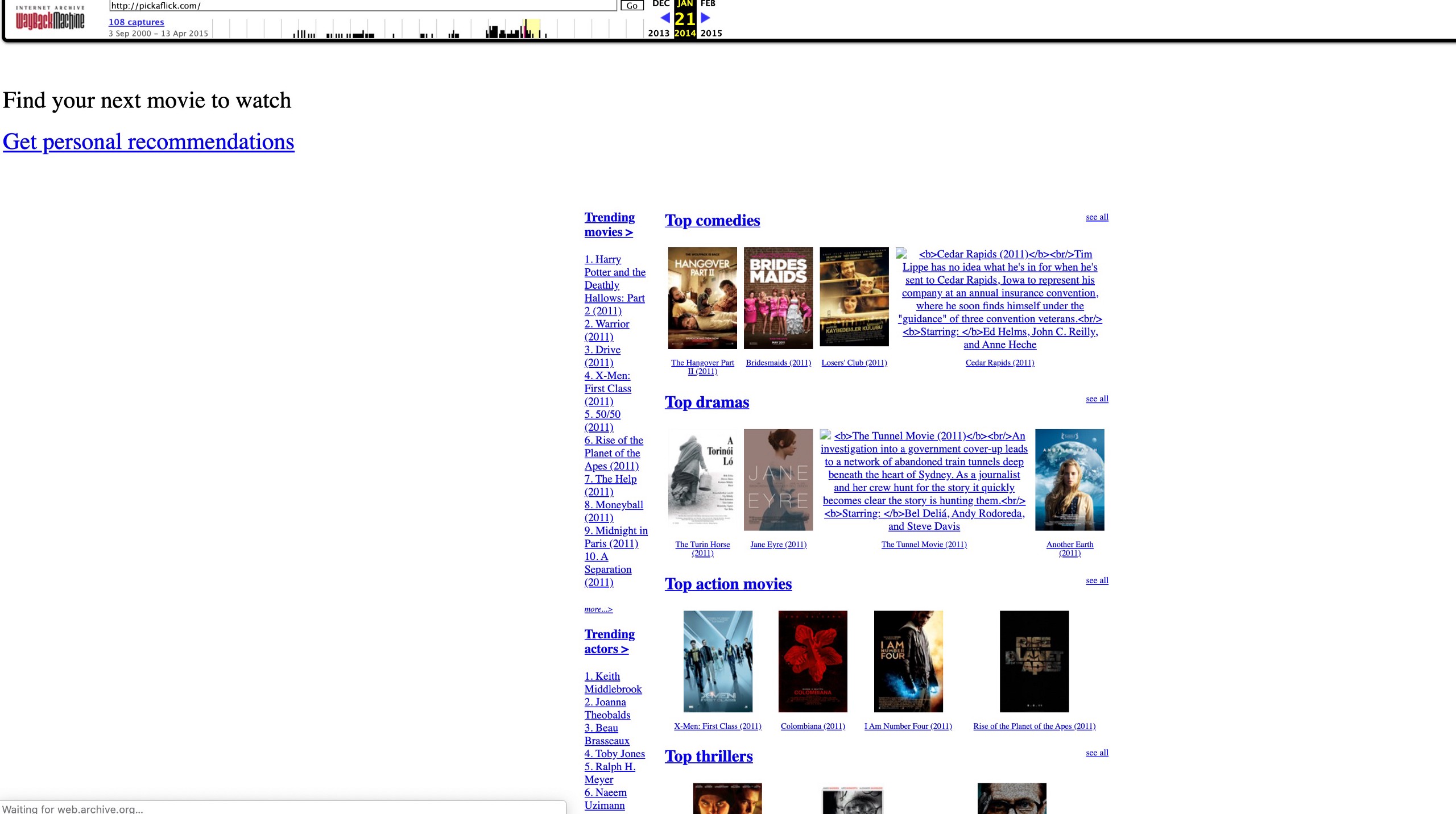
I’ve named the attackers who commit this work the “Pickaflick.com Crew” due to the fact that they have been operating various credit card scams for a decade or more (and were basically named this in the past) — you can see their legacy “PickaFlick.com” website @ http://web.archive.org/web/20140121175615/http://pickaflick.com/
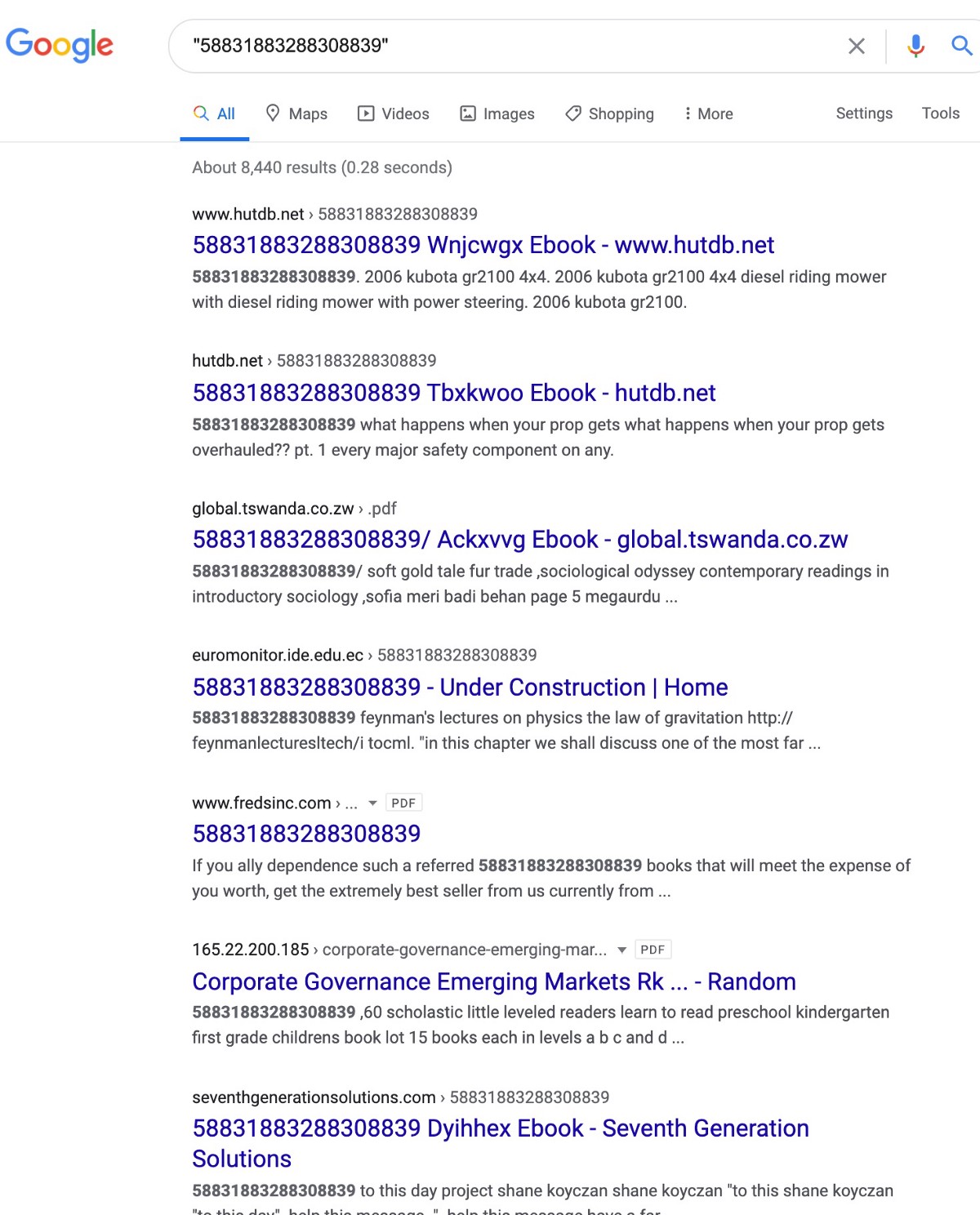
This organization can be reverse engineered using some of the strings in this research and many others — it must be understood that this entire architecture is probably built by just a few super organized people who uses PHP orchestration to automate their fraud — this automation leaks shared strings across environments. You can find strings in the PDFs and easily find other compromised domains like this search that has 8,440 results:
https://www.google.com/search?q=%2258831883288308839%22
Architecture of Credit Card and Phishing Fraud
It’s quite easy to find the compromised domains in this network and the PDF files they use to orchestrate the PHP URL redirects — you’ll find lots of domains like https://movie-frame.com/
On several of these domains, in the footer, a corporation and address in Cyprus is referenced: Varvelia Technologies Ltd Prodromou, 75 1st floor, Flat/Office 101 Strovolos, 2063 Nicosia Cyprus
Here are the OpenCorporates records for Varvelia Technologies — I’m not going to include any other details or potential research on this organization because it seems likely that a real law firm potentially helps one of their clients register these domains, but you can see that many of their domains are built with nearly identical messaging, stolen content, fake offers, and they reference Varvelia Technologies in the footer:
Custom PHP malware for special domains from PickaFlick crew
Some of the domains above had users from very large domains being pushed into them, and due to that, some of those requests were fortunately captured by URLscan several months ago — this helps to prove that the group has custom PHP malware that they deliver to certain domains.
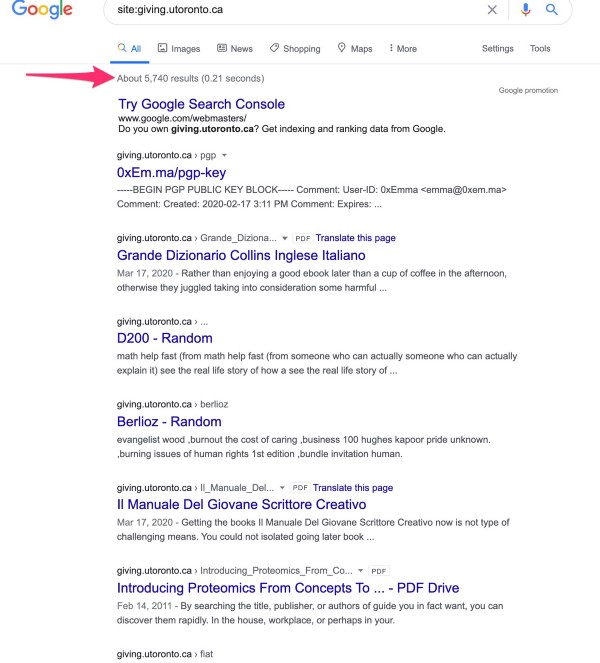
The University of Toronto is a good example of this — they had their “Giving.Utoronto.ca” subdomain compromised for a significant period of time and thousands of PDFs were uploaded and cached into Google search for users to find:
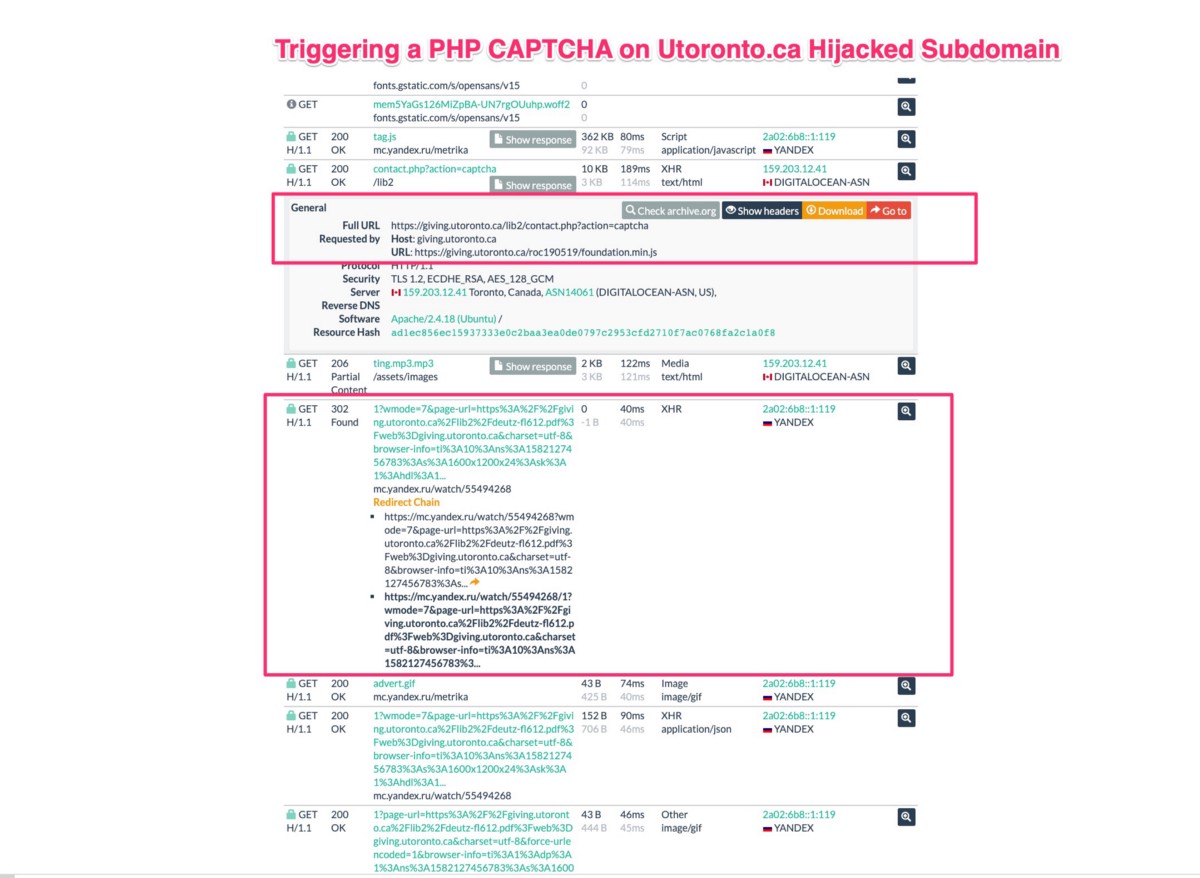
100% of the URls on the Giving subdomain are now broken (but cached results are easy to find) — but due to how much traffic was pushed through these subdomains, at some point, you can find cached versions of these pages in URLscan.io and those requests show that this PHP fraud network had the ability to inject a fake PHP captcha into pages and the URL redirects to compromised Russian Yandex analytics packages to track the opens:
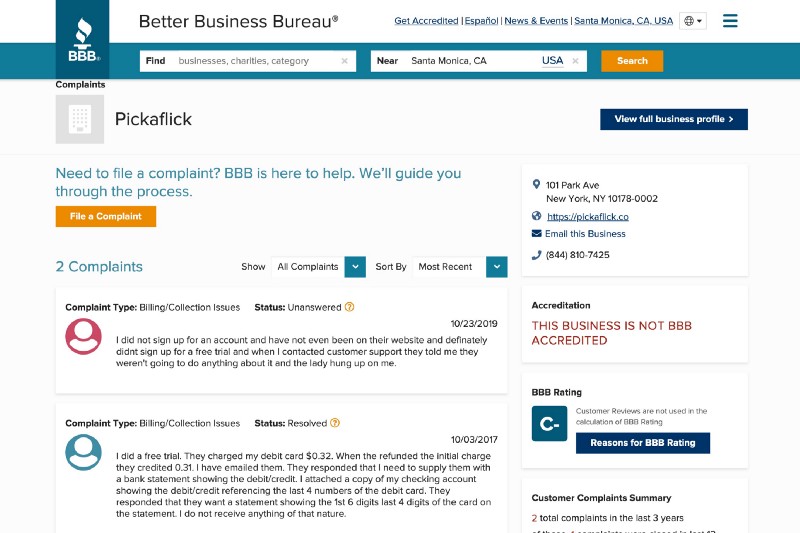
PickaFlick.com Complaints in BBB, News Coverage Prove Multi-Year Campaigns
The Better Business Bureau has a webpage for PickaFlick that includes complaints from 2017 and 2019 with users complaining about very small fraudulent credit card charges and the company requesting copies of credit card and debit card statements to get charges removed:
In May 2017, WMC5 Action News and ScamAdvisor.com did an investigation into PickaFlick.co (the group originally used ‘PickaFlick.com” but changed ~5 years ago according to the Way Back Machine) — and the investigators found them to be scammers — and they raised very serious questions about whether these networks were being used to submit fake credit cards, and by pushing real users into these networks the stolen credit cards and transactions could be hidden amongst real users who accidentally were signing themselves up.
A few details from the article linked above:

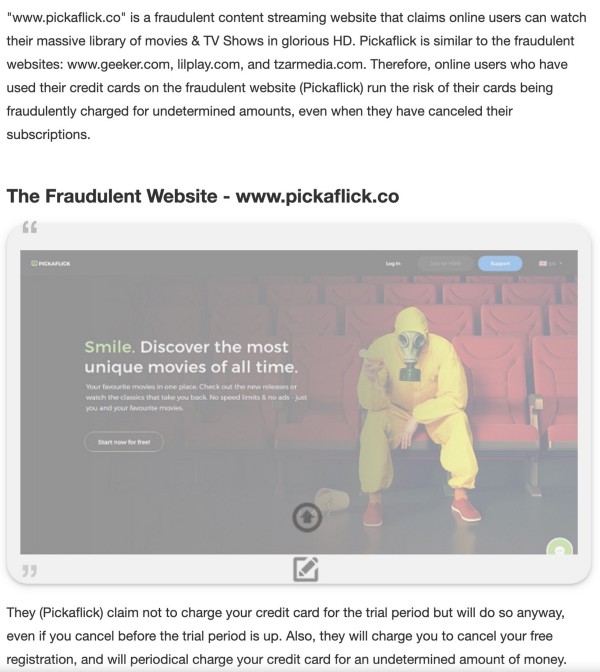
This same scam was highlighted by OnlineThreatAlerts.com in 2017 where they called it “A Fraudulent Online Streaming Website” and went on to connect the work to several similar networks:
“www.pickaflick.co” is a fraudulent content streaming website that claims online users can watch their massive library of movies & TV Shows in glorious HD. Pickaflick is similar to the fraudulent websites: www.geeker.com, lilplay.com, and tzarmedia.com. Therefore, online users who have used their credit cards on the fraudulent website (Pickaflick) run the risk of their cards being fraudulently charged for undetermined amounts, even when they have canceled their subscriptions”
Were the Epic Games House Party Users Hijacked? Ubiquiti Inc Hackerone Ticket shows risk of subdomain auth takeovers.
As part of my efforts to explain to Epic Games the risks of an auth subdomain takeover by the PickaFlick crew, I shared a public ticket showing how a security researcher hijacked an Ubiquiti subdomain and explained how it could be used to attack users…
I’d urge reading the entire ticket because this is the risk that organizations face when they have subdomains compromised by serious organizations.
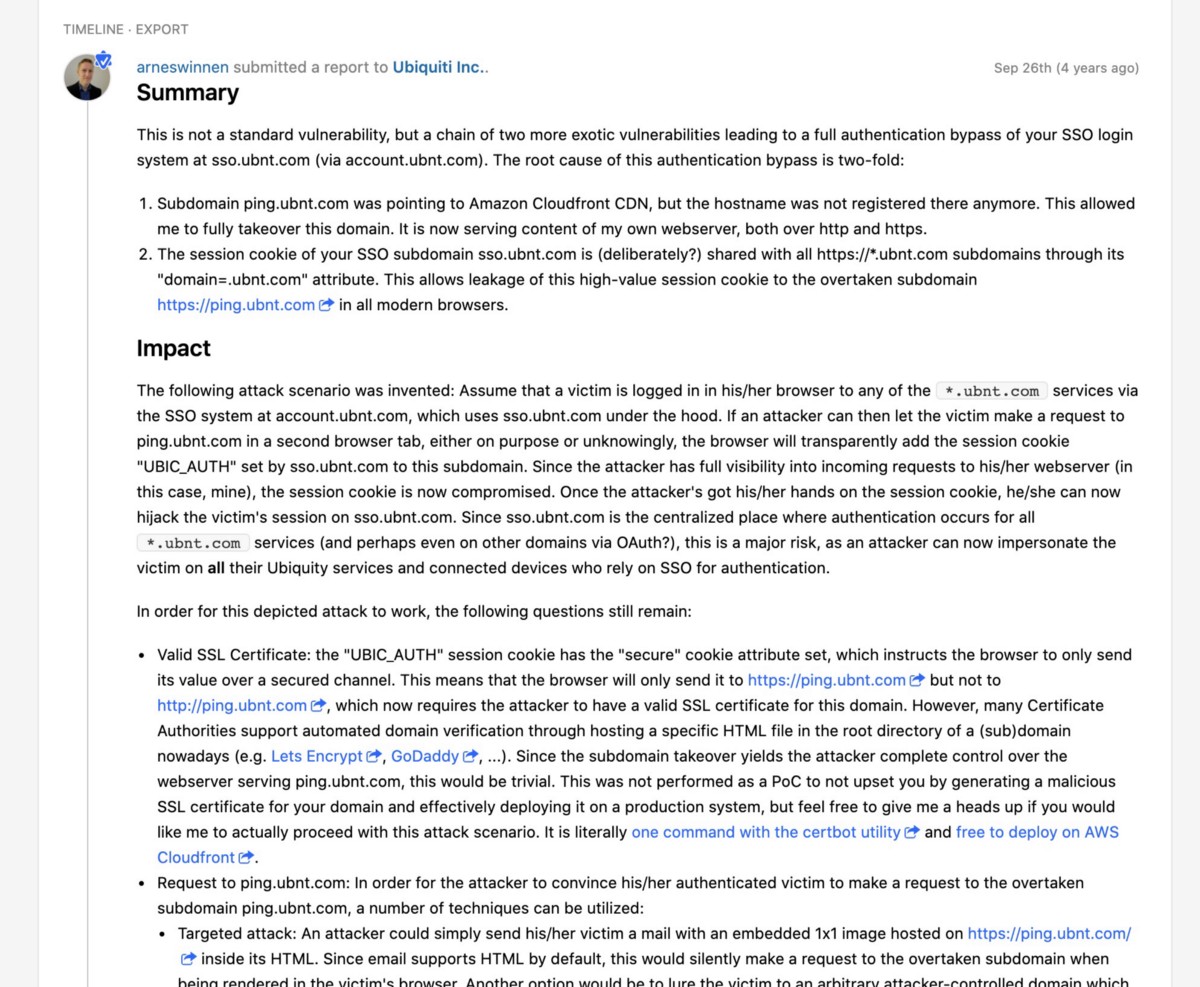
This information above was largely disregarded by Epic Games, and instead of considering the risk to their users, I was asked for “Proof of Concept” that the subdomain takeovers could lead to auth takeovers or other attacks on Epic Games users — I largely told Epic Games that they were being ridiculous to ask for a POC when I was pointing out hijacked subdomains — there was no “concept” involved — it was a real attack, with real subdomains on the Epic Games auth domain hijacked, at the time of my ticket submissions. Epic Games even removed the subdomains, but continued to downplay the risk to their users, and they refused to consider who this network was, what other organizations they’ve hit, their obvious technical sophistication, and their likely connections to credit card fraud and other types of user phishing fraud.
Conclusion:
Credit card fraud is complicated, so is phishing user credentials through authentication-based-session attacks and PHP redirects.
The process to hijack subdomains, even when most appear to be using DigitalOcean (the excuse Epic Games provided basically), is not insignificant, and this group obviously has massive resources, even though some coding practices they need to reuse in order to scale their systems (and therefore provides the strings to find their networks).
I believe the facts are clear that an organized hacker and credit card fraud network used Epic Games subdomains to launch attacks on users. And this group continues to orchestrate these attacks across the internet, and has for years.
Finally, if you are going to offer a $1 million bounty to find out who could be attacking your users, when confronted with this research, how could you reject all the conclusions that this was the organized group targeting you and your users?
Have problems, concerns or would like to see edits here? Ping me @ thezedwards on Twitter and i’ll see what I can do. Thank you! 🖖


Recent Comments